Packers and Crypters in Malware and How to Remove Them

On this text, we’ll uncover the most common types of protectors—packers and crypters—along with straightforward strategies to detect and take away them.
We’ll moreover introduce some useful devices to simplify the strategy and improve your malware analysis skills.
What Are Protectors and What Kinds Are There?
Protectors are devices designed to complicate code analysis, making it extra sturdy to detect and have a look at malware. Two of the most common types of protectors are packers and crypters.
1. Packers
Packers are utilities that bundle a variety of recordsdata proper right into a single executable, often together with compression. This course of makes static and dynamic detection more durable, a tactic many types of malware exploit.
Positive malware, like these written in scripting languages (e.g., Python or JavaScript) or relying on non-standard libraries, require packing to carry out appropriately by along with interpreters and essential libraries.
Conventional examples of packers embrace installers like NSI and MSI, UPX, MPress, and self-extracting archives (SFX) made with devices like 7zip or WinRAR.
Packers usually don’t defend software program info, making it comparatively easy to extract them at runtime in a sandbox or take away the packer using static devices.
2. Crypters
Crypters take security a step further by encrypting the executable’s contents, often together with layers of packing and obfuscation. Designed to obscure code, crypters make analysis additional difficult and time-consuming. Examples of crypters embrace NetReactor, Themida, and VmProtect.
Important Security Methods of Crypters:
- Dynamic unpacking in memory to stay away from leaving any disk trace.
- Encryption of recordsdata, info, and code, with decryption at runtime.
- Code Obfuscation: Modifications the development and sequence of instructions, transforming (meta)info into unreadable or meaningless characters.
- Virtualization: Transforms code into pseudo-instructions which is likely to be each regenerated or interpreted at runtime.
Observe that with out virtualization, code is commonly weakly protected and would possibly often be restored to its distinctive or near-original state.
Determining Packers: Simple Methods and Useful Devices
Detecting packers will probably be simplified with only a few straightforward strategies and specialised devices like DIE (Detect It Easy). DIE notifies prospects when a packer is detected, making it a quick decision for preliminary identification.
Let’s ponder the following sample. When analyzing it with DIE v3.10, we’ll observe the presence of the MPRESS packer.
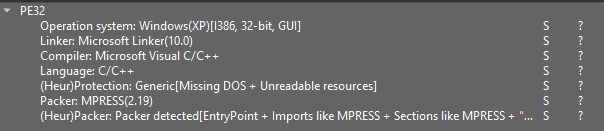
Opening the sample in DIE reveals half names that time out packing.
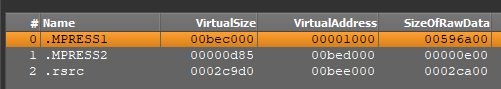
Packers like UPX and MPRESS often create sections with distinctive names, paying homage to MPRESS1 and MPRESS2, which help analysts decide their utilization.
We’re capable of moreover have a look at PE (Moveable Executable) information inside the Static Discovering window inside ANY.RUN sandbox. This provides further particulars to help decide these packers and their specific traits.
Analysis of a sample with UPX sections
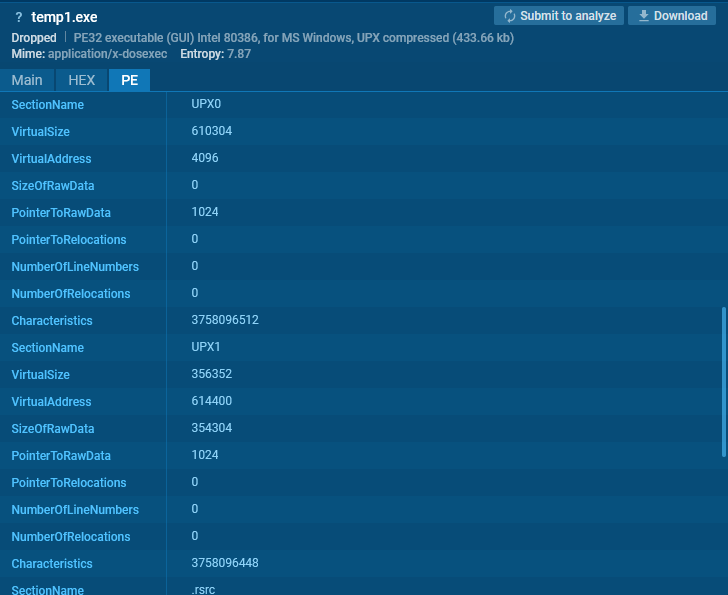
We’re capable of decide UPX through half names. In positive situations, packers like VMProtect and Themida may additionally be acknowledged by their distinct half names.

Sections, paying homage to .vmp0, level out VMProtect (see occasion).

Sections, paying homage to .themida or .taggant, signal the presence of Themida (see occasion).
Widespread Indicators of Packers
The most common indicators for packers embrace:
Unusual Half Names and Placement
For example, packers like Themida/Winlicense often have sections with random names or clear areas as half names (occasion). The image underneath displays that Sections #4 and #5 have random names, whereas sections #0 and #3 comprise clear areas as a substitute of names.
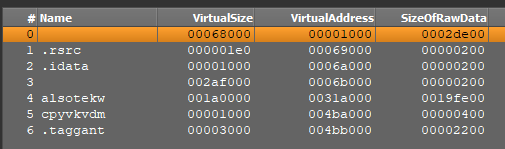
In VMProtect, the half addresses inside the file (notably the PointerToRawData self-discipline) are typically set to zero (occasion).
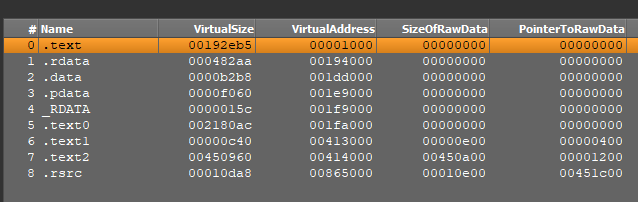
Throughout the image above, for sections #0 through #5, PointerToRawData is about to zero, which signifies that unpacking occurs dynamically at runtime.
Unusual Imports
The absence or minimal number of imports signifies that libraries are loaded, and their carry out addresses are acquired dynamically at runtime.
For .NET capabilities, a single import (mscoree.dll:: _CorExeMain) is typical. In some situations, a singular combination of capabilities can reveal the equipment’s intentions.
For example, let’s open the Static Discovering window contained within the ANY.RUN sandbox for this UPX sample and go to the Imports half.
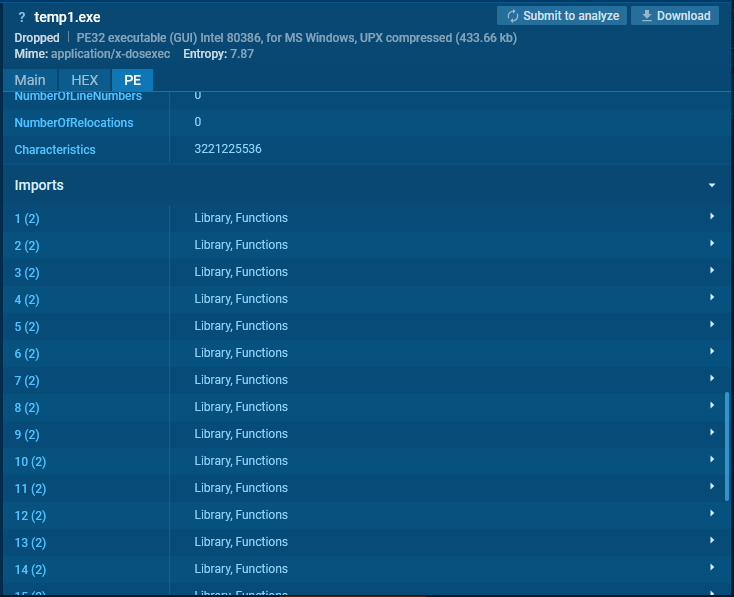
Then, let’s look for KERNEL32.DLL.

The combination of LoadLibraryA and GetProcAddress signifies dynamic library loading, whereas VirtualProtect would possibly counsel an intention to change memory net web page security to executable.
Since solely 4 capabilities are present proper right here, this combination is unlikely to be coincidental and would possibly signal intentional manipulation for code execution.
Extreme Entropy
For unpacked recordsdata, the overall entropy often ranges from 5 to 6.5. Packed recordsdata, however, often exhibit entropy ranges above 7, approaching 8 (the utmost entropy for 8-bit info).
Extreme entropy values can level out packing or encryption, as they counsel an absence of readable patterns all through the file.
This entropy stage will probably be checked using devices like DIE (Detect it Easy).
