Advanced Process Details: See Processes’ System Interactions

In case you look at suspicious data or potential malware, you need deep visibility into course of habits. ANY.RUN‘s Superior Course of Particulars provides exactly that – in-depth particulars about how a particular course of interacts with the system.
On this text, we’ll take a high-level check out what data you’ll uncover in superior course of particulars. Let’s get started!
Accessing the Attribute
To open superior course of particulars, uncover the tactic you have to look at within the main course of tree view. Then, click on on to choose it and seek for the Additional Data button.
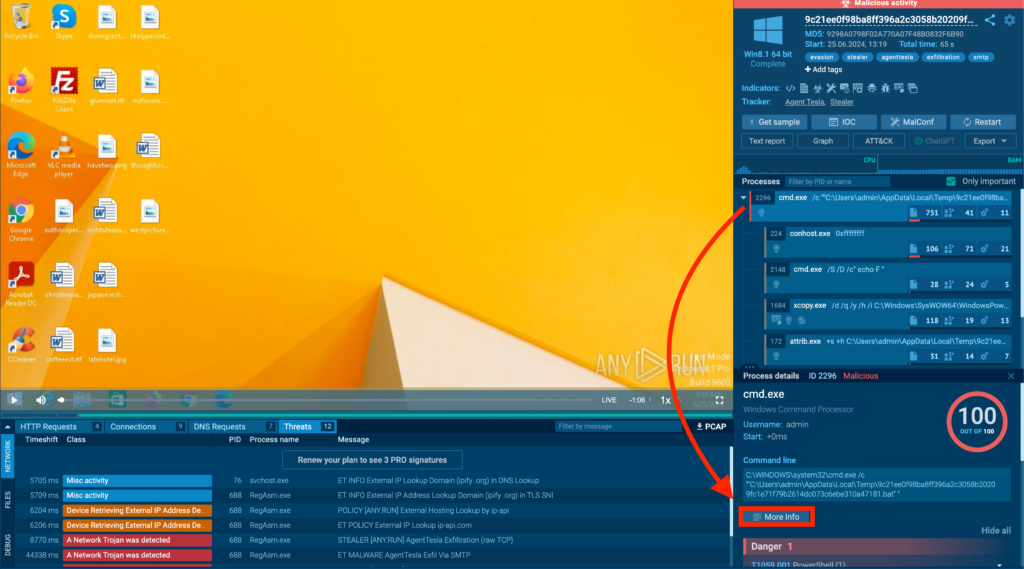
Clicking this button opens up the superior particulars interface:
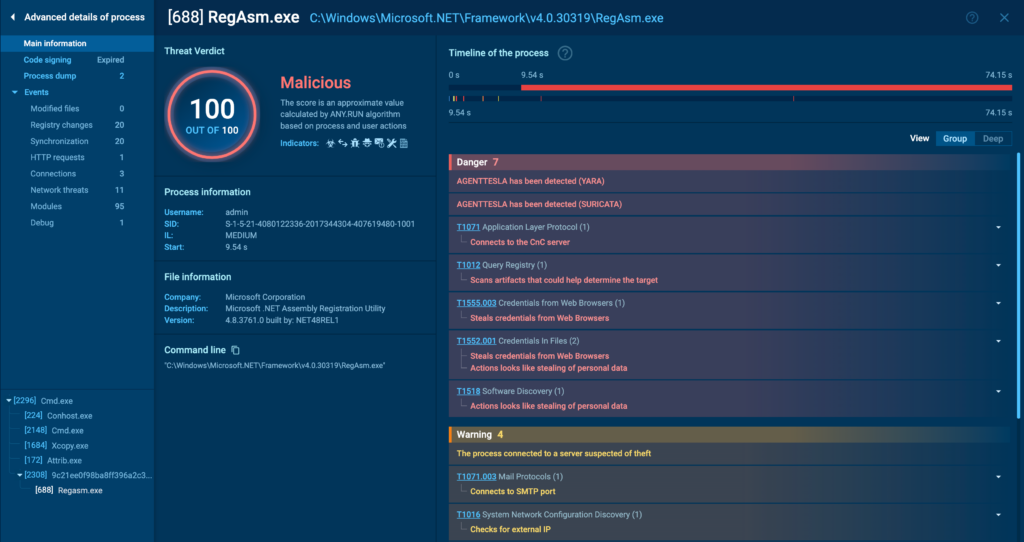
Interface Breakdown
Let’s start by breaking down the first interface, beginning with the ultimate data on the right. This half largely reveals the an identical particulars as the tactic tree, nevertheless in a further expanded and easier-to-read format.
