How to Collect Indicators of Compromise in the ANY.RUN Sandbox

Gathering Indicators of Compromise (IOCs) is important to determining and responding to threats. IOCs are gadgets of forensic information that point to potential malicious train, serving to you detect, look at, and forestall cyberattacks.
With ANY.RUN, you presumably can collect all types of IOCs, offering you with an entire picture of any danger.
Let’s dive into the kinds of IOCs you presumably can collect in ANY.RUN’s Interactive Sandbox and the place to go looking out them.
File System Indicators
Important Objects
The Important Object is among the many most necessary elements when analyzing malware contained within the ANY.RUN sandbox. This refers again to the key file that was loaded for analysis.
While you’ve initiated a sandbox analysis session, merely click on on on the file establish located throughout the upper-right nook of the show display.
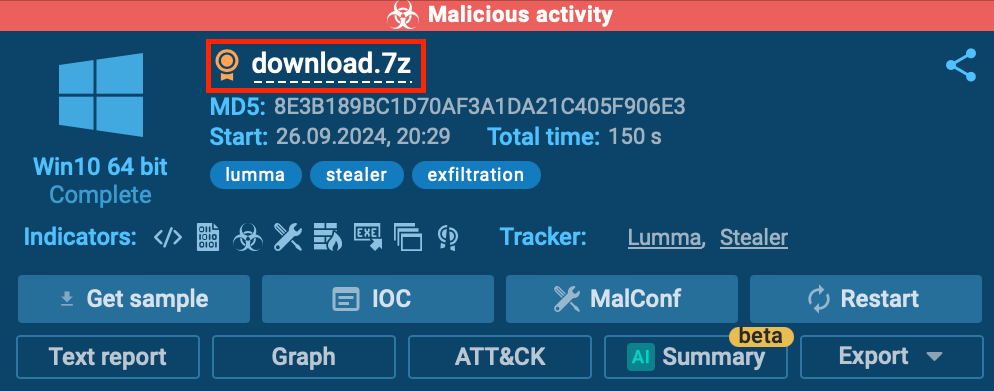
This movement gives you quick entry to the Important Object IOCs, which embrace main particulars harking back to file paths, hashes, and additional.
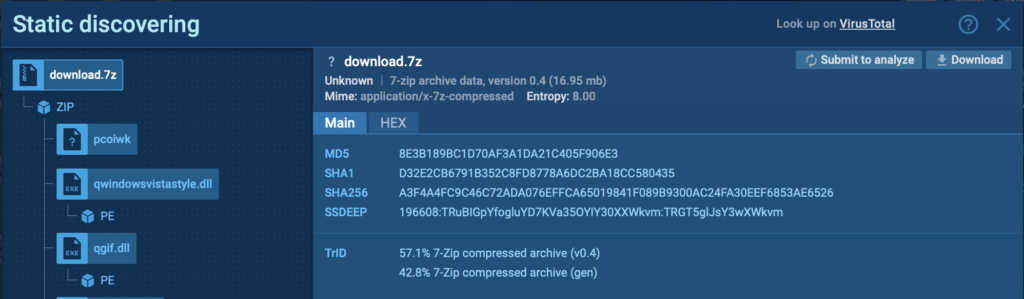
Dropped Executable Info
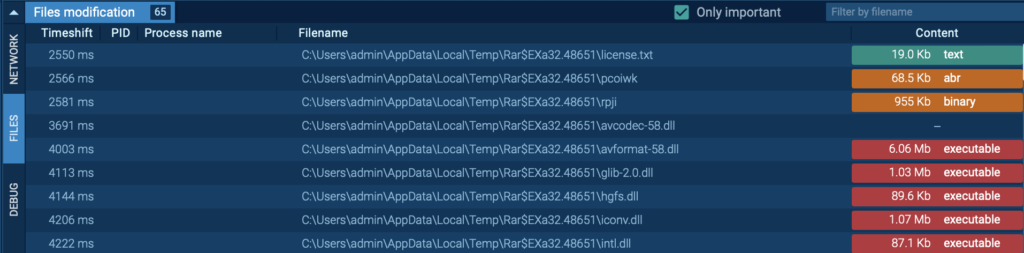
All recordsdata dropped in the middle of the malware’s execution are confirmed throughout the bottom panel beneath Info. This house demonstrates exactly what recordsdata the malware generated or modified, serving to you monitor its propagation all through the system.
