See Malicious Process Relationships on a Visual Graph

At ANY.RUN, we’re all about making in-depth technical data accessible. One in all many strategies we do that’s by providing you with assorted detailed, however easy-to-understand experiences on malware habits. One such report is Course of graph.
What’s Course of graph?
Course of graph is a report that visually reveals how system processes, notably malicious ones, relate to at least one one other.
On this text, we’ll uncover:
- How this small nevertheless very extremely efficient ANY.RUN operate works.
- And for those who might uncover it useful.
Tips about how one can entry the Course of graph report?
Course of graph is one amongst our clients’ favorite choices. Let’s stroll by way of how one can open this report using this analysis session recording as an example.
☝️ To entry all session experiences, full your analysis session first.
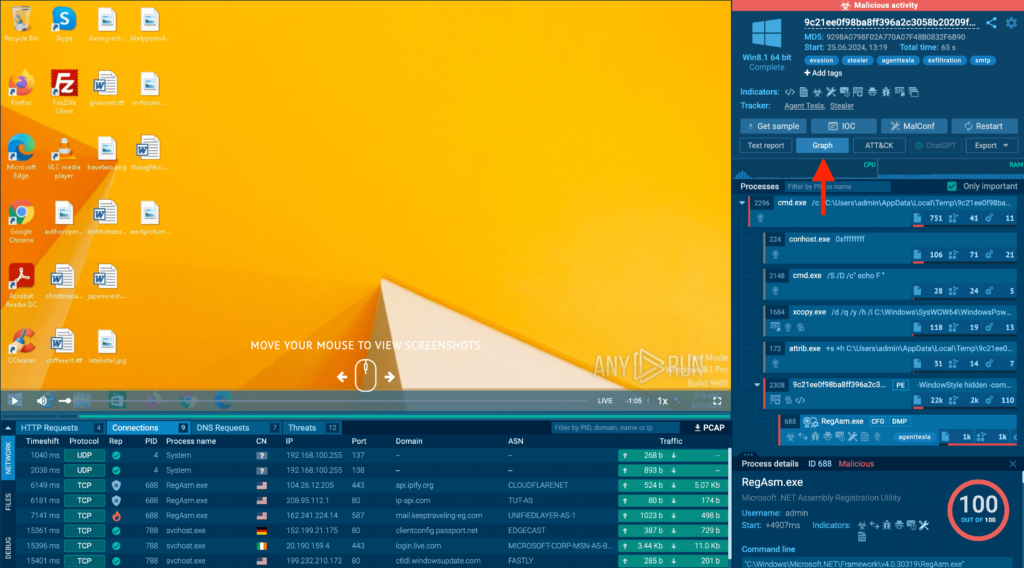
To open the graph, click on on on the Graph button inside the top-right nook of the show.
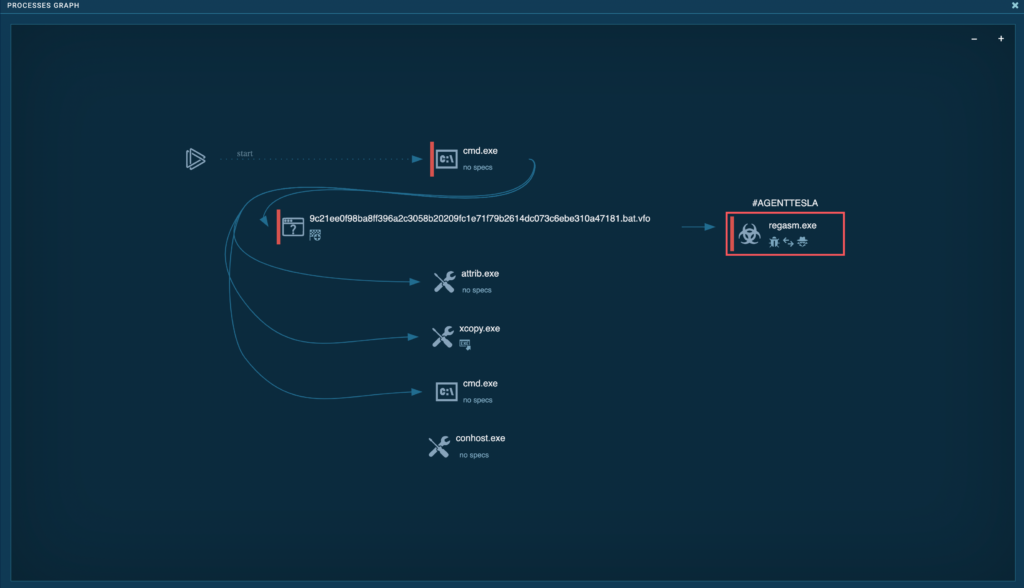
A model new full-screen popup will open, exhibiting you a visual illustration of system processes on a canvas.