You probably can immediately see the malicious ranking and signatures, along with their descriptions. In distinction to the tree view, proper right here you probably can change between Group viewwhich filters solely a really highly effective events, and Deep viewwhich lists all the tactic interactions with the system in sequence. Proper right here’s how that seems:
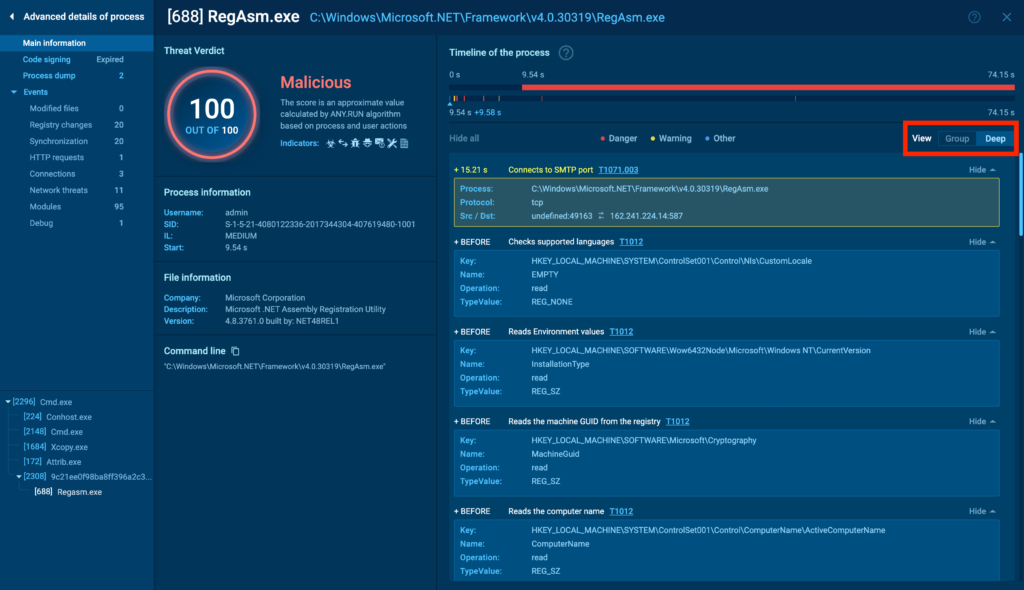
One different operate distinctive to superior course of particulars is the timeline. You probably can drag the pointer alongside it to manage the displayed events based totally on the execution timeline.
