How Attackers Use Corrupted Files to Bypass Detection

Not too way back, our analyst crew shared their evaluation proper right into a zero-day assault involving utilizing corrupted malicious recordsdata to bypass static detection applications. Now, we present a technical analysis of this system and its mechanics.
On this text, we’ll:
- Show how attackers corrupt archives, office paperwork, and completely different recordsdata
- Make clear how this system effectively evades detection by security applications
- Current how corrupted recordsdata get recovered by their native functions
Let’s get started.
Sandbox Analysis of a Corrupted File Assault
To first see how such assaults unfold, we’re ready so as to add one among many corrupted filles utilized by attackers to ANY.RUN’s sandbox.
View analysis session.
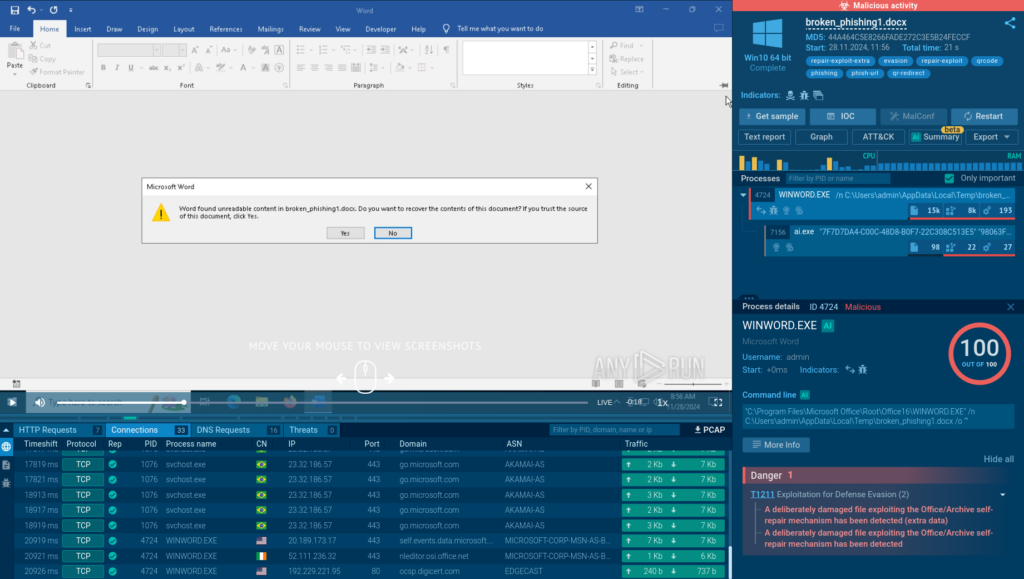
Due to its interactivity, the sandbox lets us simulate an precise state of affairs of individual opening the broken malicious file contained within the file’s corresponding software program.
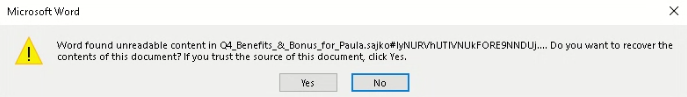
In our case, it’s a docx file. As soon as we open it with Phrase, this technique immediately supplies us the selection to get higher the content material materials of the file and effectively does it.
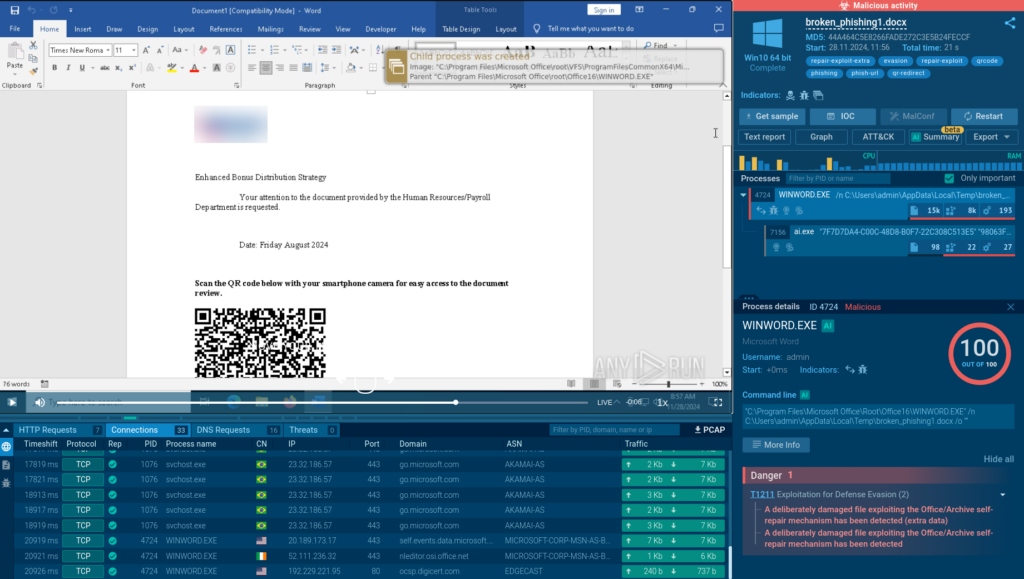
Inside, we uncover a QR code with a phishing hyperlink. The sandbox moreover mechanically detects malicious train and notifies us about this.