Group Indicators
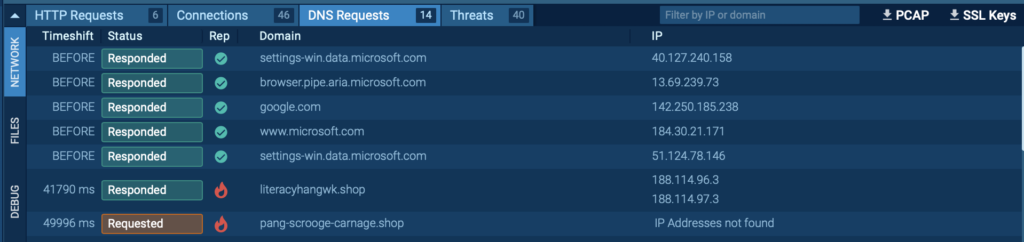
Domains (DNS Requests)
Domains that the malware makes an try and entry would possibly allow you to trace its communication with exterior servers, harking back to command-and-control (C2) infrastructure.
Yow will uncover these IOCs beneath Group → DNS Requests throughout the bottom panel of the sandbox interface.
By analyzing the DNS requests, you’ll get a clearer view of how the malware interacts with distant hosts, normally revealing malicious infrastructure or completely different indicators that will assist in further danger investigation.
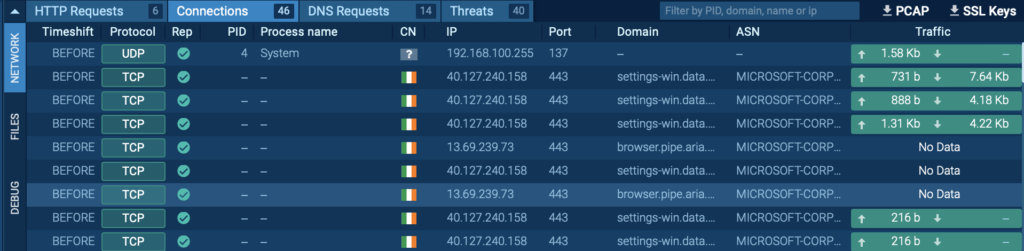
Connections
The malware’s full of life connections could also be observed beneath Group → Connections.
This perform lets you monitor the malware’s communication channels, monitoring its interactions with command-and-control (C2) servers or completely different suspicious IP addresses.
Analyzing these connections lets you set up information exfiltration routes or pinpoint the place the malware is sending information.
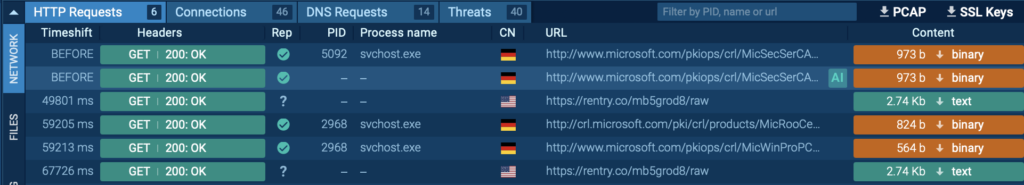
HTTP/HTTPS Requests
HTTP and HTTPS requests initiated by the malware are logged beneath Group → HTTP Requests. That’s important for determining malicious websites or exterior servers the malware connects to.
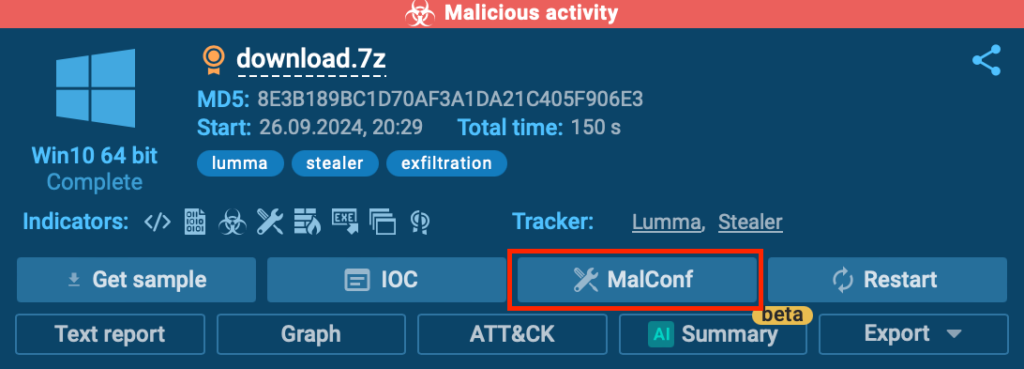
Malware Configurations
Inside the ANY.RUN sandbox, you presumably can accumulate IOCs notably associated to malware configurations by clicking the MalConf button located throughout the larger correct nook of the show display.
