Search Operators and Wildcards for Cyber Threat Investigations

Discovering information on explicit cyber threats in an unlimited amount of data will likely be tough. Menace Intelligence Lookup from ANY.RUN simplifies this job with wildcards and operators that give you the pliability to create versatile and precise search queries.
Let’s try how it’s best to use them to determine and accumulate intel on malware and phishing assaults additional efficiently.
About Menace Intelligence Lookup
Menace Intelligence (TI) Lookup is a fast and setting pleasant instrument designed to simplify cyber threat investigations. It permits for versatile searches for Indicators of Compromise (IOCs), Indicators of Assault (IOAs), and Indicators of Conduct (IOBs).
TI Lookup provides entry to a persistently updated database of threat info collected from tens of hundreds of thousands of public malware and phishing samples analyzed in ANY.RUN’s Interactive Sandbox.
Each sandbox session incorporates detailed logs of system and neighborhood events that occur whereas a threat is executing. By wanting by this whole info, you can merely uncover connections between seemingly unrelated gadgets of knowledge and tie them to a specific threat.
Proper right here’s how TI Lookup may assist you to and your group:
- Study Threats Shortly: Acquire in depth and in-depth information on rising and continual cyber threats with over 40 search parameters (e.g. threat names, command traces, registry logs, and lots of others.).
- Get hold of Precise-Time Updates: Preserve educated with real-time updates on outcomes in your search queries.
- Enrich Menace Intelligence: Get associated context, indicators, and samples manually analyzed by threat analysts.
Search Operators in TI Lookup
Search operators are vital devices in TI Lookup that help you to combine quite a few indicators to refine your search queries efficiently. They act as logical connectors that permit you to specify the relationships between fully totally different conditions in your search and acquire higher flexibility and precision in your searches.
TI Lookup helps logical operators like AND, OR, and NOT, along with grouping with parentheses. Let’s take a greater check out each of these.
AND
What it does
The AND operator helps you combine quite a few conditions.
Why use it
AND is good for narrowing down your search to hunt out threats by along with as many distinctive indicators as potential.
It is equally environment friendly in situations when you might have quite a few absolutely disparate artifacts, like an IP deal with and a mutex, and must hyperlink them to a particular threat.
Occasion
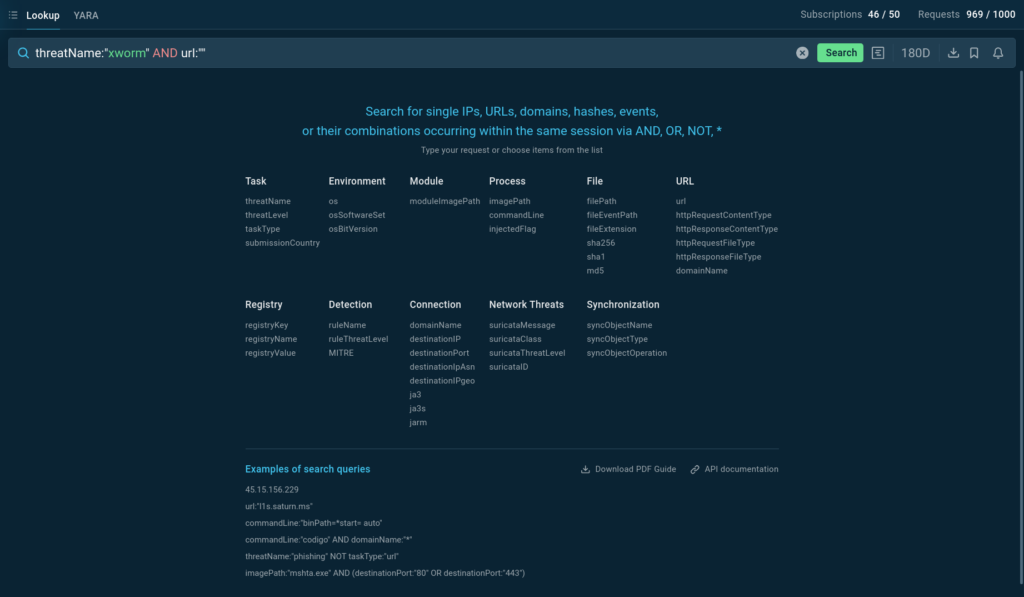
This query is designed to hunt for sandbox intervals the place every thum[.]io and emblem[.]clearbit[.]com domains have been found.