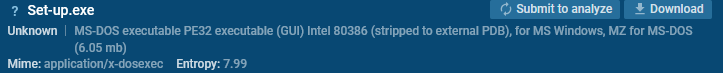
You may additionally confirm it correct contained within the ANY.RUN sandbox.
Unpacking Utterly totally different Kinds of Packers
There are two principal types of unpacking:
- Static unpacking: The code is processed by the unpacker nonetheless not executed. This system depends upon analyzing the packed file with out working it, allowing for a safer examination.
- Dynamic unpacking: The code is executed and preserved by the unpacker in memory. This technique entails working the packed malware in a managed setting, often in a sandbox, to observe the unpacked code in movement.
Dynamic unpacking might be probably the most troublesome sort of unpacking, as a result of it often requires utilizing a debugger and capturing memory dumps.
This technique permits analysts to observe how the code behaves at runtime, however it absolutely requires a managed setting and additional superior devices to observe and extract the unpacked code exactly.
To make the strategy of the analysis easier and faster, you probably can profit from ANY.RUN’s Interactive Sandbox. It offers memory dumps of unpacked and decrypted info, along with the decrypted executable payload.
The sandbox generates memory dumps for diverse processes and makes them on the market for receive, saving analysts vital time and simplifying the analysis course of. You probably can receive these memory dumps and analyze them domestically.
There are two decisions for accessing memory dumps generated inside ANY.RUN’s sandbox.
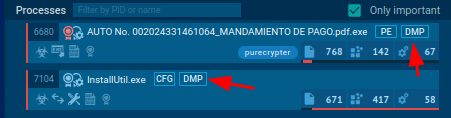
You probably can entry them by clicking on the DMP button inside the course of tree half.
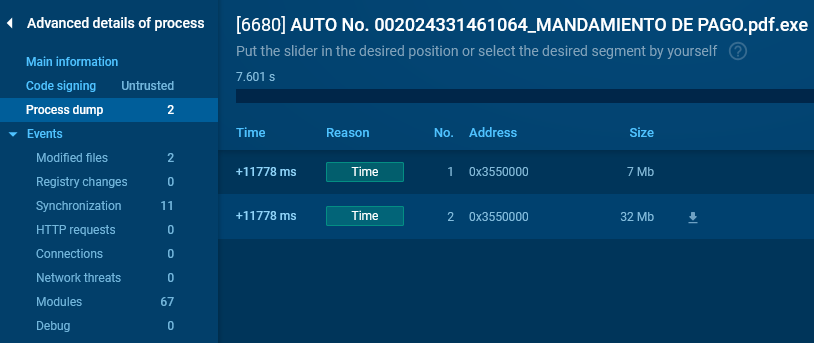
Alternatively, you probably can go to “Superior Particulars” of a course of that has the DMP icon subsequent to it and navigate to the “Course of dump” half, the place you probably can receive the dumps.
Let’s now see how one can cope with varied sorts of packers.
SFX Installers
SFX (Self-Extracting Archives) is an archive format that, when executed, extracts recordsdata and would possibly perform specific actions. Typically, these archives will probably be unpacked statically with utilities like 7zip or WinRAR.
To see a typical SFX in movement, let’s ponder the following sample.
Such archives often have a specific icon, indicating they’re self-extracting executables:

Use WinRAR to open the archive and have a look at the extraction settings and packed recordsdata all through the SFX.
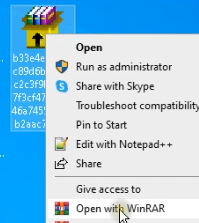
After opening the file, on the becoming side, you’ll uncover extraction parameters, file paths, and the primary executable file. On the left, you probably can view all recordsdata packed all through the archive.
MSI Recordsdata
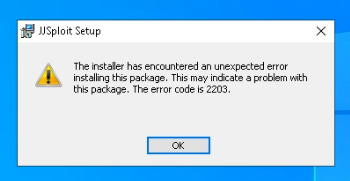
To unpack MSI recordsdata, a typical methodology is using the command line with msiexec /a. However, this system may not work for every file and would possibly usually result in errors.
For example, with the following sample, making an attempt this command in a sandbox triggers an error (see sandbox occasion).
An alternate decision is LessMSI, a specialised instrument for extracting recordsdata from MSI packages.
Let’s see the best way it really works this using the following sample.
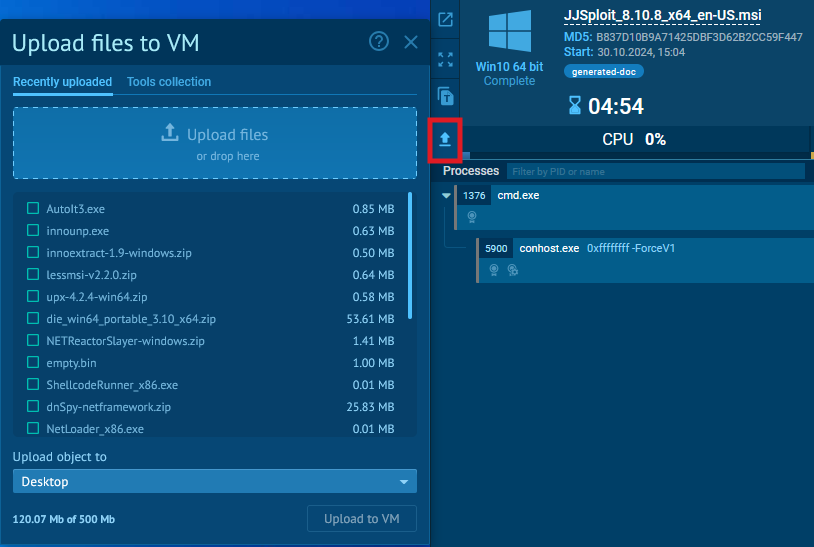
Add the LessMSI archive to a digital machine in ANY.RUN by the add button.
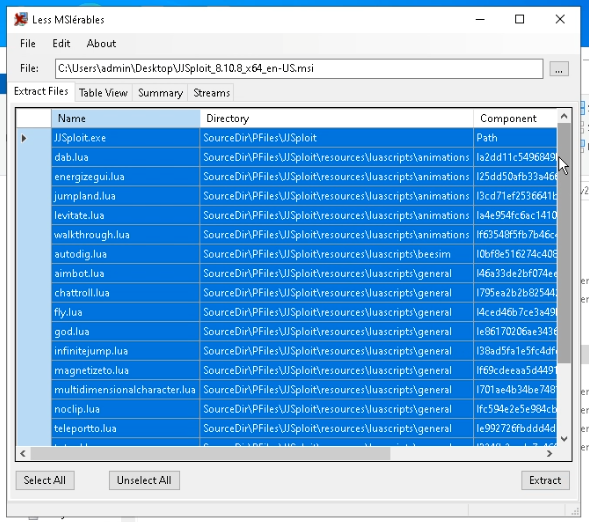
Launch the GUI mannequin of LessMSI and select the MSI file. Subsequent, this method will present a list of recordsdata and their paths for extraction.
Nullsoft Installer
Nullsoft installers are typically straightforward to unpack using 7zip. By opening these recordsdata with 7zip, you probably can instantly entry the contents of the installer.
Let’s have a look at this sample for additional particulars.
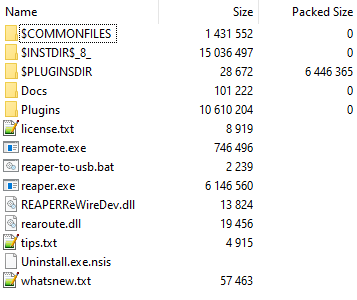
Opening the archive in 7zip reveals the recordsdata packed inside it, along with specific directories that often start with the $ picture.
This technique permits you to uncover the installer’s recordsdata merely. However, a limitation is that it doesn’t reveal the preliminary arrange parameters, which may be essential for deeper analysis.
InnoSetup
Unpacking InnoSetup installers requires specialised devices. The unpacking turns into harder because of these recordsdata often comprise embedded scripts that administration the arrange course of.
On this case, 2 useful devices may be utilized:
- innoextract: A command-line instrument designed to extract recordsdata from InnoSetup packages.
- innounp: One different instrument that provides associated efficiency, supporting different variations of InnoSetup.
Let’s ponder this sample.
Start a digital machine with the necessary utilities and unpack innoextract.
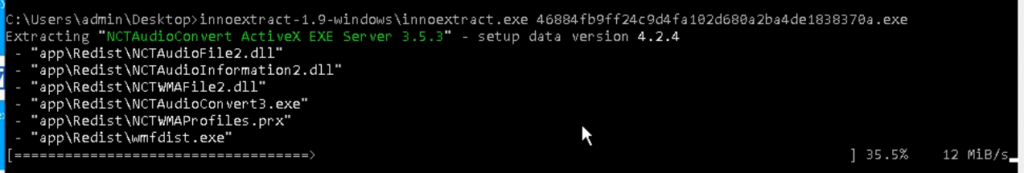
Consequently, we’ll pay money for a variety of directories. The precept one is appRedist, which includes the executable file.