How Corrupted Data Bypass Antivirus Software program program and Totally different Automated Choices
Analysis contained within the ANY.RUN sandbox confirmed how a corrupted file will get restored due to Phrase’s built-in restoration mechanismswhich allows us to ascertain its malicious nature.
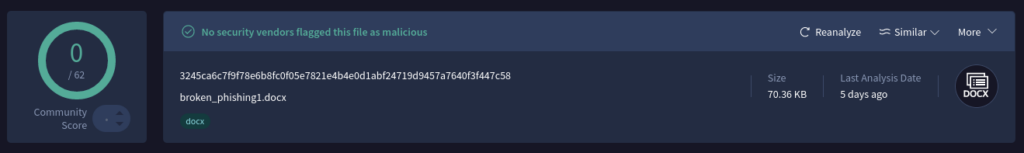
However, if we submit the equivalent corrupted file to VirusTotalwhich supplies verdicts from fairly a number of security choices, we’ll see zero menace detections. The question is why?
The reply is straightforward: most antivirus software program program and automated devices are not equipped with the restoration efficiency that is current in functions, comparable to Phrase. This prevents them from exactly determining the form of the corrupted file, resulting in a failure to detect and mitigate the menace.
Docx simply is not the one file format utilized by attackers. There are moreover corrupted archives with malicious recordsdata insidewhich merely bypass spam filters because of security applications can’t view their contents ensuing from corruption.
As quickly as downloaded onto a system, devices like WinRAR merely restore the damaged archivemaking its contents obtainable to the sufferer.
Now, let’s see how exactly it actually works on a technical stage.
Technical Analysis of a Corrupted Phrase Doc
The Building of a Phrase Doc
As a result of the mid-2000s, office paperwork (OpenOffice.org 2.0 — launched in 2005) have been structured as archives containing the doc’s content material materials.
Throughout the image beneath, you presumably can see the development of a Phrase doc.
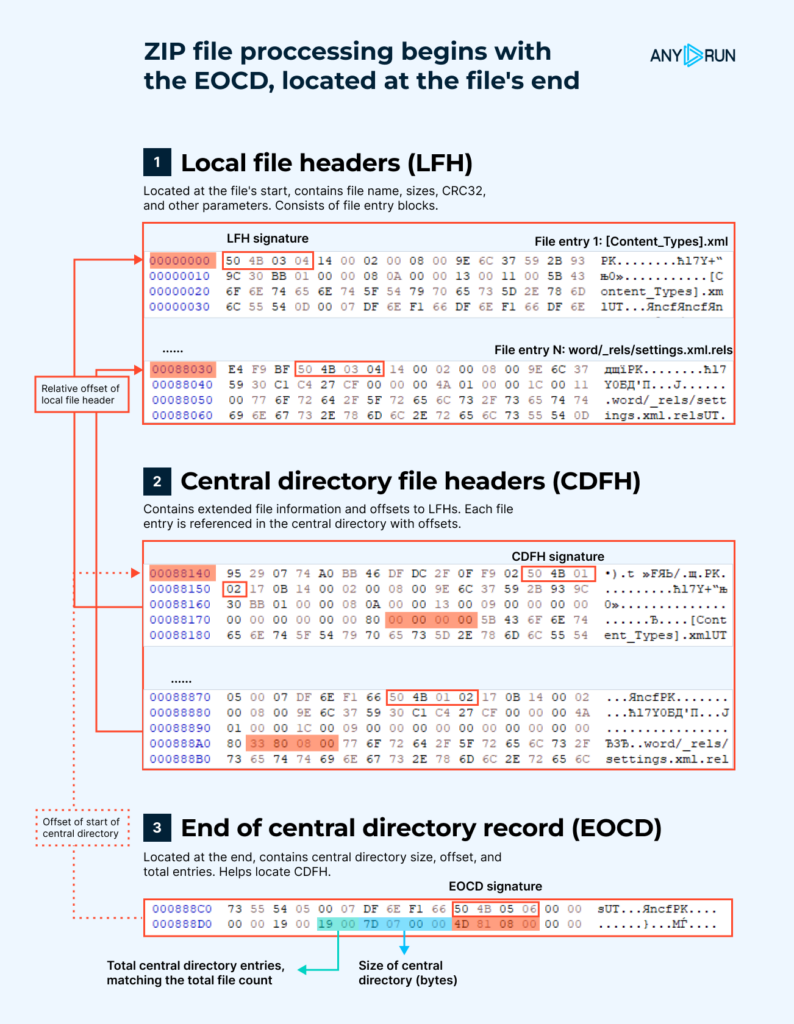
As we’re in a position to see, all buildings inside this archive are interconnected, and this relationship begins from the highest.
