Use Cases from an Expert

TI Lookup from ANY.RUN is a versatile software program for gathering up-to-date intelligence on the most recent cyber threats. One of many easiest methods to disclose its effectiveness is to hearken to from exact security professionals about how they use the service of their daily work.
This time, we requested Jane_0sintan accomplished neighborhood guests analyst and the first ANY.RUN ambassador, for her real-world circumstances of using TI Lookup. Lucky for us, she agreed to share her insights and despatched us a variety of examples, which embrace discovering intel on phishing kits like Mamba2FA and Tycoon2FA.
About Danger Intelligence Lookup
TI Lookup is a searchable hub for investigating malware and phishing assaults and gathering latest cyber danger data. Powered by a big public database of tens of tens of millions of samples analyzed in ANY.RUN’s Interactive Sandbox, it includes quite a few Indicators of Compromise (IOCs), Indicators of Assault (IOAs), and Indicators of Conduct (IOBs), from threats’ neighborhood train to system processes and previous.
The service provides you with intensive search capabilities, allowing you to create personalized requests that operate utterly completely different data elements to dwelling in on specific threats. It presents:
- Quick Outcomes: Searches for events and indicators from the earlier six months take merely 5 seconds on frequent
- Distinctive Data: It includes over 40 styles of danger data, along with malicious IPs, URLs, command line contents, mutexes, and YARA tips
- Big Database: TI Lookup is updated daily with lots of of public samples uploaded to ANY.RUN’s sandbox by a worldwide group of over 500,000 security professionals
Investigating the Mamba2FA Phishing Bundle
Mamba2FA is a phishing package deal that has seen a giant rise over the earlier a variety of months. To investigate this danger and accumulate additional context, we’re in a position to profit from a typical URL pattern usually current in its campaigns. This pattern follows the development {space}/{m,n,o}/?{Base64 string}.
When translating this into an exact query for TI Lookup, we’re in a position to make use of the following search string:
Let’s break down this query:
- Asterisk :
- This wildcard character signifies any character string. It helps broaden our search to include all domains utilized in Mamba2FA assaults, guaranteeing a whole investigation Question Mark (?):
- That’s one different wildcard character that signifies exactly one character or none the least bit. In our case, there are two question marks inside the query. The first one is the wildcard that serves as a stand-in for the characters “m”, “n”, and “o” which is perhaps usually utilized in Mamba2FA URLs. The second question mark is a part of the deal with. To flee it, we use the slash picture c3Y9:
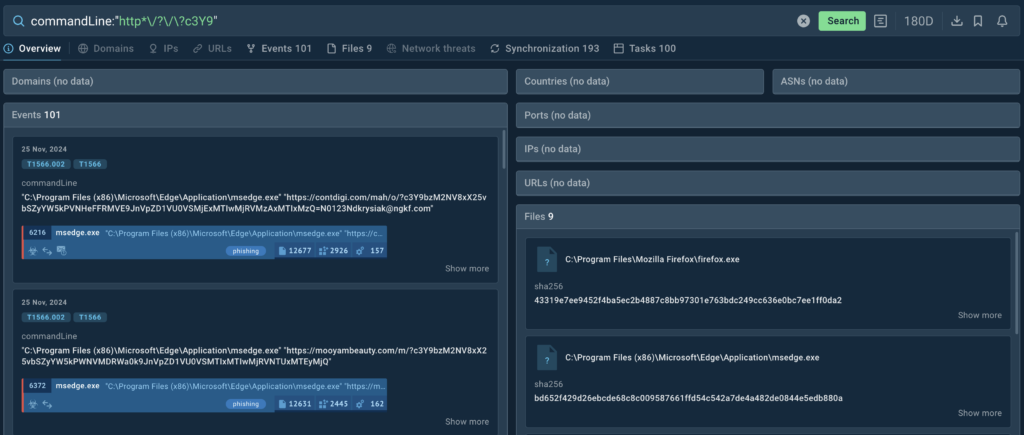
TI Lookup provides danger intel all sandbox courses with the matching command line strings
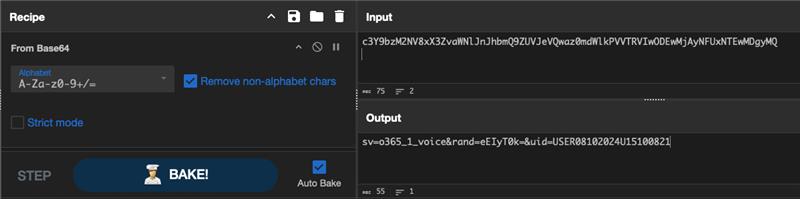
CyberChef recipe used for decoding the URL string
We then can accumulate the entire URLs found and decode the base64-encoded parts to reveal additional knowledge on the assault and extract the itemizing of domains from them.