Furthermore, recordsdata paying homage to help paperwork, libraries, samples, and totally different related sources are extracted.

Registry info entries are extracted individually as properly.
The app itemizing incorporates recordsdata unpacked by the installer.
The reg$HKCU itemizing incorporates info entries which is likely to be added to the registry beneath CURRENT_USER.
Innounp works in an an identical methodology.
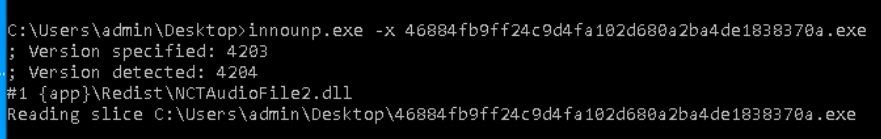
Consequently, software program and registry info are extracted.
The good thing about this utility is that it restores the arrange script and saves it in a file.
We’re capable of open this file in a notepad.
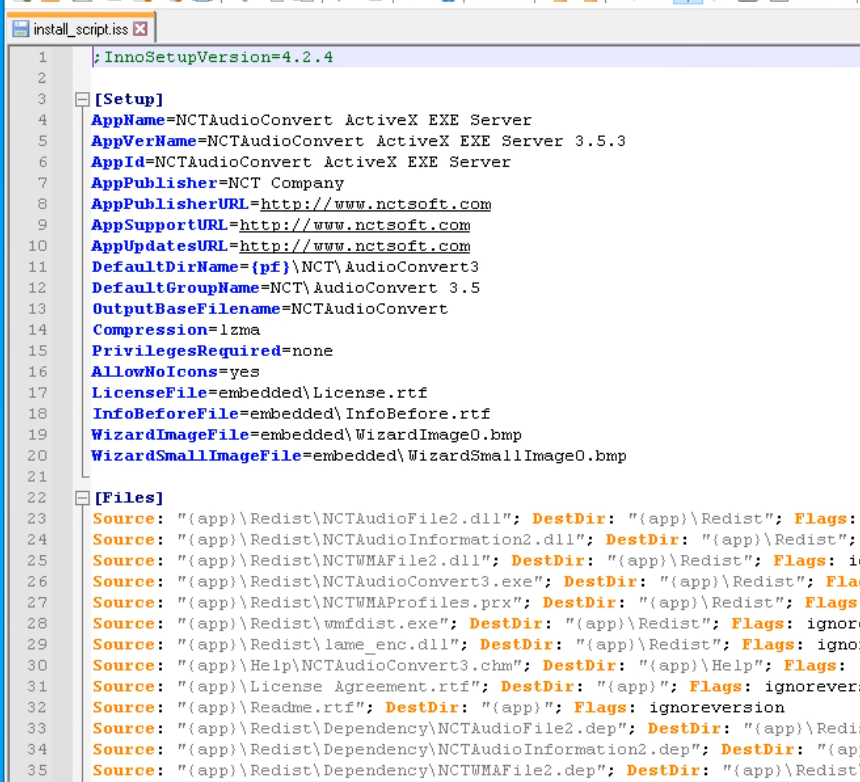
The [Run] half incorporates particulars in regards to the recordsdata that is likely to be executed after unpacking.
NSIS + ASAR
It’s worth mentioning the SFX archives utilized by Electron.js.
Let’s ponder this occasion.
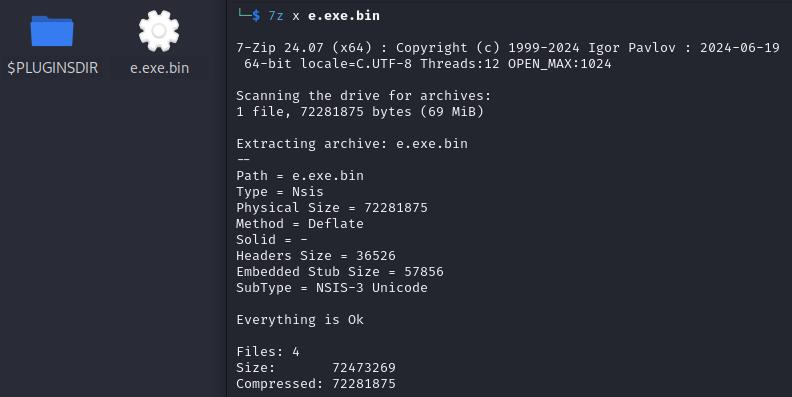
Receive the EXE file and start the unpacking course of.
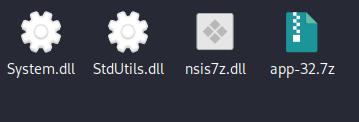
When extracting with 7zip, we pay money for a folder containing different recordsdata, along with an archive with a renamed Chromium executable (on this case, Runtime Vendor.exe) and its libraries.
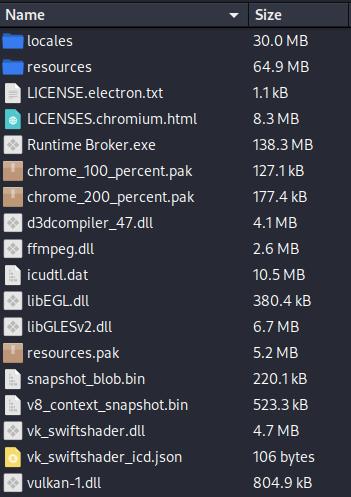
The Electron.js software program info is saved inside the sources itemizing.
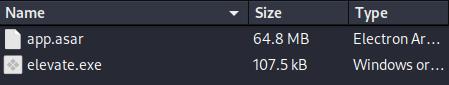
The app.asar file is an archive containing the Electron.js software program info.
To unpack it, you’ll need an npm module.
- Arrange npm: sudo apt arrange npm
- Run the following command to extract the archive: npx @electron/asar extract app.asar extracted
- If the asar module isn’t already put in, npm will quick you to place in it.
On account of working the command, the archive is likely to be unpacked into the extracted folder.
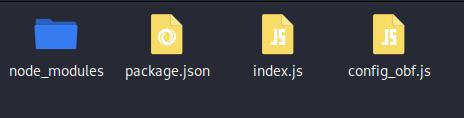
The node_modules folder incorporates the Node.js packages, and index.js is the preliminary script of the equipment.
UPX
UPX (Remaining Packer for eXecutables) is a packer for executable recordsdata.
- Compatibility: It helps solely native PE (Moveable Executable) capabilities.
- Unpacking: UPX-packed recordsdata are typically easy to unpack statically using the an identical UPX utility.
To unpack a UPX-packed file, you solely need to make use of a single command:
upx –d UPX will probably be acknowledged by the presence of sections named UPX0 and UPX1 inside the file.
Let’s observe it with the following sample.
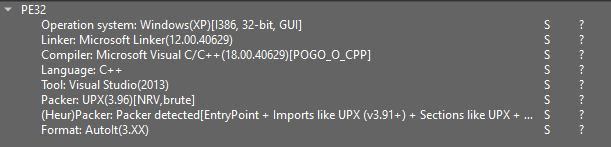
First, receive the sample and open it in DIE (mannequin 3.10). DIE will level out the presence of UPX, itemizing specific indicators.
Some malware samples use older variations of UPX. In such situations, you’ll need the corresponding mannequin to unpack them. DIE suggests the advisable mannequin, which, on this occasion, is 3.96.
To analyze a sample like this, it’s vital to remove the UPX compression; in some other case, the disassembler gained’t have the power to interpret the code appropriately.
For example, Ghidra—a free disassembler and decompiler—will present a variety of errors when importing a compressed file.
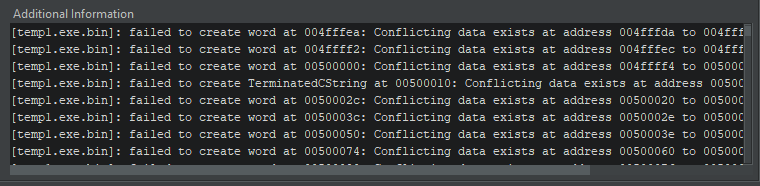
All through analysis, Ghidra will detect solely a single carry out. The built-in decompiler will report the wrong code.
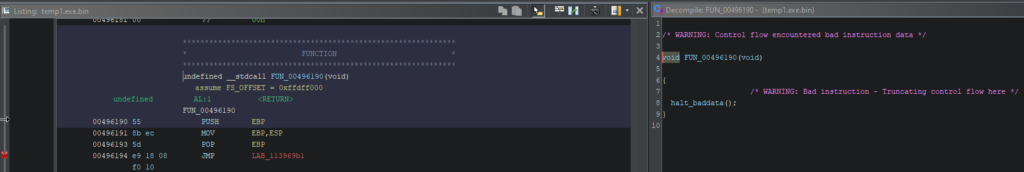
Throughout the image above, on the left side, there is a Itemizing displaying the one carry out, whereas on the correct side, the Decompiler window displays an error message.