- Thum[.]io is a real-time website screenshot generator.
- emblem[.]clearbit[.]com is a service for fetching agency logos.
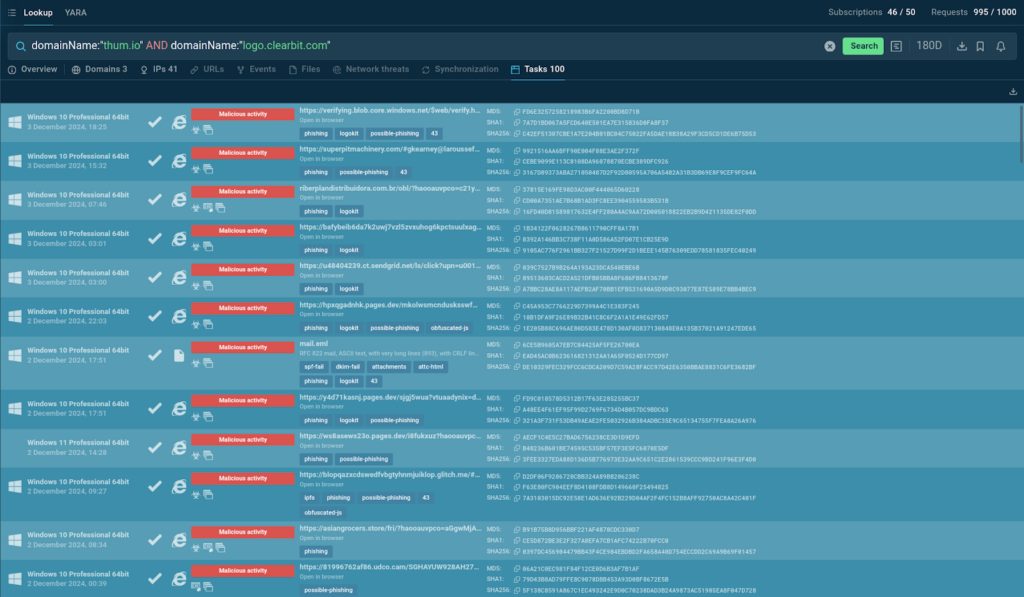
TI Lookup practically instantly provides outcomes: associated IP addresses and sandbox intervals, all of which embrace a “malicious train” label and a “phishing” tag.
We are going to click on on any session of our curiosity to analysis the chance further.
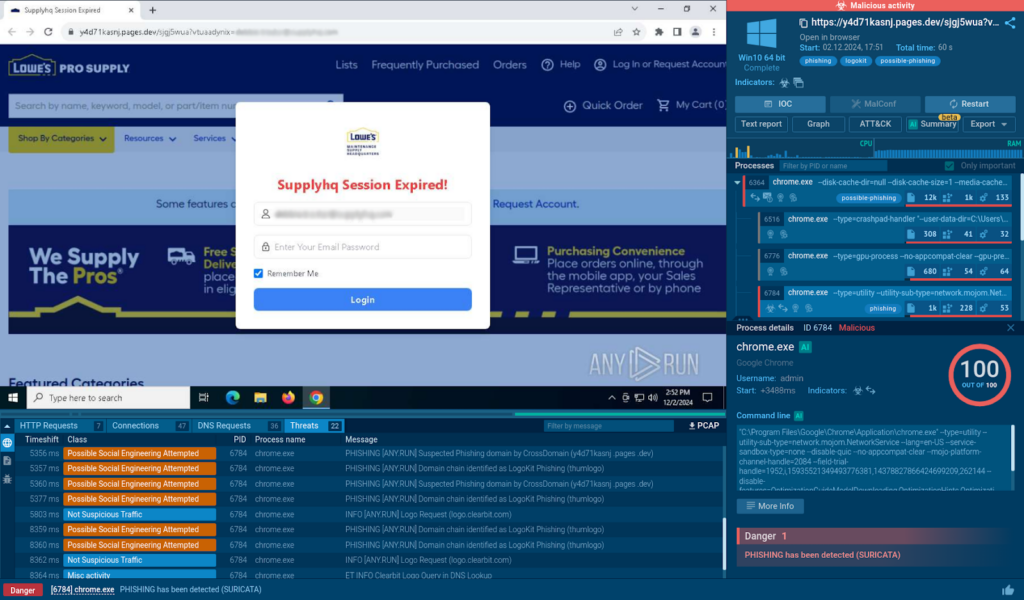
By reviewing the analysis report, we’re capable of spot that this could be a cyber assault which makes use of thum[.]io to dynamically generate phishing pages with the backgrounds of a website that coincides with that of the sufferer. Attackers moreover use emblem[.]clearbit[.]com in order so as to add corresponding agency logos to make faux pages appear additional legit.