Investigating the Tycoon2FA Phishing Bundle
Tycoon2FA is one different phishing package deal, which is known for faking Microsoft authentication pages to steal victims’ credentials. With the help of TI Lookup, we’re in a position to accumulate a great deal of intel on its latest samples and wider infrastructure.
- A wonderful comply with for organising queries in TI Lookup is to hyperlink each state of affairs of the query to specific choices of the phishkit:
- If the phishkit hides its pages behind Cloudflare Turnstile, we add a state of affairs for this;
- If there could also be content material materials encryption, we add a state of affairs for the encryption library;
If the phishing internet web page outlets content material materials on a specific CDN (Content material materials Provide Neighborhood), we add a state of affairs for that as successfully.
An occasion of this query constructing methodology for trying Tycoon2FA phishkit assaults could also be seen underneath.
As well-known, certainly one of many signature choices of this danger is the abuse of Cloudflare’s Turnstile challenges as a barrier for automated security choices. For the issue to work, Tycoon2FA plenty the library api.js.
Via the issue, Tycoon2FA moreover plenty one different library, crypto-js.min.js, which it makes use of at later phases of the assault to encrypt its communication with the command-and-control center (C2).[.]The phish package deal moreover accesses elements saved on the dependable space ok4static[.]oktacdn
com and makes use of them to assemble phishing pages designed to imitate Microsoft’s login pages.
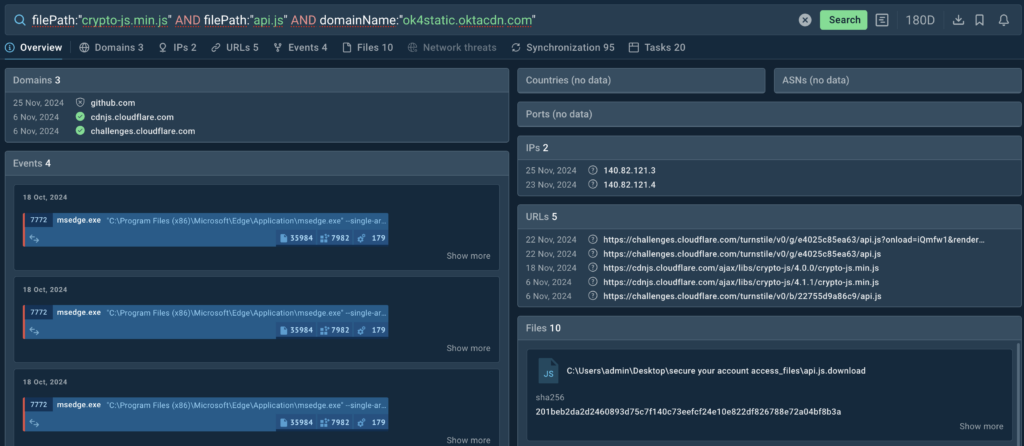
TI Lookup pulls associated danger data from sandbox courses the place every libraries have been detected
In response to the query, the service provides an inventory of matching events current in 20 decrypted sandbox courses over the earlier 180 days. Search queries created on this principle based totally on domains ship additional outcomes on account of they work not solely on decrypted neighborhood courses however moreover require an even bigger number of conditions inside the query. We are going to accumulate the data and take a extra in-depth check out the courses to take a look at assaults as they unfolded in precise time.