This view makes it masses less complicated to see how processes relate to no less than one one different and trace parent-child relationships.
What can you do in Course of graph?
Course of graph has some hidden choices!
Firstly, it is a completely interactive seen illustration of the similar data you see inside the Course of tree. And just like inside the tree, you could entry additional information by clicking on each course of:
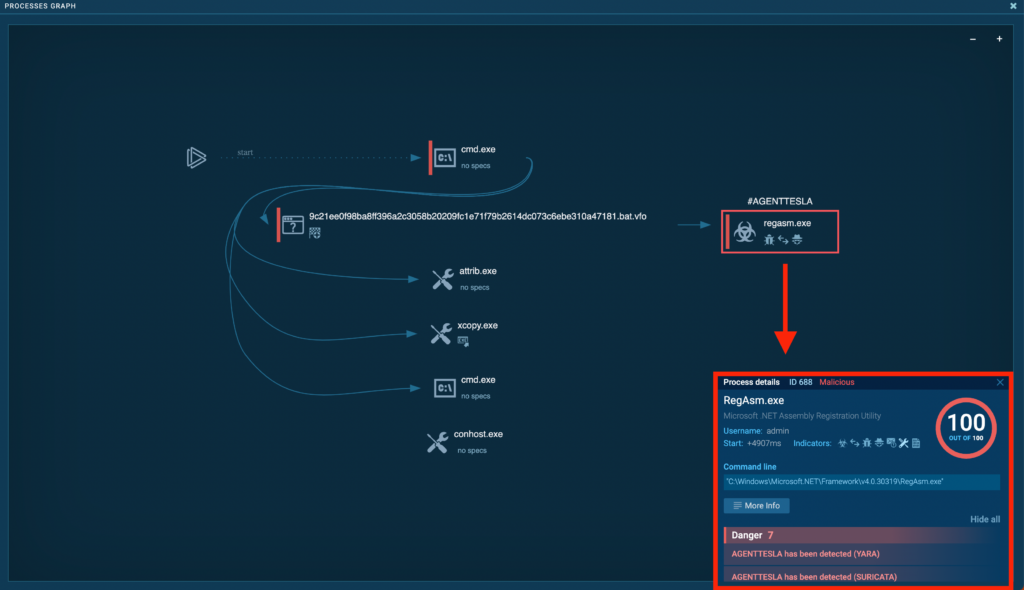
Clicking on a course of (identical to the one marked with #AGENTTESLA) reveals more information in a popup, along with:
- Expanded itemizing of indicators.
- Triggered signatures with descriptions.
By clicking Further infoyou could entry Superior course of particulars for an way more in-depth report:
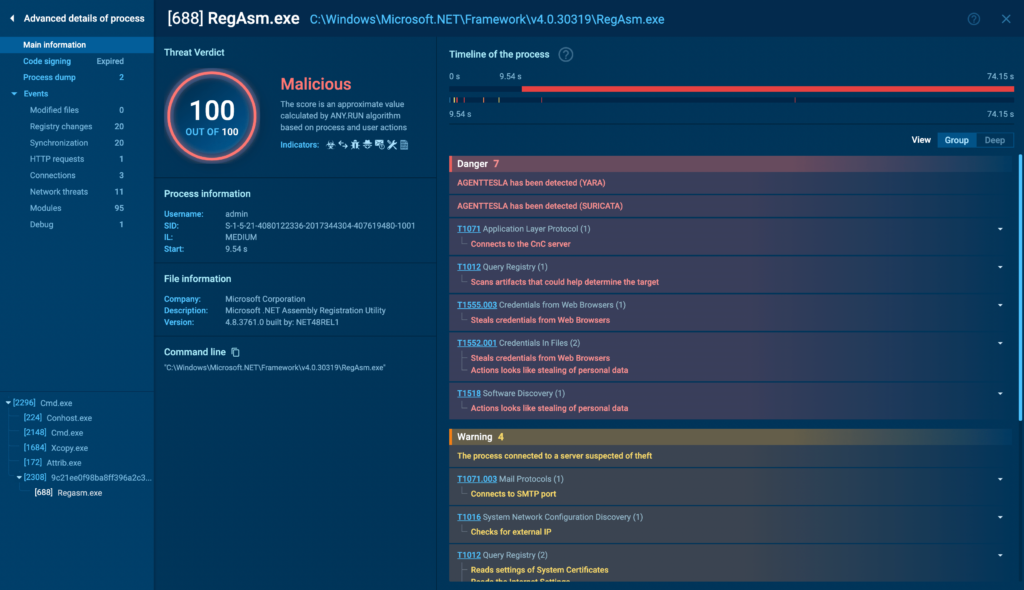
Secondly, you could switch throughout the canvas and zoom in and out.