OR
What it does
The OR operator helps return matches the place a minimum of certainly one of many given conditions is found.
Why use it
OR is nice in situations if you find yourself undecided which thought of certainly one of two indicators is expounded to a threat. It is also useful for broadening your search to include outcomes the place every indicators are found, nevertheless primarily collectively within the equivalent session.
Occasion
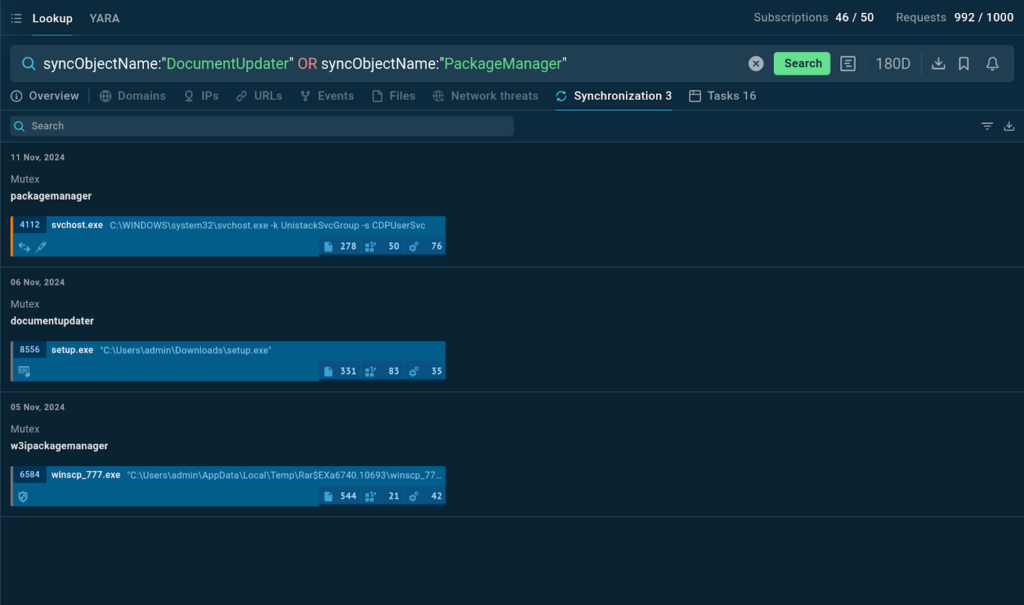
It searches for entries the place the synchronization object establish is “DocumentUpdater” or “PackageManager”. For many who’re investigating a threat that may be using each of these sync objects, this query ensures you don’t miss any associated information.
TI Lookup reveals that the synchronization objects are mutexes and provides sandbox intervals the place they’ve been beforehand discovered.
NOT
What it does
The NOT operator excludes outcomes that match the specified scenario.
Why use it
NOT is beneficial every time you want to refine your search and see sandbox intervals the place no certain merchandise, like a website or file establish, was observed.
Occasion
This query is looking for phishing samples nevertheless excludes any entries the place the preliminary submission uploaded to the ANY.RUN sandbox was a URL.

It helps us uncover e mail, html, zip, exe, or totally different types of info, utilized in phishing assaults.