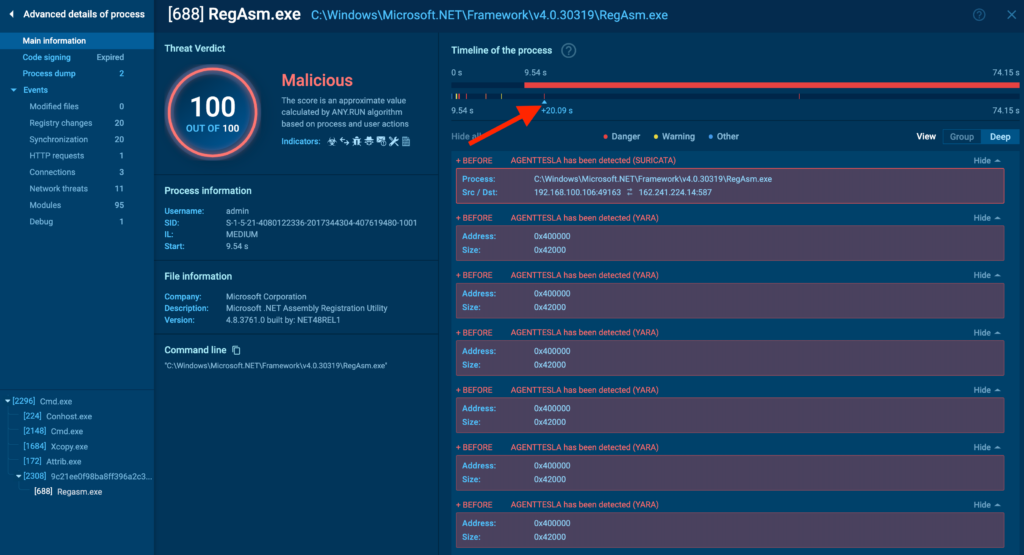
Now, let’s flip our consideration to the menu on the left. The vertical menu is break up into two sections:
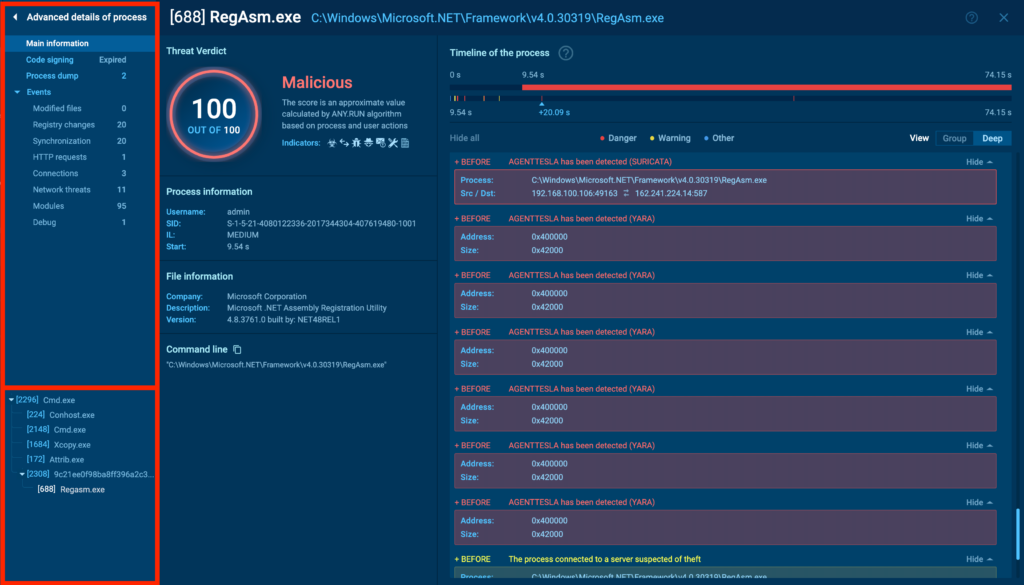
- The very best half includes tabs with further in-depth particulars in regards to the technique.
- The underside half incorporates a list of processes, allowing you to switch between them with out having to close out of the detailed view. Super helpful!
Breaking Down the Fully completely different Tabs
We’ll check out Predominant Information sub-menu first.
Code Signing
The Code Signing tab provides important insights into the authenticity of the tactic. It reveals whether or not or not the tactic has a professional digital signature, which is often used to verify the legitimacy of software program program.
On this tab, you probably can see the certificates particulars, along with the issuer, standing, validity, and in-depth particulars in regards to the signature.