In our first occasion, all of the information fits in a single show, nevertheless we’ll see this aspect greater used inside the subsequent occasion.
When might you use the Course of graph report?
Course of graph is very useful for those who’re working with a sample that has many nested or branching processes, making it powerful to determine the precept one from a vertical course of tree.
In numerous phrases, it’s most helpful when a linear tree view seems overwhelming or difficult on account of malware launching loads of child processes to mislead analysts.
Let’s see this in movement! Ponder this TrickBot sample:
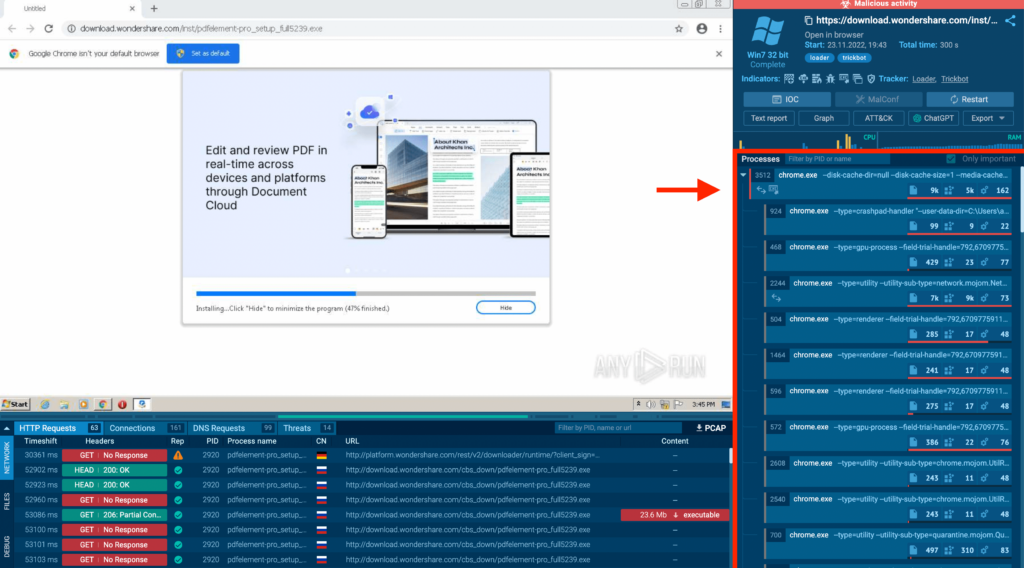
On this analysis session, the itemizing of processes goes on and on, and there’s an prolonged scrollbar. Let’s swap to the graph view to make sense of this complexity:
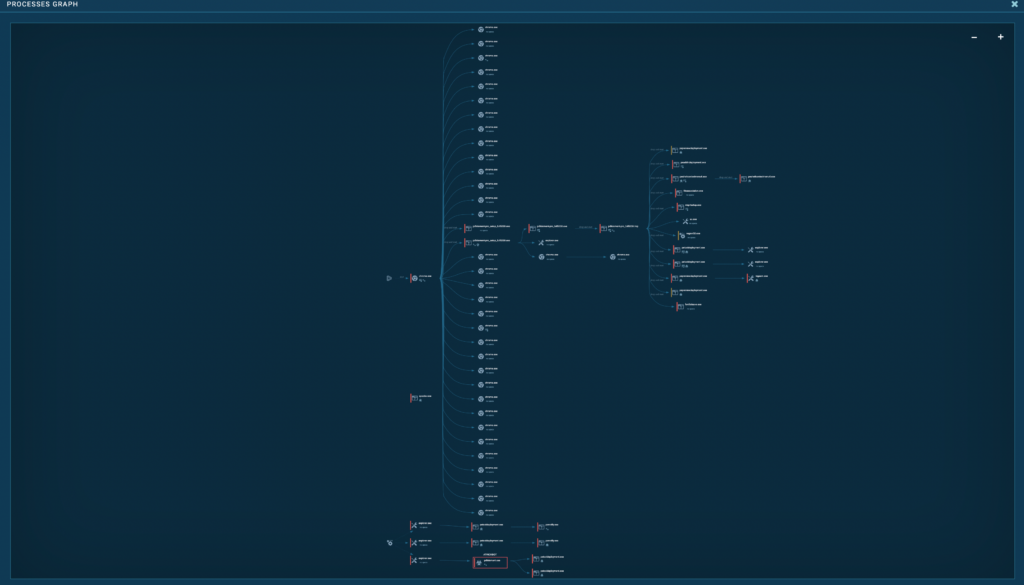
Now it turns into crystal-clear which processes are mom and father, which are youngsters, and the way in which they division out.