Parentheses ()
What they do
Parentheses group conditions and administration the order of operations to ensure they’re processed throughout the order you specify.
Why use them
Parentheses are vital for creating difficult queries, making your search additional precise and environment friendly.
Occasion
This query searches for sandbox intervals and their related info the place the tactic “mshta.exe” was observed along with connections to trip spot ports of each 80 or 443. The parentheses guarantee that the OR scenario is processed first, making the search additional precise.
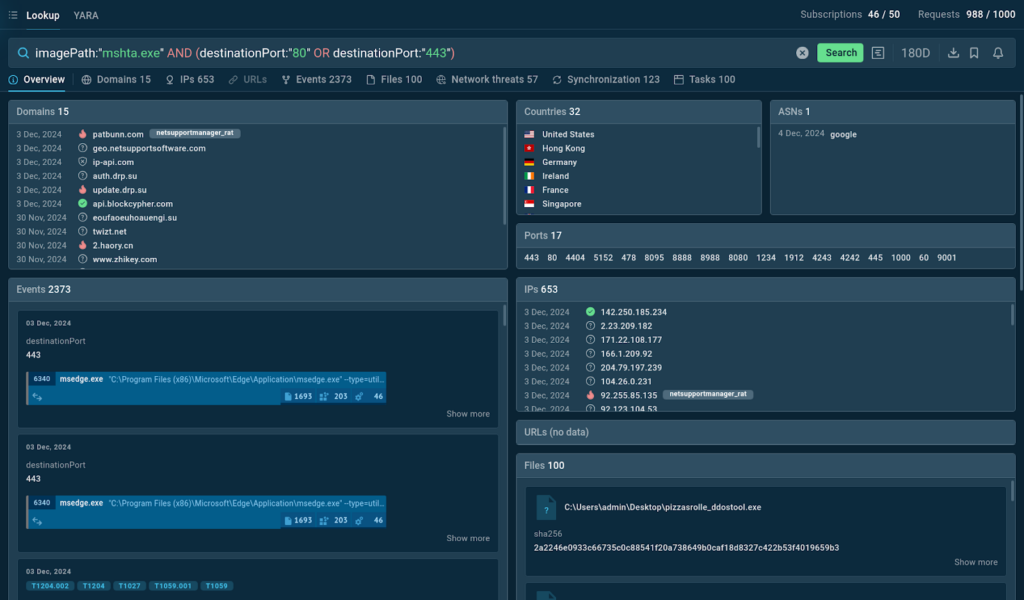
TI Lookup returns a wealth of threat info related to our query. A couple of of the outcomes embody malicious domains and IP addresses, along with an inventory of neighborhood threats detected all through analyses.
Wildcard Characters
Wildcards in TI Lookup act as placeholders in your search queries. They will characterize a number of kinds of character sequences.
Asterisk
What it does
The asterisk represents any number of characters, along with none. This suggests it might properly stand in for zero, one, or quite a few characters. The asterisk is added by default at the start and end of each query, so that you simply typically there’s no need to enter it manually. Why use it
The asterisk is good for everytime you’re undecided regarding the exact content material materials of a string. It helps you uncover matches even when there are unknown parts or certain variations in your query string. Occasion
This query searches for sandbox intervals the place the command line consists of paths to explicit script info located throughout the C:UsersPublic itemizing. The scripts ought to be of kinds .vbs (Seen Basic Script), .bat (Batch file), and .ps1 (PowerShell script).