To conduct analysis, receive the newest launch of UPX from GitHub.
Subsequent, add the sample along with the upx.exe file (it’s not important so as to add your complete archive) to the digital machine.
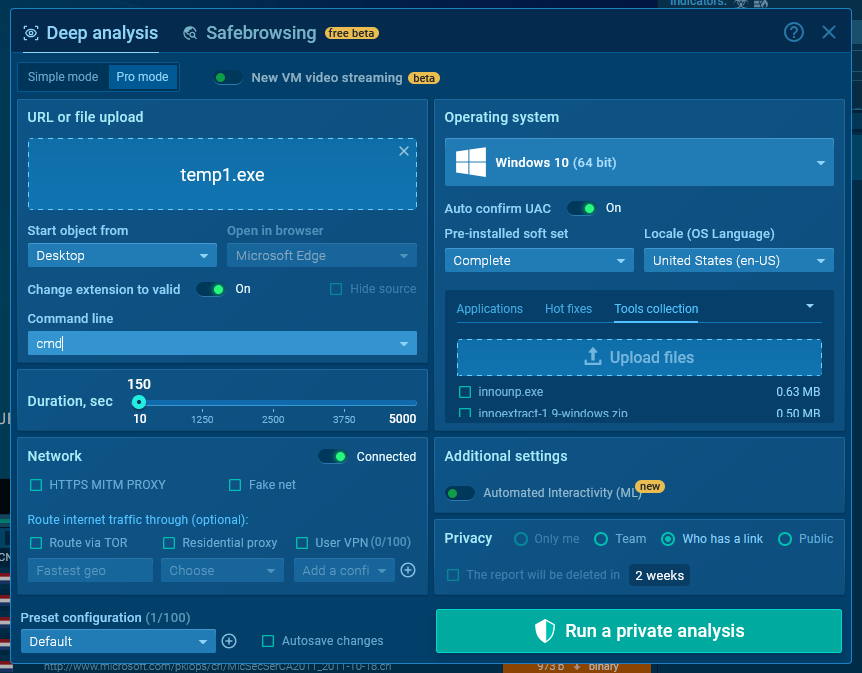
To do this, swap to the Skilled mode inside the sandbox and select Devices assortment. Proper right here, you probably can each use beforehand uploaded devices or add new ones.
Sooner than starting the analysis, enter the “cmd” command inside the Command line self-discipline. This will likely cease the sample from working routinely and may open the console originally of the session.
All further steps are carried out inside the following analysis session.
Unpack the UPX archive and enter the following command inside the console:
upx.exe -d On account of the command execution, the file is likely to be overwritten with the decompressed mannequin.
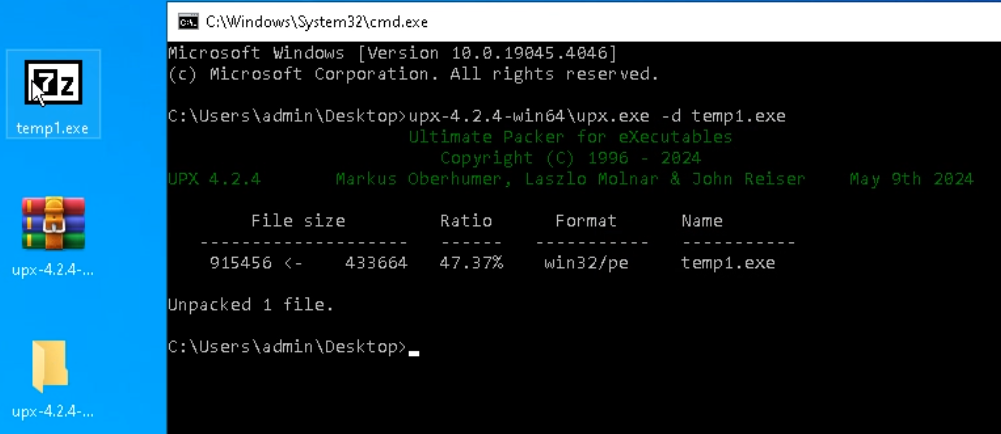
To verify the unpacked sample is functioning appropriately, let‘s run it in a sandbox.

When clicking the PE button, the Static Discovering window opens, the place we’ll observe a particular hash.
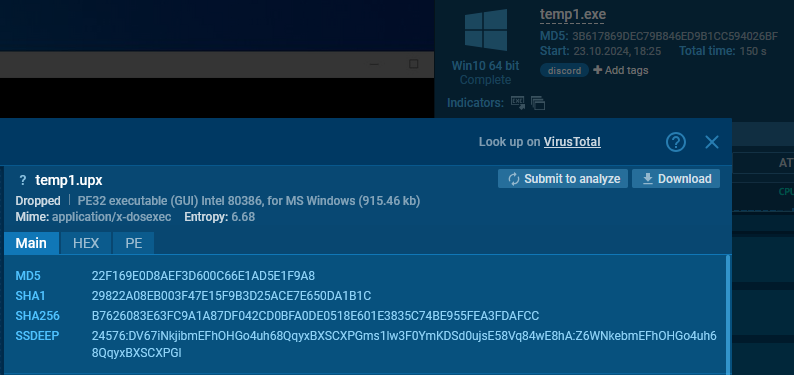
The Static Discovering window for the unpacked file, displays the determine beneath which it was saved to disk. We’re capable of see a decrease in entropy, an enhance in file dimension, and a fully totally different hash price.
Now, Ghidra can cope with this file with none factors.
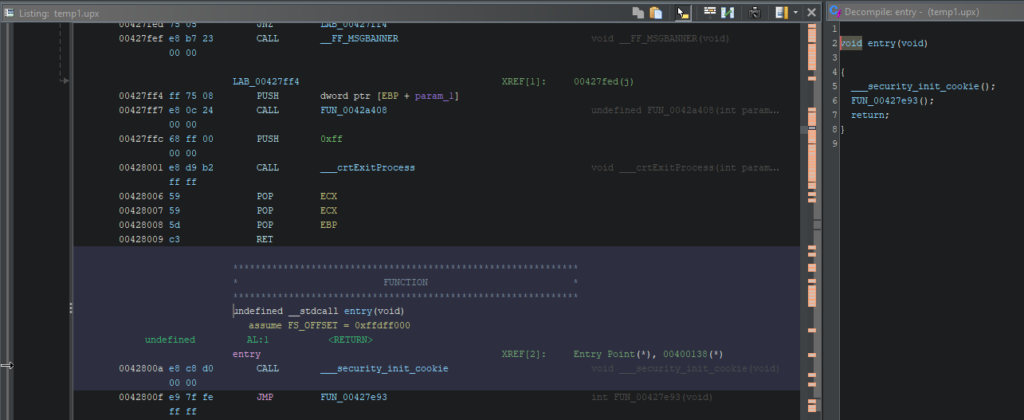
Throughout the Itemizing half, we see fairly just a few references and capabilities, and the Decompiler window reveals the proper code.
The an identical course of will probably be carried out on a bodily machine, as UPX does not execute code all through unpacking.

Research to research cyber threats
See an in depth info to using ANY.RUN’s Interactive Sandbox for malware and phishing analysis
Study full info
AutoIt
AutoIt is often used as a crypter. The one strategy to detect AutoIt is by checking the file description. To do this, go to the Important tab inside the Static Discovering window inside ANY.RUN and scroll down.
You could possibly uncover fully totally different mentions of AutoIt inside the description.
Let’s ponder the following sample.
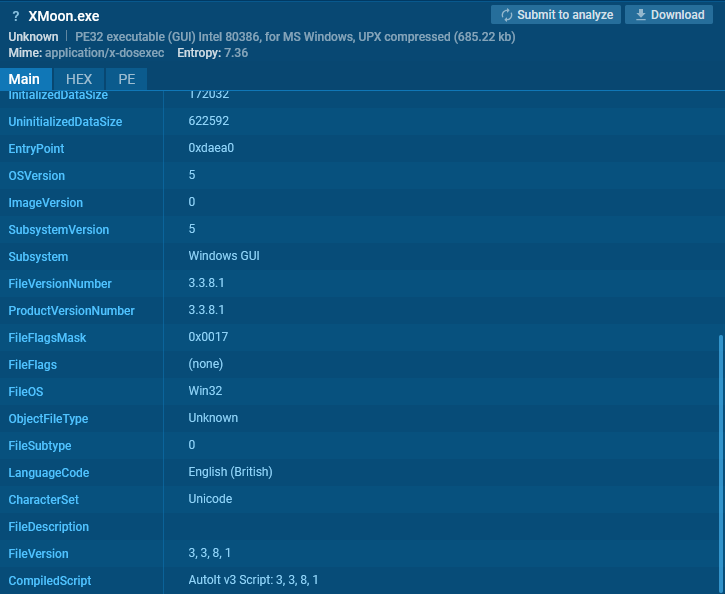
Proper right here is one different occasion. Usually, such a file is an AutoIt interpreter bundled with a script.