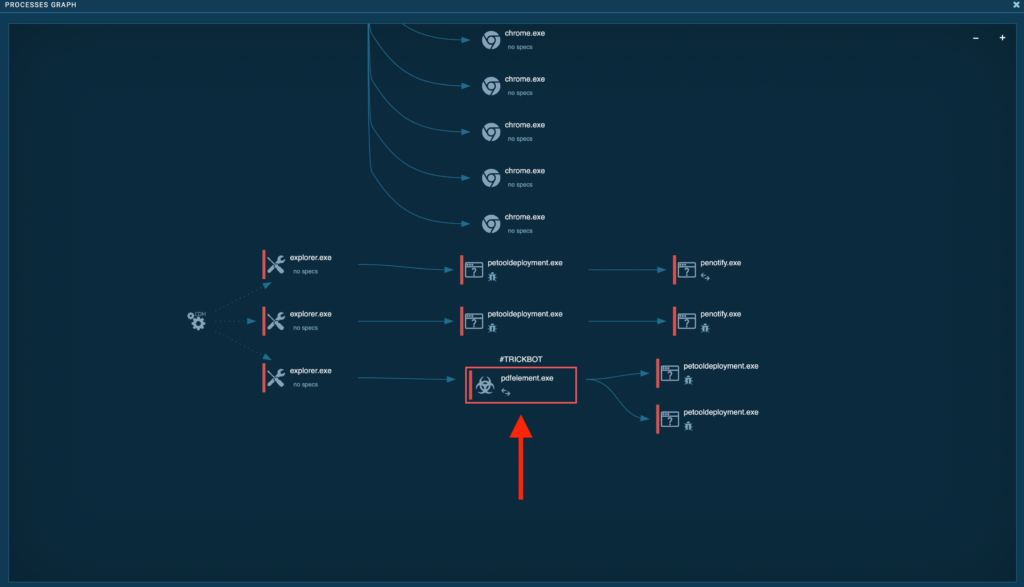
From proper right here, you could merely trace your strategy to the precept executable, which is on this group:
To summarize
Let’s shortly recap:
- Course of graph visually represents relationships between system processes, notably malicious ones.
- It’s interactive and you could click on on on processes to see additional particulars, along with malicious scores, indicators, and triggered signatures.
- Course of graphs are notably useful for superior malware samples with many nested processes, the place linear tree views turn into difficult.
- The graph view makes it less complicated to determine parent-child relationships and trace the precept executable in superior eventualities.
About ANY.RUN
ANY.RUN helps larger than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that concentrate on every House home windows and Linux methods. Our danger intelligence merchandise, TI Lookup, Yara Search and Feeds, help you to find IOCs or info to check additional regarding the threats and reply to incidents faster.
With ANY.RUN you could:
- Detect malware in seconds.
- Work along with samples in precise time.
- Save time and cash on sandbox setup and maintenance
- Doc and analysis all components of malware habits.
- Collaborate collectively together with your workers
Try the overall vitality of ANY.RUN with a 14-day free trial →