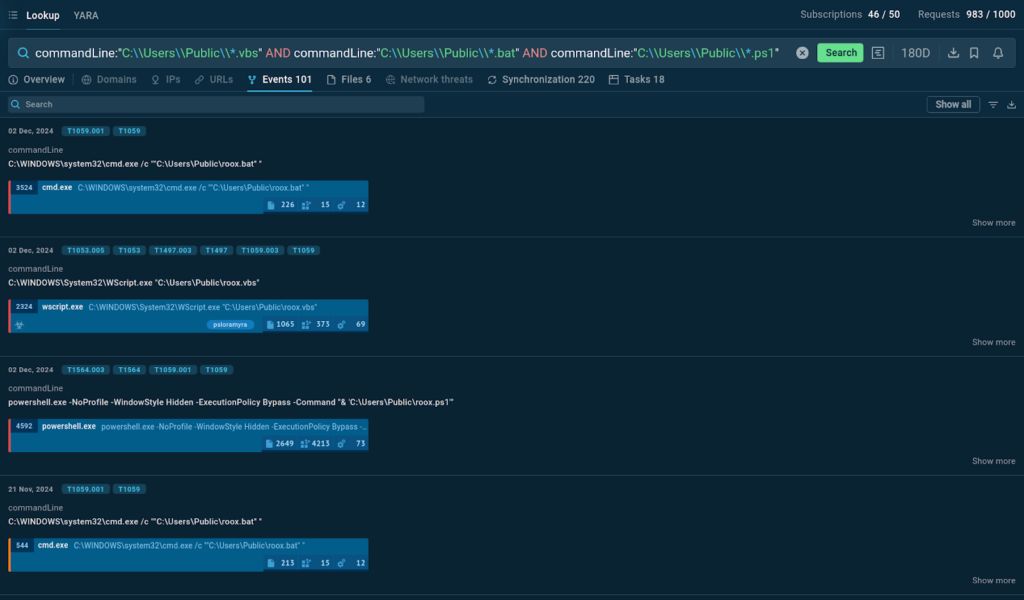
Asterisks are used to alternate any string of characters
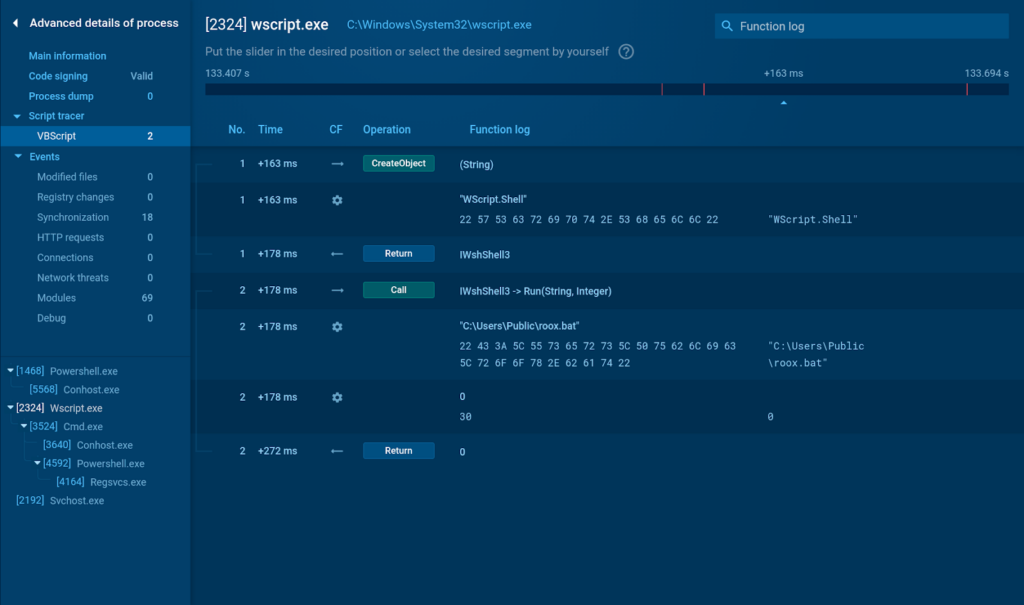
ANY.RUN’s Interactive Sandbox offers superior script executiion analysis

ANY.RUN cloud interactive sandbox interface
Be taught to Monitor Rising Cyber Threats Check out expert info to accumulating intelligence on rising threats with
OF Lookup
Be taught full info Question Mark (?)
What it does
The question mark represents any single character or its absence. This suggests it might properly stand in for exactly one character or none the least bit. Why use it
The question mark is good for situations if you find yourself undecided a couple of certain character in your string or know that it varies. Occasion
Proper right here, we’re capable of borrow a query from Jane_0sint’s article on phishing investigations, which is supposed for determining samples of Mamba2FA assaults.