In some situations, a deeper examination is required. Let’s take a look on the subsequent occasion.
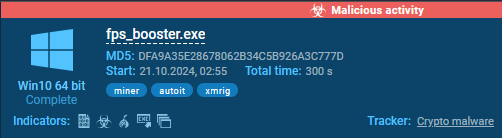
On this occasion, AutoIt was detected by ANY.RUN’s sandbox. Let’s affirm this in DIE.
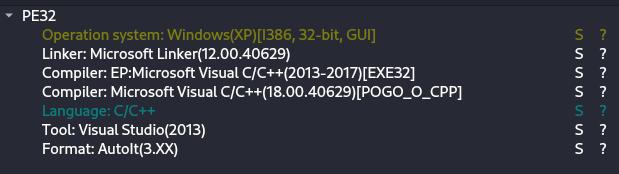
To extract and decompile the script, we’ll use AutoIt-Ripper.
Let’s arrange it using pip arrange autoit-ripper.
The latter is kind of easy to utilize:
autoit-ripper 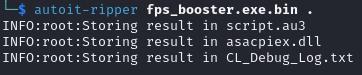
On account of working the command, the restored script is saved to a file named script.au3. Along with, all the associated recordsdata have been detected and saved.
Now it’s doable to research the script’s actions by opening it in a textual content material editor.
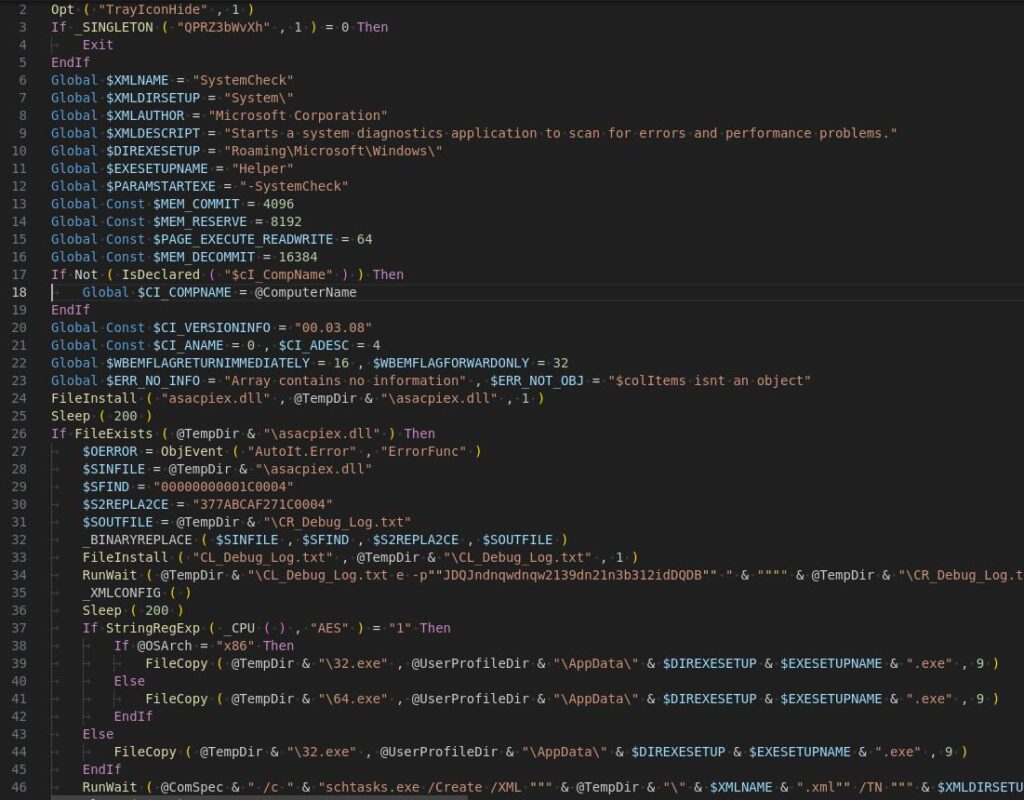
On this occasion, we see the execution of CL_Debug_Log.txt with specific parameters.
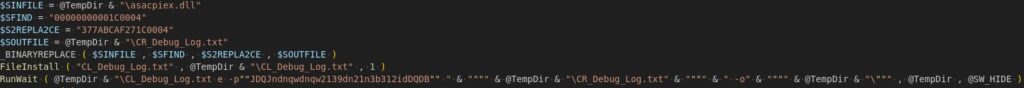
Opening CL_Debug_Log.txt in DIE reveals that it is a standalone mannequin of 7zip.
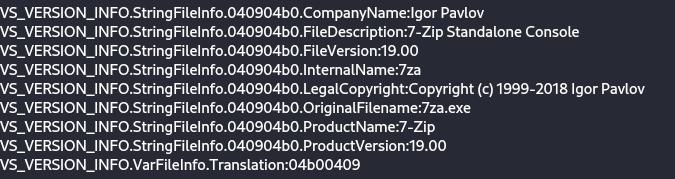
On this methodology, the malware unpacks the recordsdata essential for its operation. In addition to, the script incorporates checks for execution in a digital setting.
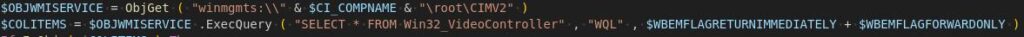
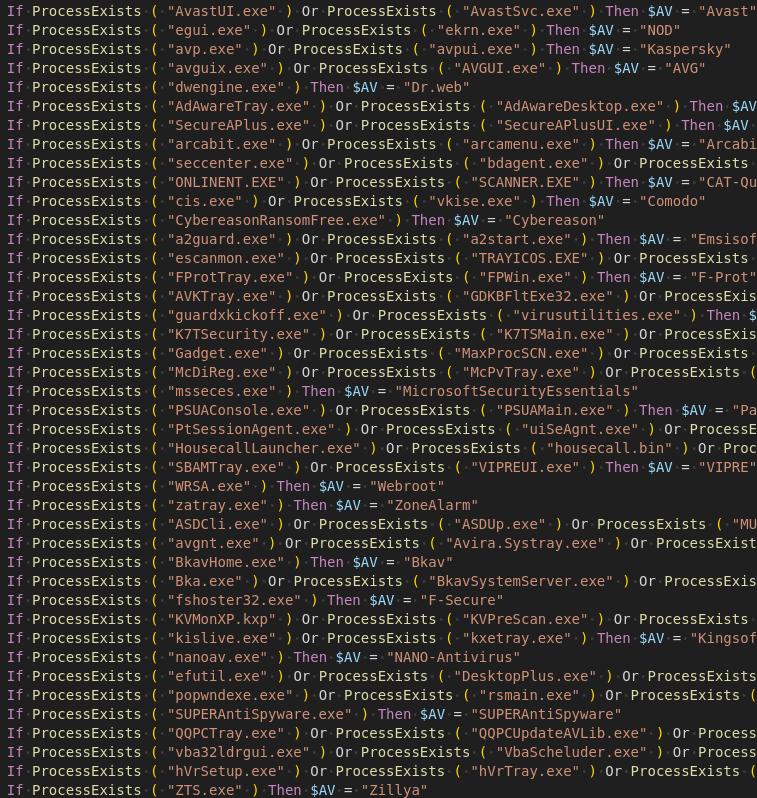
It moreover comprises checks for the presence of antivirus software program program.
NetReactor
NetReactor is a packer and obfuscator for capabilities written in .NET.
- Helps code virtualization.
- Recordsdata and libraries often should not saved to disk nonetheless are loaded instantly into memory.
- Modifications the development of the code, making analysis more durable.
Most recordsdata will probably be effectively unpacked using NetReactorSlayer, nonetheless for the right outcomes, dynamic unpacking is advisable. This system executes the code all through the working system, allowing system capabilities to be often known as as needed for a additional appropriate unpacking course of.
Let’s take a look at an occasion with the PureHVNC payload.
Subsequent, run the analysis session using dnSpy and NetReactorSlayer.
dnSpy is not maintained; however, you probably can receive a forked mannequin.
Then, open the sample in dnSpy.
Sooner than processing, you probably can see fairly just a few namespaces.
Let’s discover the configuration class.
Open Kind References and discover the IPAddress class.
Correct-click on it and select Analyze.