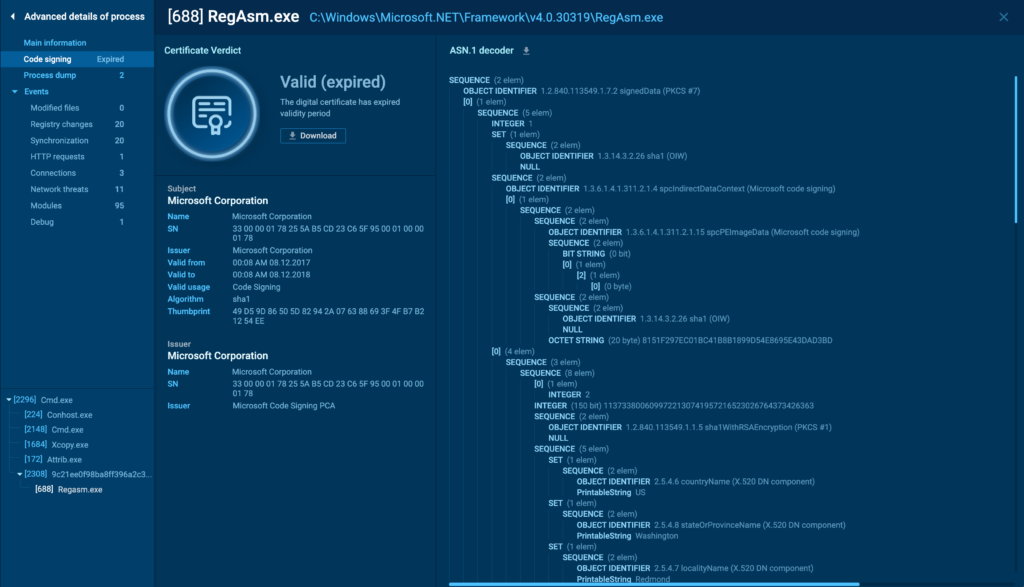
When using this tab, take care of verifying the legitimacy of the digital signature. A professional signature from a trusted issuer usually signifies that the tactic is protected. However, be cautious of expired or self-signed certificates, as these can be indicators of in all probability malicious train.
Course of Dump
The Course of Dump tab means you can acquire a full memory dump of the chosen course of. It’s a extremely efficient software program for in-depth forensic analysis. Memory dumps can comprise essential data, similar to encryption keys, passwords, and completely different delicate data that the tactic was coping with on the time of the dump.
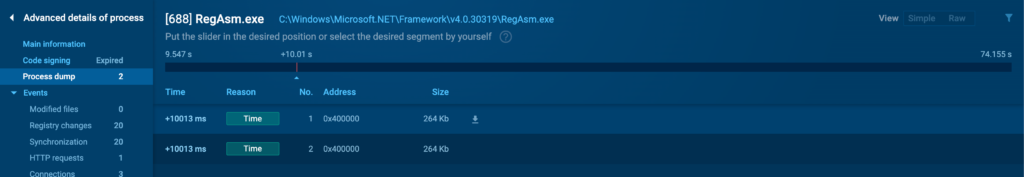
To acquire a dump, hower over it and click on on on the acquire icon which is ready to appear subsequent to the Dimension topic.
Script Tracer
If the malware or course of in question makes use of a scripting language, similar to PowerShell, JavaScript, or VBScript, you’ll discover a Script Tracer tab. It provides an in depth trace of the script execution, allowing you to see the exact directions and scripts being run by the tactic.