On the end of the archive, there is a development generally known as the End of Central Itemizing Report (EOCD). This development incorporates particulars concerning the scale of the Central Itemizing File Header (CDFH), its offset, and the complete number of entries inside the archive. This development helps discover the CDFH.
The CDFH duplicates the data saved inside the Native File Header (LFH) and the offsets to it. However, this development would not comprise the compressed data itself nonetheless barely represents a hierarchy of recordsdata all through the archive. This part of the development allows you to uncover the LFH of each file inside the archive.
The LFH is taken into consideration the header for each file inside the archive. It incorporates very important data such as a result of the file title, compressed and uncompressed sizes, CRC32 checksum, and completely different parameters.
The compressed data is positioned after the header.
How the File Building Can Be Manipulated by Attackers
As confirmed inside the image above (Decide 1), the archive is structured backward, starting with the highest, whereas all parts are linked collectively.
This has led us to verify three completely completely different hypotheses (Decide 2):
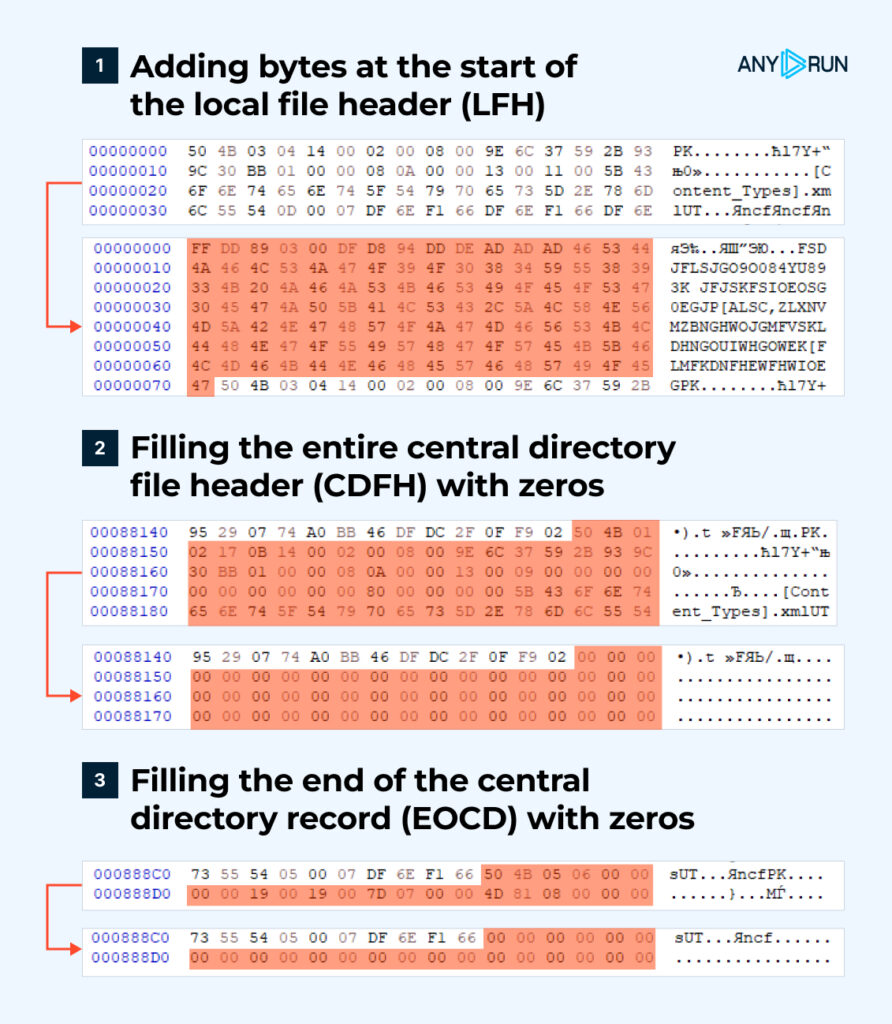
1. Can Phrase or an archiving program get higher and effectively open a file if additional data is added to the beginning of the archive?
2. Can Phrase or an archiving program get higher and effectively open a file if we corrupt the linking between the parts and delete the CDFHwhich does not comprise the file data itself?