Monitoring APT-C-36 Phishing Campaigns
Danger Intelligence Lookup could also be helpful in your investigations into campaigns which is perhaps attributed to superior persistent threats (APTs).
Ponder the occasion of Blind Eagle, additionally known as APT-C-36, which is a bunch that targets Latin America. You probably will be taught additional about their train in ANY.RUN’s article on the threats present in October 2024.
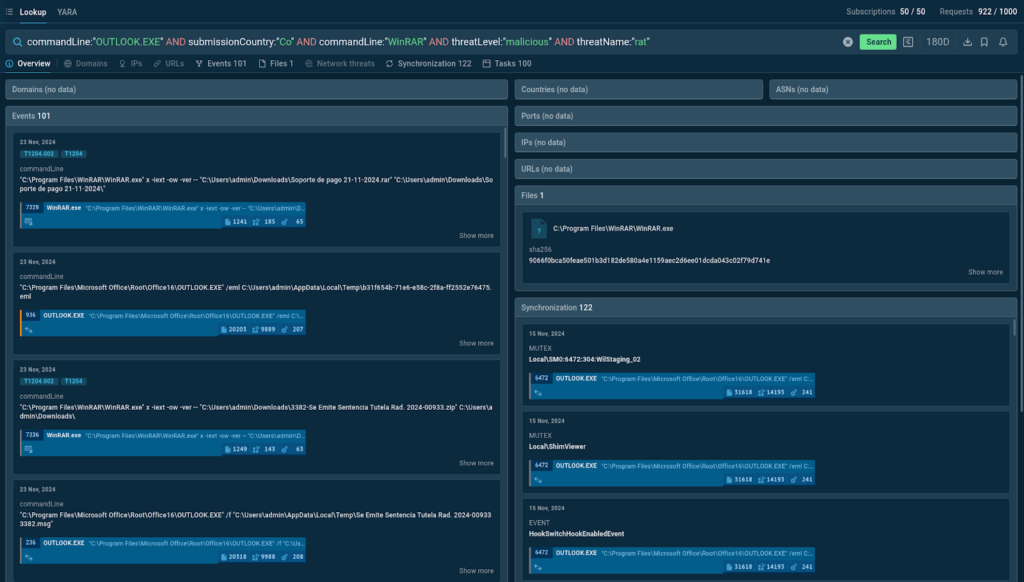
Outcomes for the query investigating APT-C-36
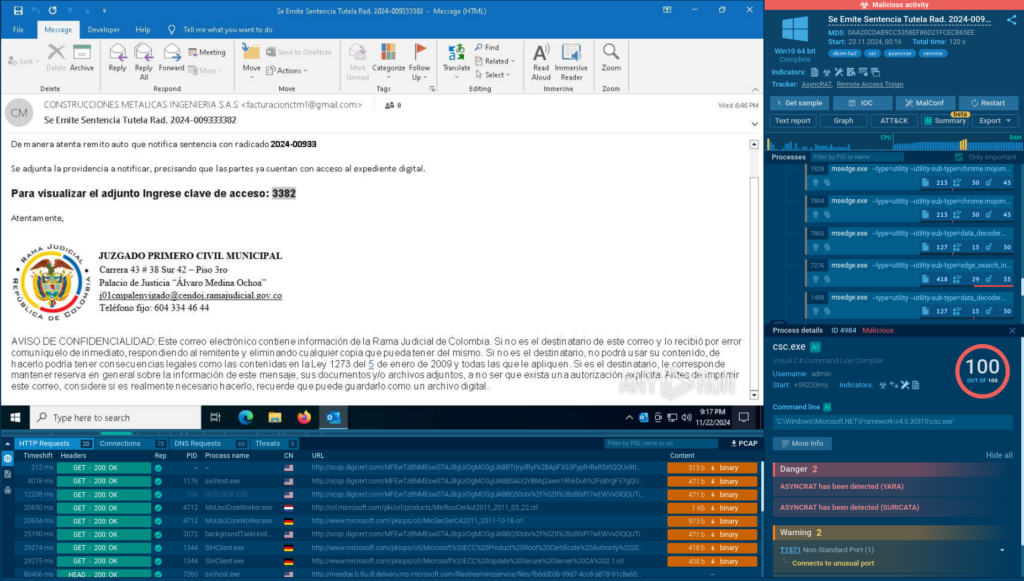
One in every of many phishing emails containing an AsyncRAT payload discovered by the use of TI Lookup
Amongst them, we’re in a position to uncover samples of exact phishing emails belonging to Blind Eagle’s campaigns which have been publicly uploaded to ANY.RUN’s sandbox for analysis by prospects in Colombia.