Throughout the opened window, click on on on Utilized by to go looking out the tactic the place this class is used.
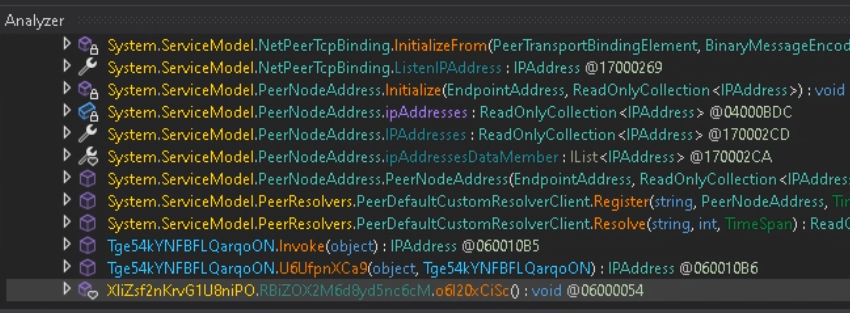
Now, open NetReactorSlayer and select the sample.
There are a selection of settings on the market; the default settings work properly for this goal.
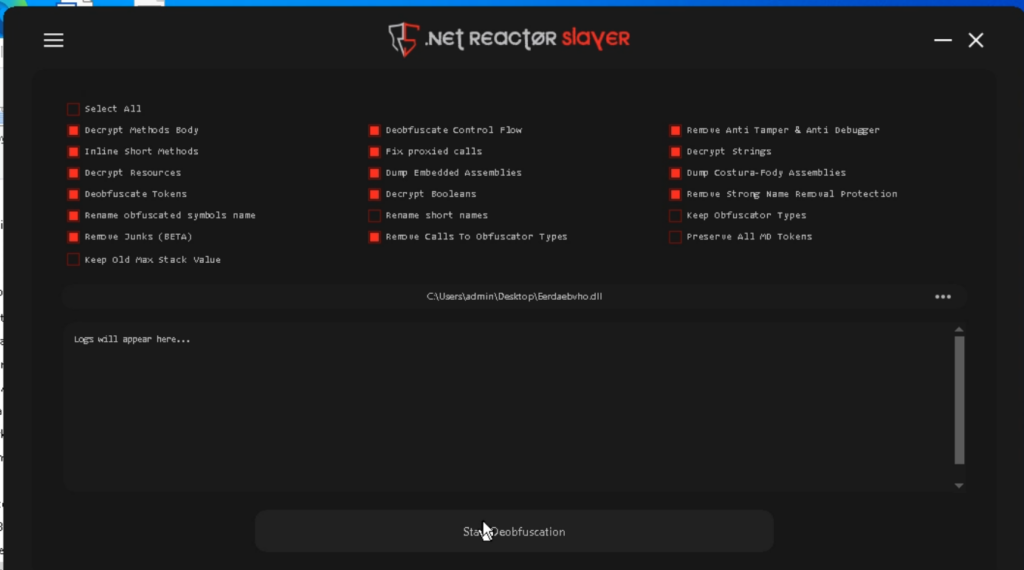
Click on on Start Deobfuscation and look ahead to the strategy to complete.
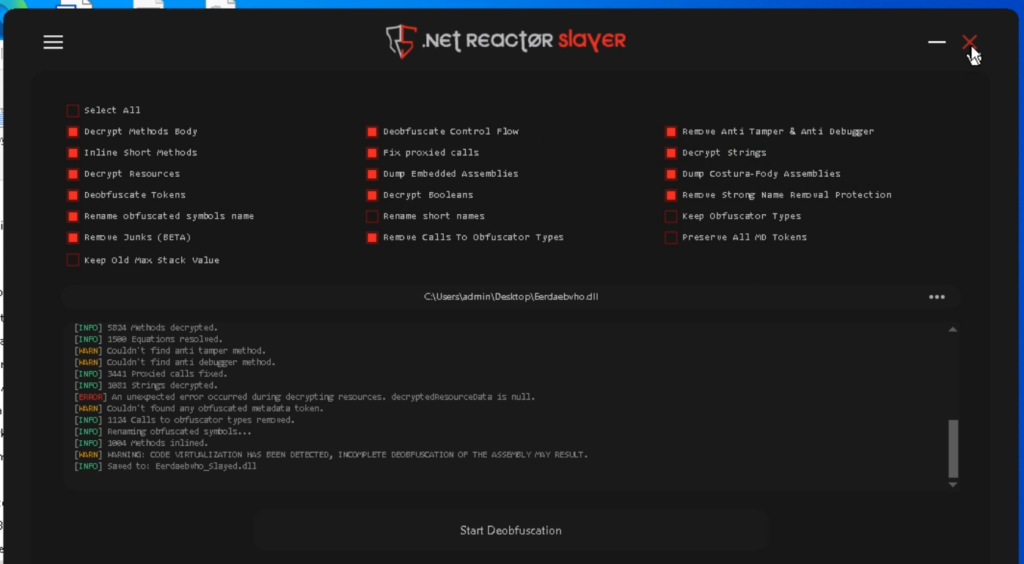
This technique decrypts strings, simplifies the code, and even makes an try to remove virtualization.
The file is saved with the suffix _Slayed.
Now, open the obtained file in dnSpy. Consequently, the pointless namespaces have been eradicated.
The teachings have been renamed too.
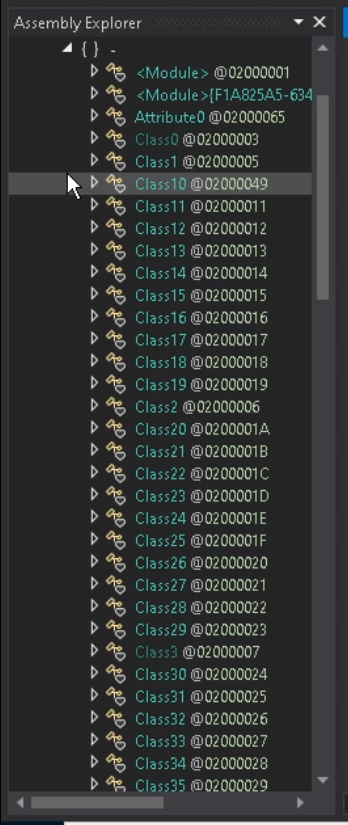
Subsequent, let’s seek for the utilization of IPAddress as properly.
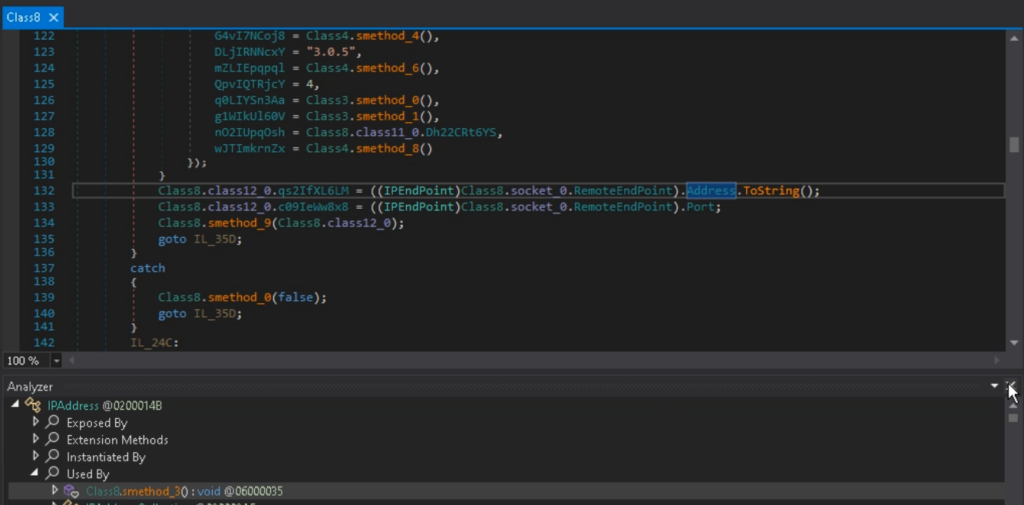
The extended class names have been shortened, and the fields have been renamed consistent with their respective values. The code has turn into easier to research, and string literals are literally included.
Normally, together with being packed, malware is saved in an encrypted variety inside a specific loader (crypter).
This analysis demonstrates the strategy of extracting the payload using dnSpy.
After execution, the crypter decrypts the payload and performs an injection into the objective course of.
With the help of dnSpy, let’s join the debugger to the strategy. To do this, go to the Debug tab and click on on on Connect with Course of.
Then, choose the strategy you want.