- A notable part of this query is that we’re capable of see the question mark getting used twice. However, there is a distinction between these two conditions:
- The first one is the wildcard that serves as a stand-in for the characters “m”, “n”, and “o” that are typically utilized in Mamba2FA URLs.
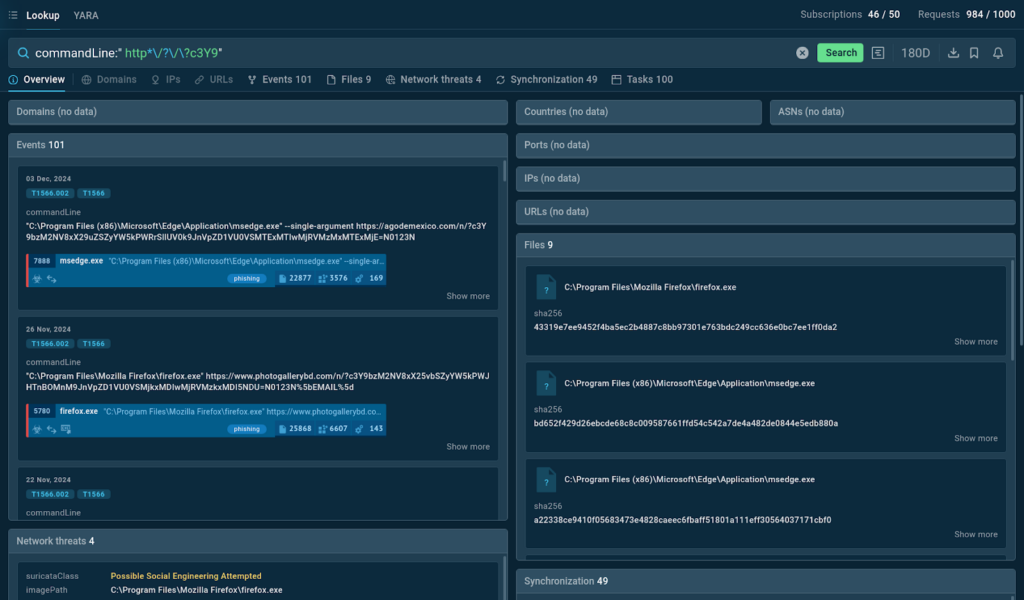
Be sure that to flee ? when it is part of your search string
We as quickly as as soon as extra can observe various outcomes, along with command traces that embrace fully totally different URLs matching our query. Buck Sign ($)
What it does
The dollar sign ensures that the search time interval ought to appear on the end of the string. It excludes matches with any characters after the specified content material materials. Why use it
The dollar sign is useful while you already know the exact ending of a string nevertheless are unsure regarding the beginning. It helps you uncover matches that end alongside together with your specified time interval. Occasion
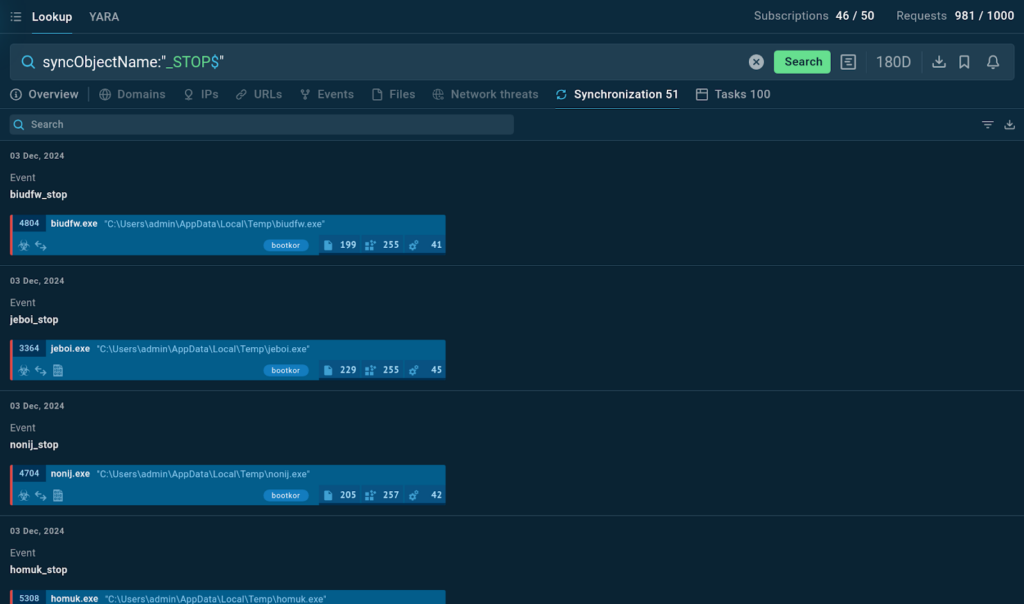
will likely be explored intimately in its corresponding sandbox session
Among the many many outcomes, we’re capable of see mutex names akin to biudfw_stop, jeboi_stop, and nonij_stop. As always, we’re capable of uncover each of them intimately by navigating to their corresponding sandbox intervals. Caret (^)
What it does