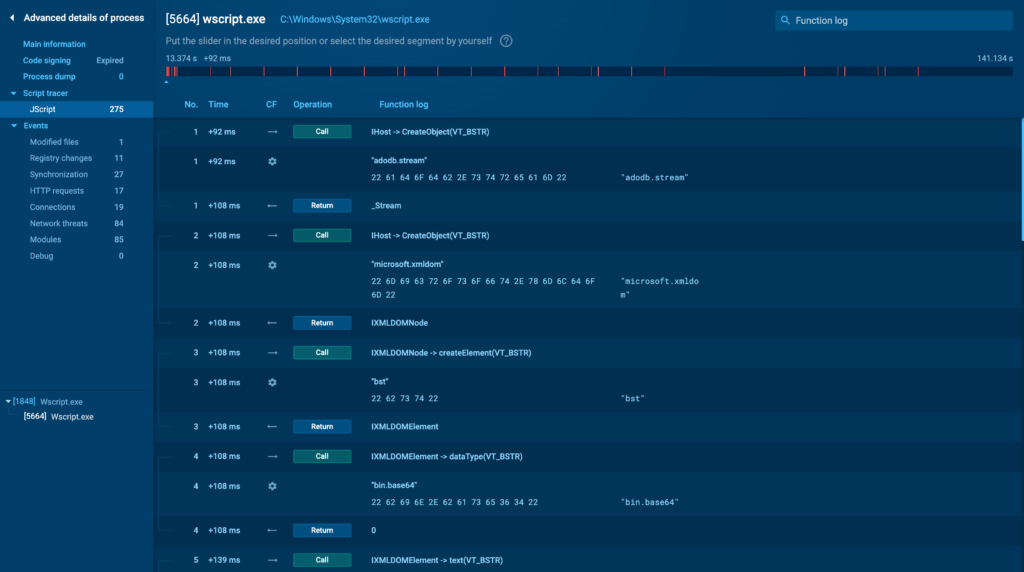
This tab is very useful when dealing with fileless malware or completely different threats that depend upon scripts to hold out malicious actions.
Subsequent, let’s check out the numerous events ANY.RUN captures all through analysis.
Modified Data
The Modified Data tab tracks all changes made to the file system by the tactic.
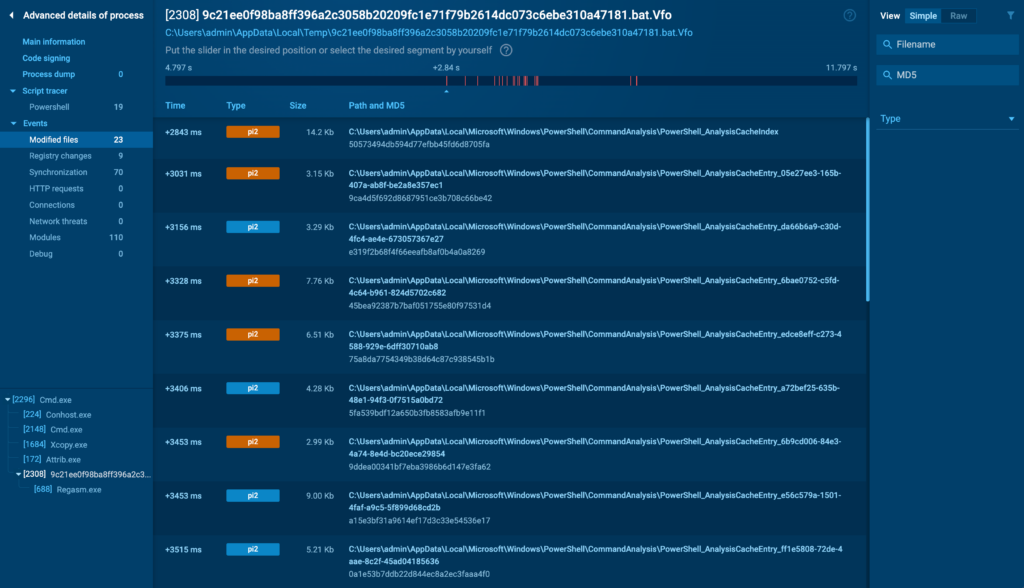
This comprises file creation, modification, and deletion events. For malware analysts, this tab is invaluable, because it might really quickly reveal if a course of is attempting to drop or modify data in delicate areas, similar to system directories or startup folders.
Registry Changes
The Registry Changes tab logs any modifications the tactic makes to the Dwelling home windows Registry. The registry is a typical objective for malware on the lookout for persistence, as it could be used to run malicious code on startup or alter system habits.