3. Can Phrase or an archiving program get higher and effectively open a file if we corrupt the linking between the parts and erase the EOCDwhich is a crucial part of the restoration course of?
You’ll see the outcomes of our hypothesis testing inside the desk beneath.
|
Phrase |
ZIP |
|
|---|---|---|
|
Hypothesis 1 |
Success |
Fail (the file is no longer an archive) |
|
Hypothesis 2 |
Success |
Success |
|
Hypothesis 3 |
Success (due to undamaged Native File Headers) |
Success (due to undamaged Native File Headers) |
All through our hypothesis testing, we’ve made various noteworthy observations:
1. For minimal restoration of a Phrase doc, the subsequent recordsdata are necessary:
[Content_Types].xml,
Phrase/doc.xml,
phrase/_rels/doc.xml.rels,
_rels/.rels;
These comprise important information referring to the relationships between elements and kind the standard file hierarchy required for Phrase to interpret the doc.
2. A ZIP archive with corrupted Native File Headers will solely current the file development. The exact file content material materials will doubtless be empty.
3. If the highest part of the ZIP file is damaged, the archiving software program program and Phrase will attempt to make use of an alternate restoration approach: by leveraging intact Native File Headers.
Our findings show that Phrase is additional resilient to file corruption than ZIP. Whereas Phrase effectively recovered recordsdata with corrupted CDFH, EOCD, and even when random bytes have been added to create a non-existent LFH developmentZIP failed inside the first hypothesis, the place random bytes have been added to the beginning of the file.
Why Security Packages Fail to Study Corrupted Data
Security applications attempt to set up file kinds, along with via the usage of Magic Bytes in File Headers. Throughout the case of office paperwork and ZIP archives, because of the file efficiently begins from the highest, we’re in a position to corrupt the archive development and magic bytesmaking it robust for detection applications to ascertain the file kind.
This ends in the shortcoming to unpack and study the contents.
Keep in mind this piece of email with a corrupted Phrase doc.
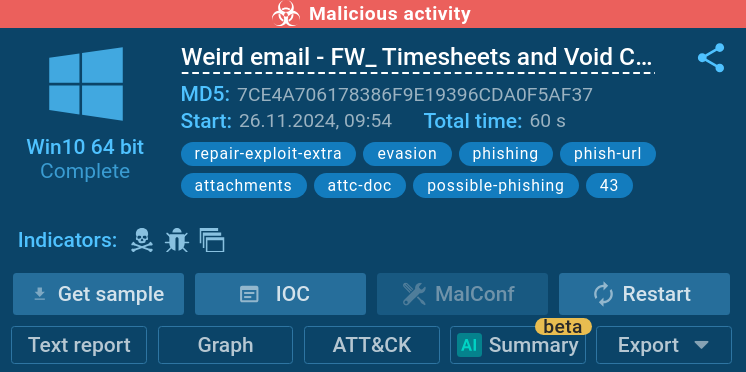
The sandbox as quickly as as soon as extra has no disadvantage detecting the menace, returning a “malicious train” verdict.
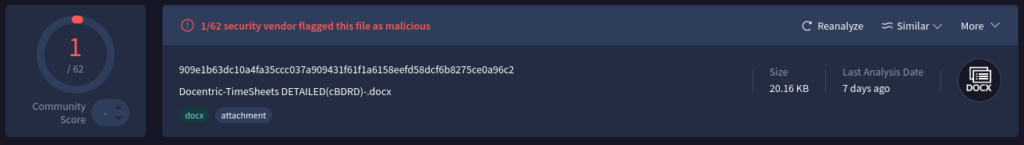
Nonetheless, when run in VirusTotal, practically zero menace detections come once more for this file.

Examine to analysis cyber threats
See an in depth data to using ANY.RUN’s Interactive Sandbox for malware and phishing analysis
Study full data
Conclusion
Our analysis revealed a vulnerability in doc and archive buildings. By manipulating specific components identical to the CDFH and EOCD, attackers can create corrupted recordsdata which could be effectively repaired by functions nonetheless keep undetected by security software program program. Due to this, we face a state of affairs when security applications have not however developed a clear logic for detecting such assaults, exposing the security of their clients.
About ANY.RUN
ANY.RUN helps better than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that consider every Residence home windows and Linux applications. Our menace intelligence merchandise, TI Lookup, YARA Search and Feeds, will let you uncover IOCs or recordsdata to be taught additional regarding the threats and reply to incidents sooner.
With ANY.RUN you presumably can:
- Detect malware in seconds
- Work along with samples in precise time
- Save time and cash on sandbox setup and maintenance
- Report and analysis all aspects of malware habits
- Collaborate collectively along with your crew
- Scale as you need
Try ANY.RUN’s Interactive Sandbox and Danger Intelligence merchandise completely free →