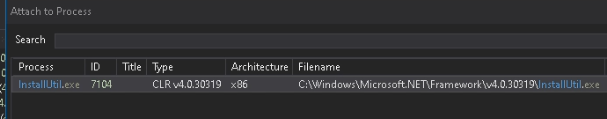
Observe that to debug 32-bit processes, you could run dnSpy x86, and for 64-bit processes, use dnSpy x64.
Pause the strategy and open the Modules window.
Correct-click on the first module, then select Open Module from Memory.
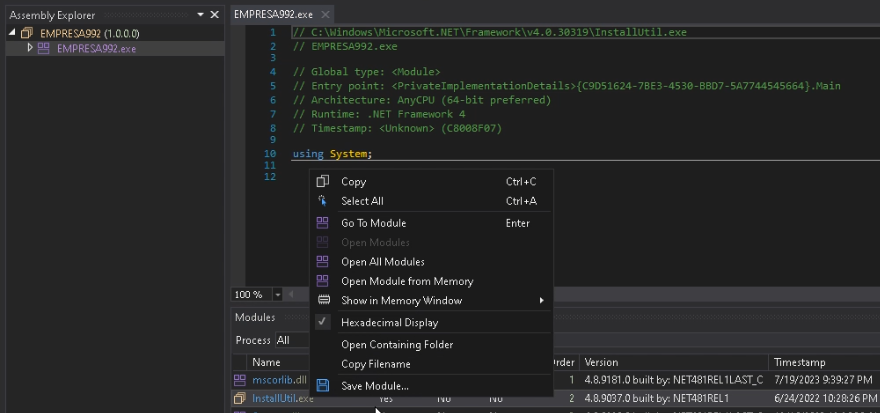
After opening the module, obfuscation will probably be observed.
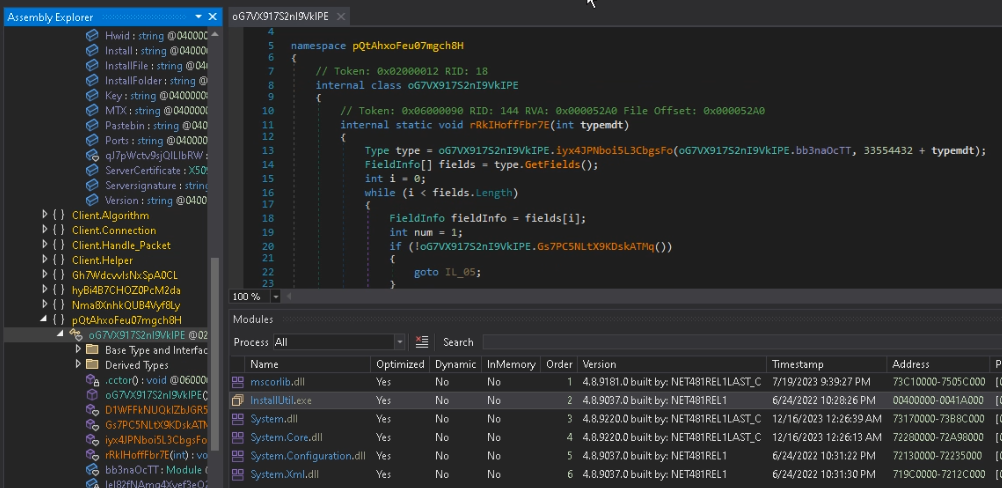
Click on on Save Module and swap the saved file to the console mannequin of NetReactorSlayer.
Consequently, we get the following output.
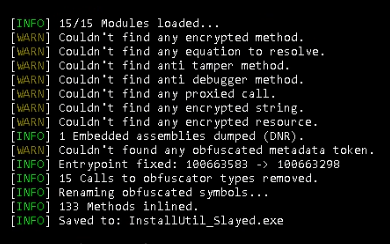
NetReactorSlayer corrected the entry stage, eradicated pointless code, and saved consequence to disk as InstallUtil_Slayed.exe.
The associated library MessagePack.dll has been saved as a separate file.
Now, the payload InstallUtil_Slayed.exe will probably be run individually and analyzed through debugging (See sample analysis).
SmartAssembly and Completely different .NET Packers
One different widespread packer for .NET capabilities is SmartAssembly.
Check out this occasion.
Along with obfuscating the code (which makes the execution order unclear and renames identifiers to unreadable phrases), SmartAssembly complicates analysis with quite a few delegates which is likely to be resolved at runtime, along with these used for decrypting strings.
Let’s open the sample in DIE and ensure the presence of the protector.
We’re capable of see how DIE detects Protector Good Assembly.
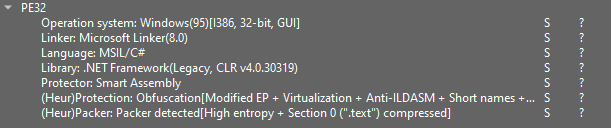
Throughout the US (Shopper Strings) tab, there could also be an abnormally small number of strings.
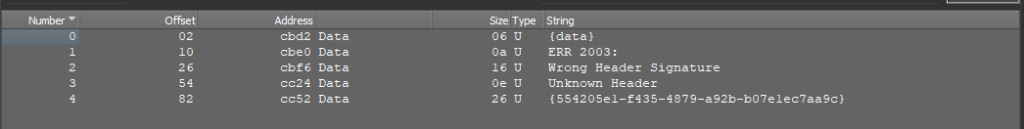
Let’s swap to dnSpy.
Upon opening the sample, you will immediately uncover an attribute indicating the presence of the SmartAssembly protector.
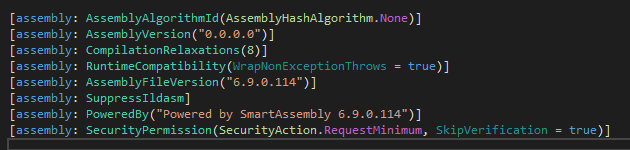
Moreover, you’ll uncover the attribute namespaces associated to SmartAssembly.
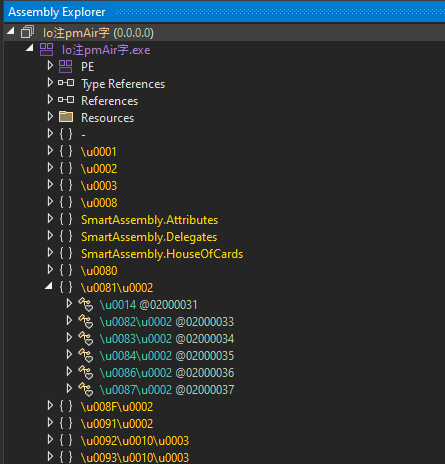
These artifacts are pretty frequent amongst protectors, considerably in .NET capabilities.
Subsequent, click on on on Go to Entry Stage.
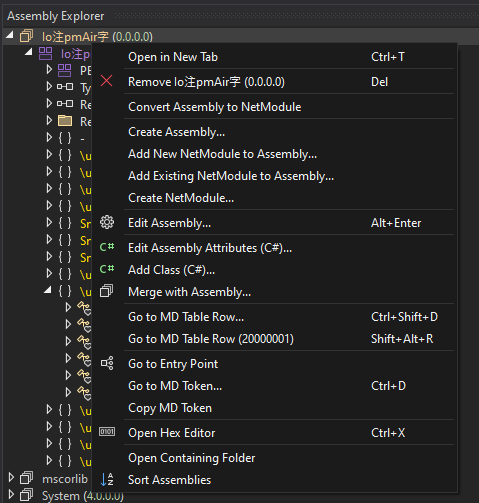
On this case, whereas the code (administration transfer) simply is not obfuscated, the strings are obtained through a delegate title with a numeric argument.
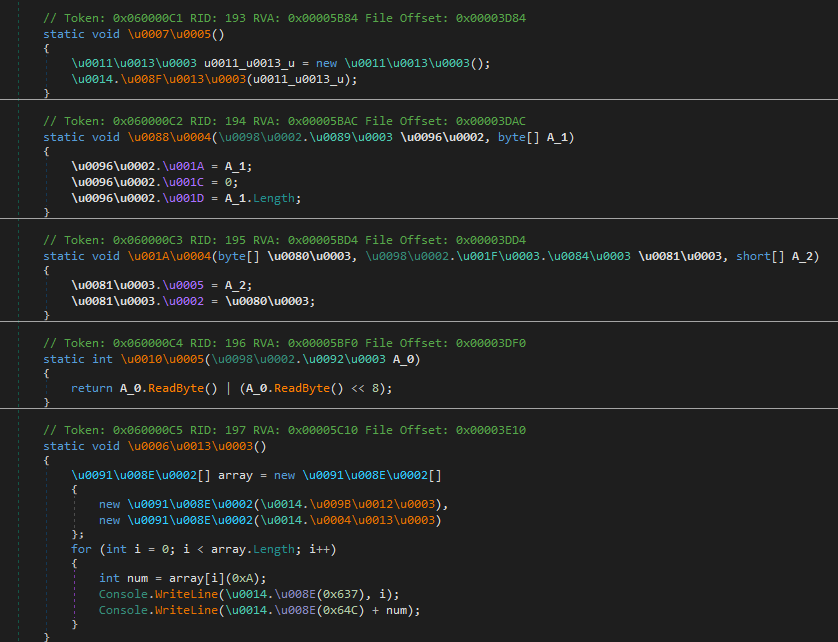
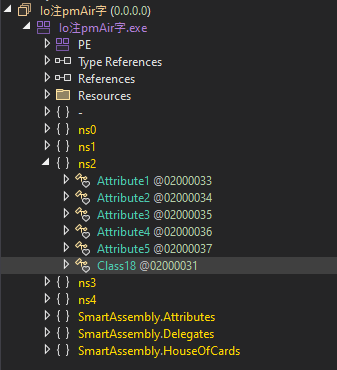
Earlier, we used NetReactorSlayer to remove the protector.