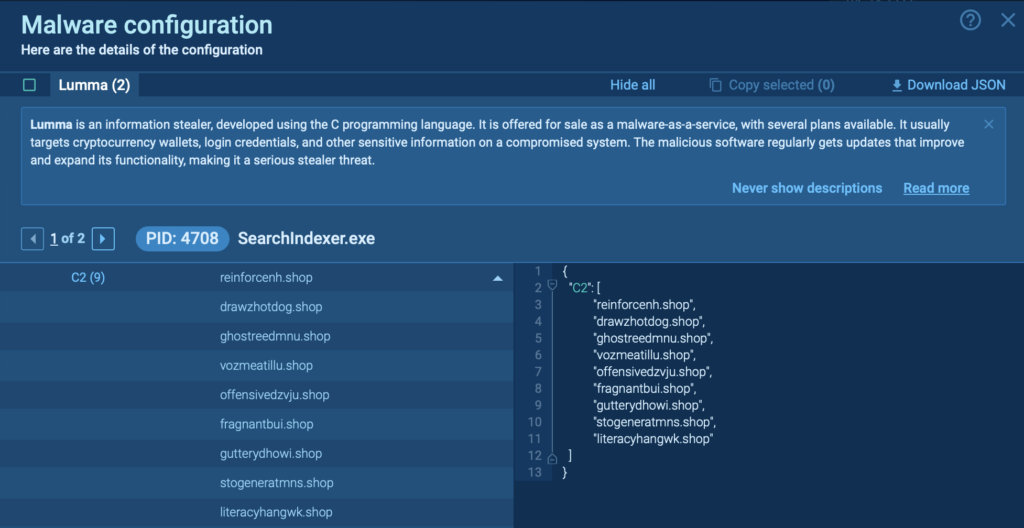
The perform notably pulls IOCs from to the malware’s configurations, harking back to URLs, file hashes, and domains, providing key insights which may be important for extra in-depth investigation and reporting.
Centralized IOC Window
Chances are you’ll merely entry all the important indicators throughout the IOC window.
Merely hit the IOC button located throughout the top-right nook, and in addition you’ll instantly purchase entry to most likely probably the most very important IOCs collected all by means of the analysis—whether or not or not they arrive from Static Analysis or Malware Configurations.
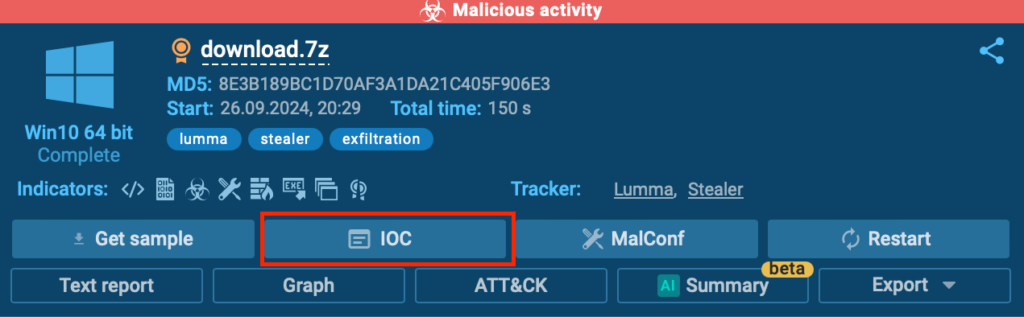
This window saves time and ensures that every one very important information is conveniently organized in a single place for less complicated overview.