The caret ensures that the search time interval ought to appear at the beginning of the string. It prevents matches with any characters sooner than the specified query content material materials. Why use it
The caret is beneficial while you already know the exact place to start of a string nevertheless are unsure in regards to the the rest. It narrows down your search to devices that begin alongside together with your specified time interval. Occasion
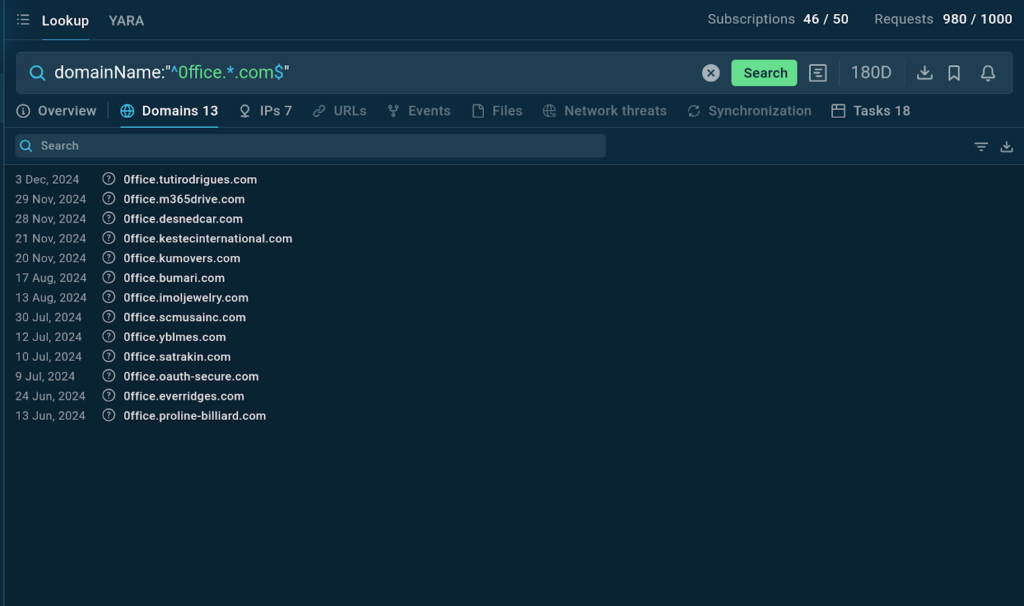
TI Lookup returns all matching domains found all through its database over the earlier 180 days
TI Lookup provides us with domains that match our query along with sandbox intervals, the place they’ve been found.
Conclusion
Wildcards and operators in TI Lookup current the pliability and precision needed to hold out threat intelligence searches. By learning how you should utilize these devices, you can too make your threat looking efforts easier.
Give it a attempt by requesting a free trial of TI Lookup.
About ANY.RUN
ANY.RUN’s Menace Intelligence Lookup and YARA Search firms allow for precise threat looking and the extraction of priceless insights into current cyber threat developments. What’s spectacular is how briskly these scans are—they significantly tempo up the analysis course of, allowing for quick detection of threats and malware.
Try ANY.RUN’s Interactive Sandbox and Menace Intelligence Lookup for FREE →