Whereas it is a specialised instrument, it could even be used for widespread capabilities, paying homage to simplifying code, though with some limitations.
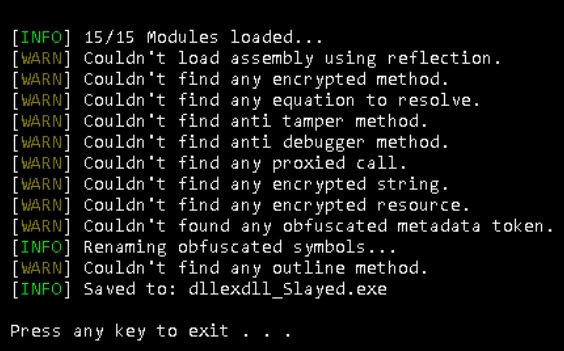
Let’s try to simplify the code using NetReactorSlayer.
Whereas this instrument simplified the code readability, it was unable to decrypt the strings.
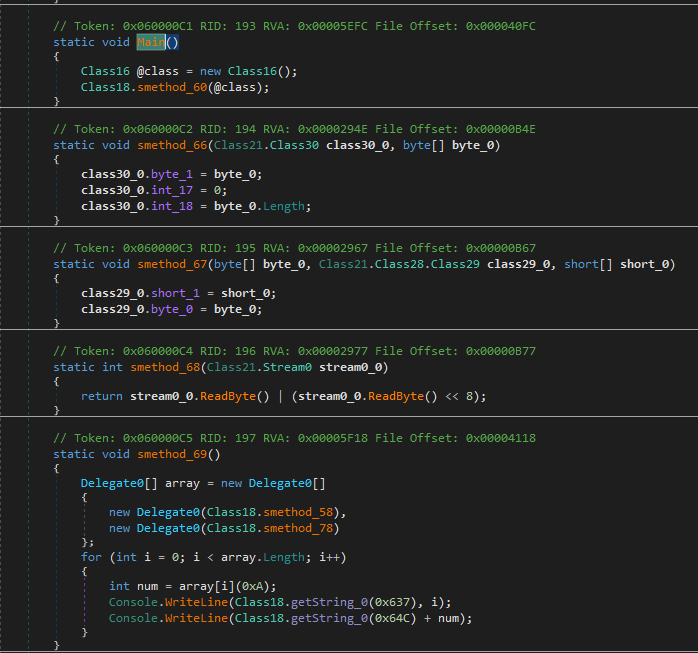
Now, let’s use one different instrument—de4dot—which may be part of what NetReactorSlayer makes use of for code simplification. You may additionally profit from de4dot-cex, which is the improved mannequin of de4dot.
For this case, we’re going to use de4dot to remove SmartAssembly.
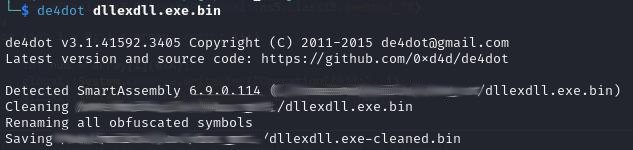
Consequently, the file is processed in an an identical methodology.
However, the string encryption has moreover been eradicated.
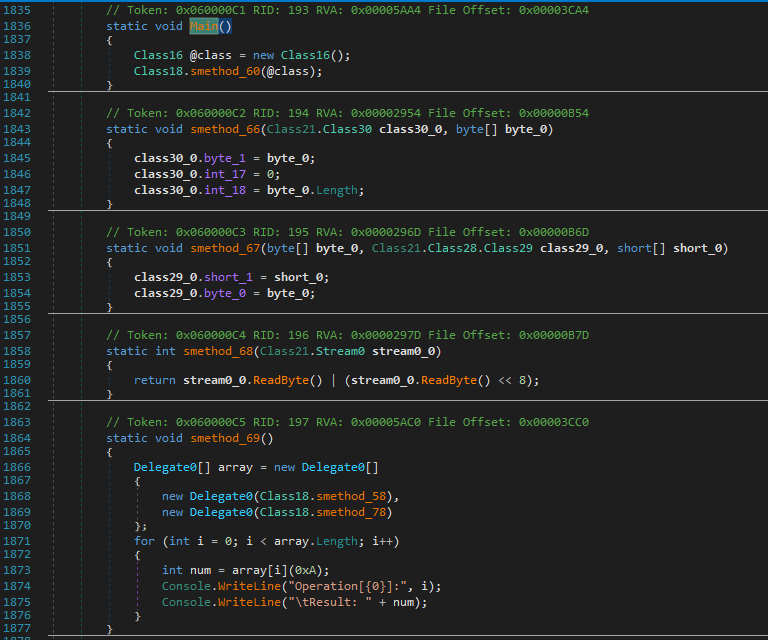
The GetString delegates have been modified with string literals.
In DIE, you probably can view all the decrypted strings.
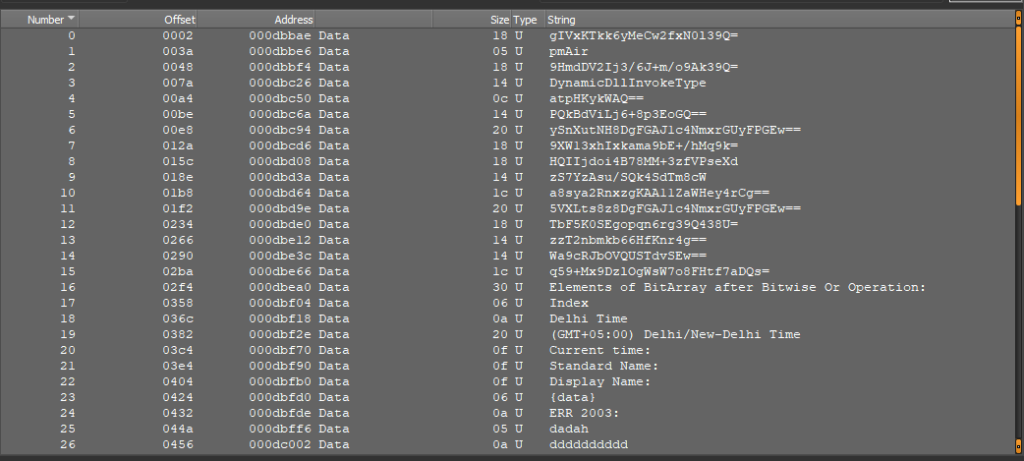
The processed file often retains efficiency and would possibly make runtime analysis easier.
de4dot works with many various protectors and would possibly simplify code analysis.
If de4dot doesn’t succeed, attempt using NetReactorSlayer, which may be extra sensible at further simplifying difficult code.
However, for older variations of NetReactor (underneath 6.0), de4dot stays the favored selection.
Themida, VMProtect
Themida and VMProtect are packers and obfuscators for capabilities that help virtualization and code mutation.
- Virtualization: This attribute protects the malware code at runtime, not merely in static analysis.
- Extracting Samples: Typically, virtualization simply is not utilized, allowing an unpacked sample to be extracted from memory, though it is likely to be partially modified.
- Static Unpacking: That’s usually unlikely, as these enterprise packers adapt quickly to new analysis methods.
For a additional detailed analysis, verify with our article: VMProtect and Themida Malware Analysis.
About ANY.RUN
ANY.RUN helps higher than 500,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that concentrate on every Dwelling home windows and Linux packages. Our menace intelligence merchandise, TI Lookup, YARA Search and Feeds, allow you uncover IOCs or recordsdata to review additional regarding the threats and reply to incidents faster.
With ANY.RUN you probably can:
- Detect malware in seconds.
- Work along with samples in precise time.
- Save time and cash on sandbox setup and maintenance
- Report and analysis all factors of malware habits.
- Collaborate collectively along with your workforce
- Scale as you need.
Request free trial →