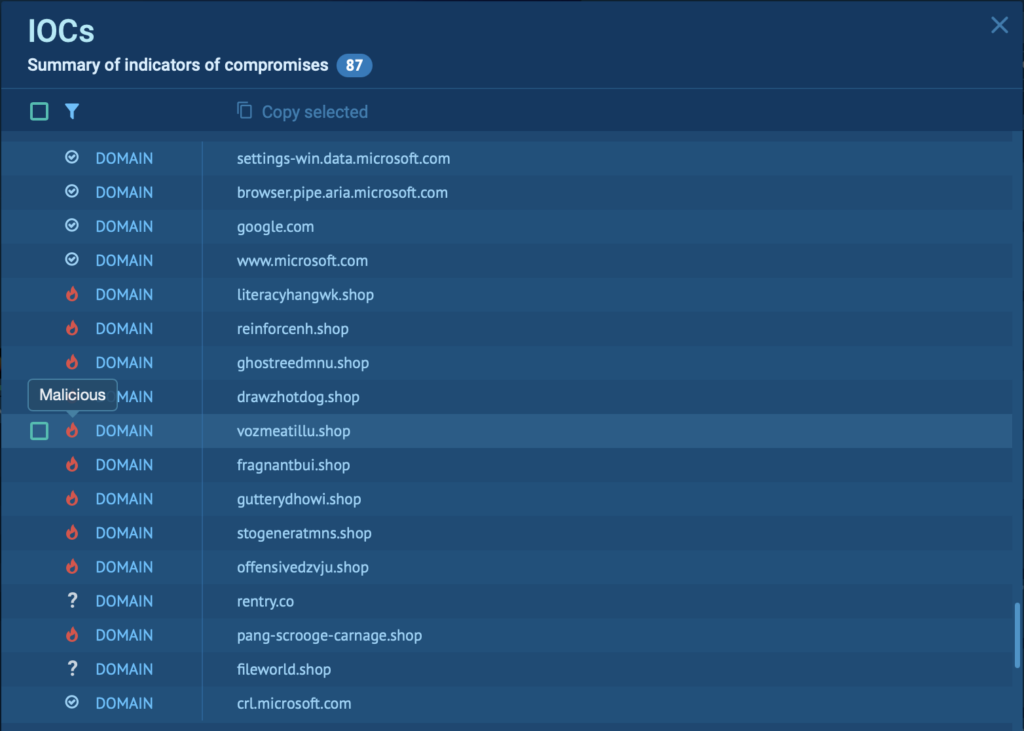
The IOC window is straightforward to navigate because of the simple dropdown menu.
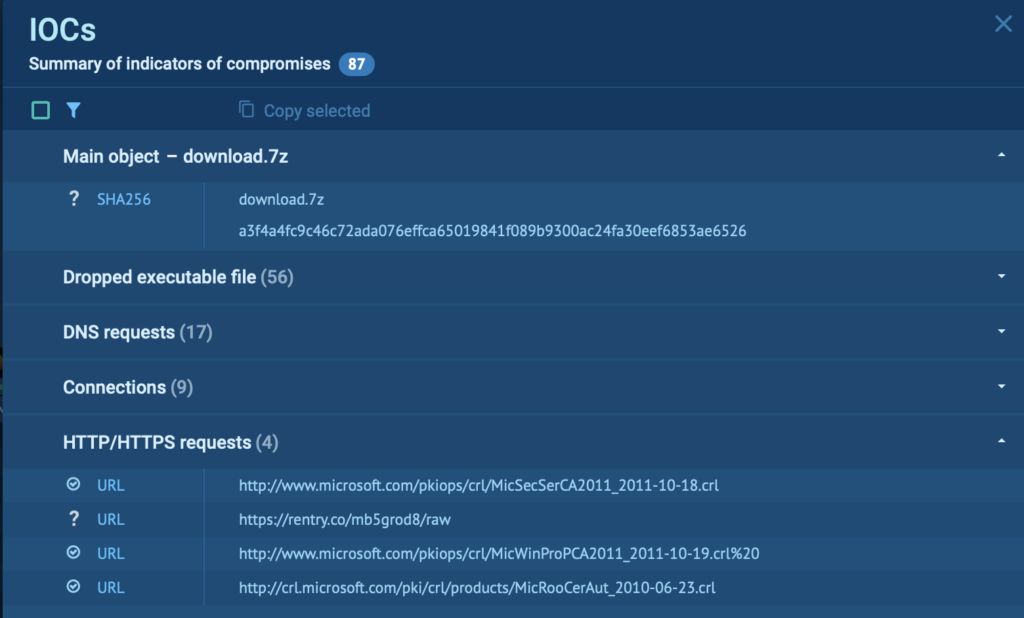
Chances are you’ll shortly filter and prepare IOCs. Plus, copying the chosen indicators in your critiques or further analysis is barely a click on on away, making the whole course of unpolluted and setting pleasant.
About ANY.RUN
ANY.RUN helps higher than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that target every Residence home windows and Linux applications. Our danger intelligence merchandise, TI Lookup, Yara Search and Feeds, present you how one can uncover IOCs or recordsdata to review additional regarding the threats and reply to incidents sooner.
With ANY.RUN you presumably can:
- Detect malware in seconds
- Work along with samples in precise time
- Save time and cash on sandbox setup and maintenance
- File and analysis all factors of malware conduct
- Collaborate alongside together with your crew
- Scale as you need
Request free trial →