Determining Phishing Assaults Abusing Microsoft’s Infrastructure
One different useful method to profit from TI Lookup is to proactively evaluation phishing assaults that use dependable belongings to entry content material materials as dependable account login pages do. As an illustration, attackers usually use parts of the Azure Content material materials Provide Neighborhood (CDN), like backgrounds or login sorts.
To go looking out these examples with TI Lookup, you probably can specify the Azure space. Nonetheless, it’s important to filter out non-malicious conditions. You’ll be able to do that by excluding Microsoft’s domains from the query using the NOT operator and setting the danger stage to “suspicious.” You are free in order so as to add exceptions at your discretion do you have to wish to cleanse your query outcomes of unsolicited submissions.
We are going to moreover embrace parameters with empty values. This indicators the system to point all doable outcomes for these parameters.
Together with domainName:”” and suricataMessage:”” will present all domains and Suricata messages found all through sandbox courses that match our query.
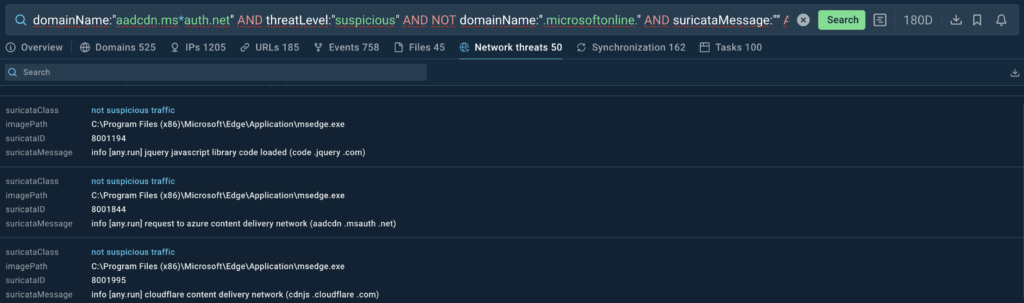
Suricata tips that match our query
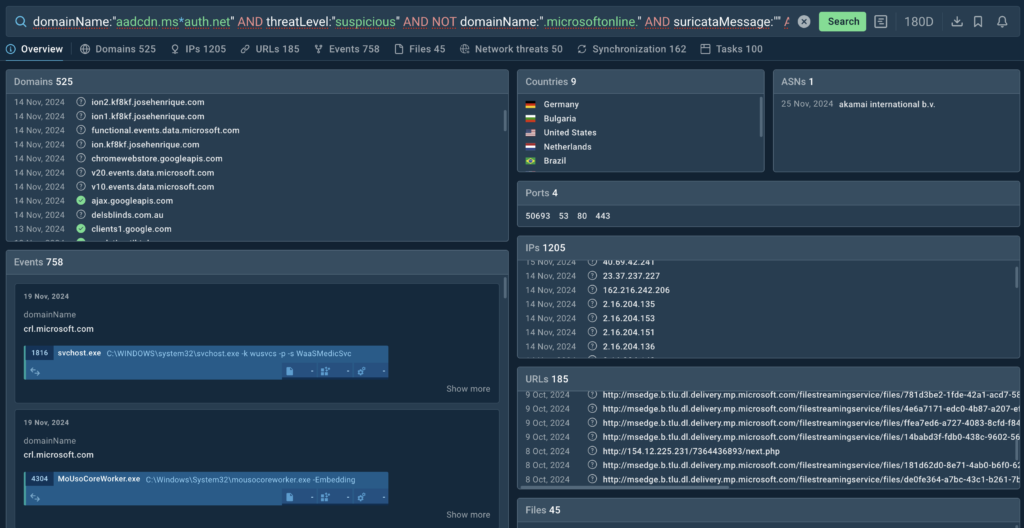
Apart from domains, TI Lookup moreover presents IP addresses and URLs
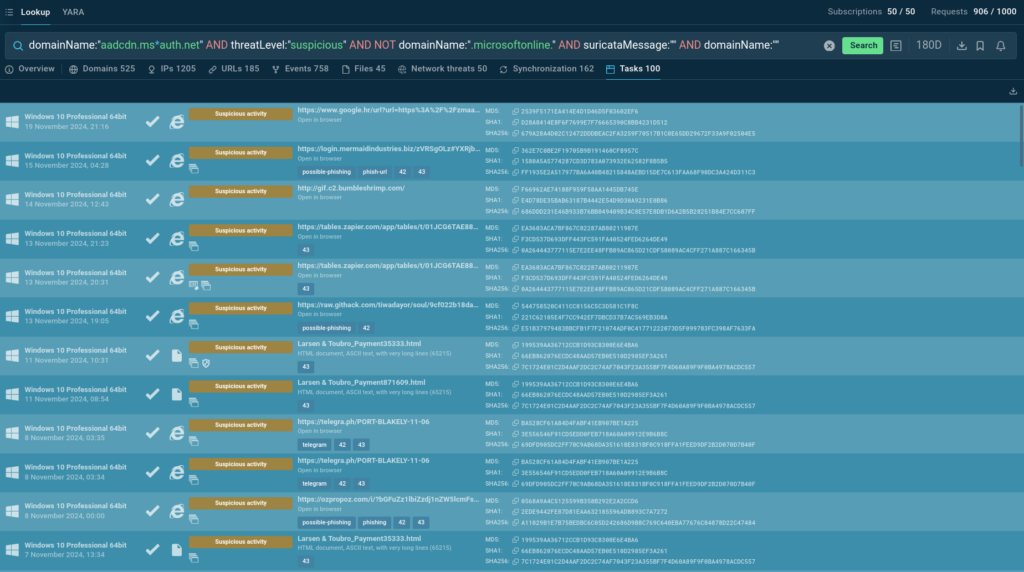
Sandbox courses that match our request
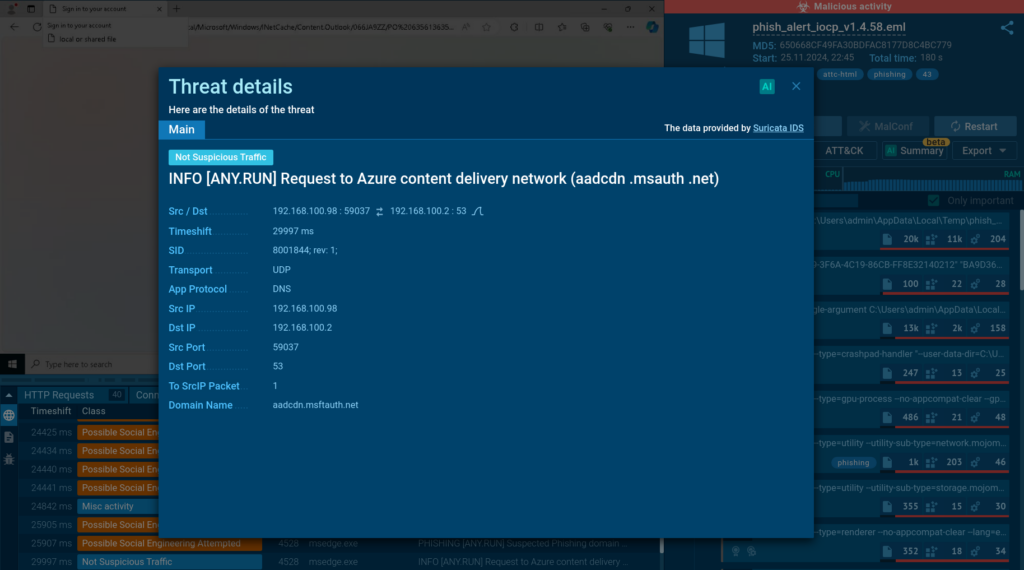
Suricata rule displayed inside the ANY.RUN sandbox
On this session we’re in a position to see a Suricata rule that signifies a request to Azure’s content material materials provide neighborhood.

ANY.RUN cloud interactive sandbox interface
Examine to Monitor Rising Cyber Threats Attempt expert data to gathering intelligence on rising threats with
OF Lookup
Study full data
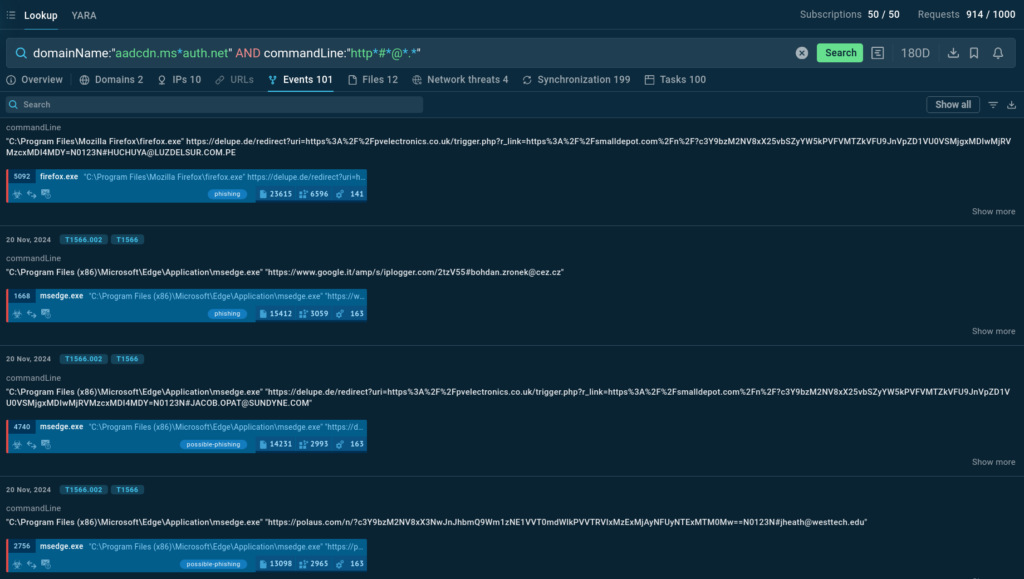
Command line data from logged all through ANY.RUN sandbox courses
Apart from associated sandbox courses, the service returns an inventory of command strains extracted from these, allowing us to see the URLs utilized by attackers that embrace emails of victims.
About ANY.RUN
ANY.RUN’s Danger Intelligence Lookup and YARA Search suppliers allow for actual danger looking out and the extraction of useful insights into current cyber danger tendencies. What’s spectacular is how briskly these scans are—they significantly tempo up the analysis course of, allowing for quick detection of threats and malware.

ANY.RUN writer and neighborhood guests analyst
Jane I’m ANY.RUN ambassador and an precise neighborhood guests numismatist. I moreover love penguins andtortoises
. My motto is to do good and throw it into the ocean.