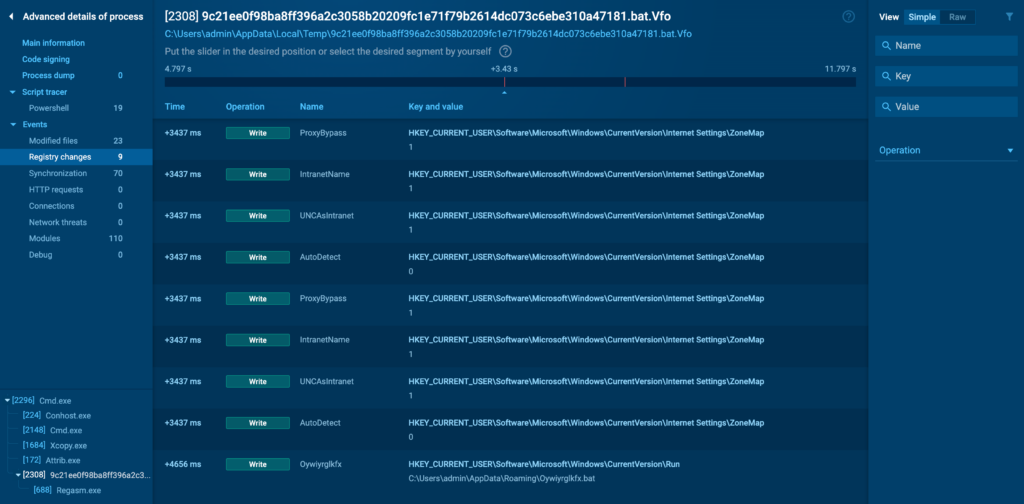
Key areas to look at embody startup entries, that are generally manipulated by malware to ensure it runs robotically after a reboot.
Synchronization
The Synchronization tab provides particulars on any synchronization events, similar to course of prepared events or alerts. These events can level out coordination between completely completely different processes or threads, which is a typical habits in refined malware.
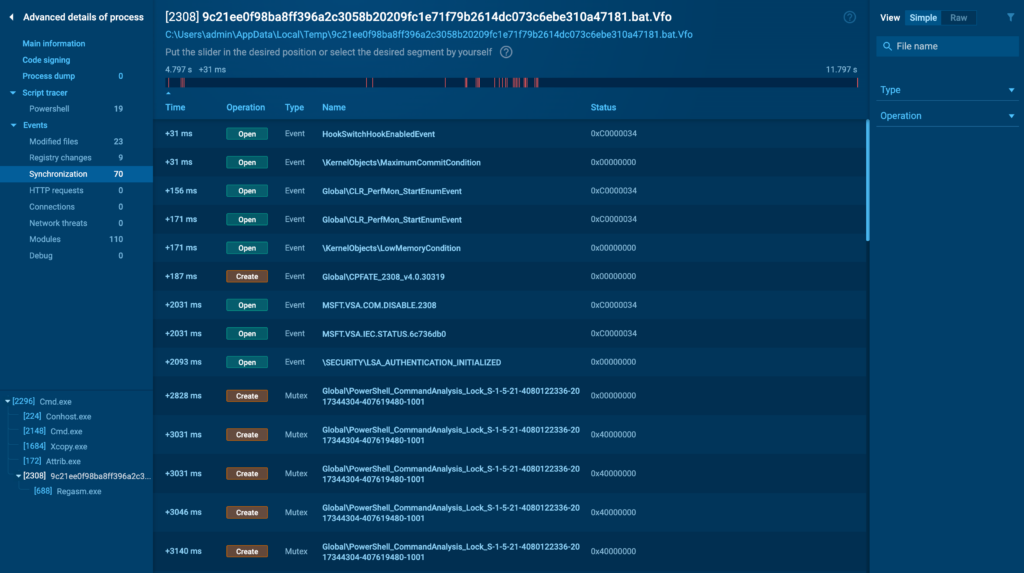
Whereas a lot much less frequent in elementary malware, synchronization events are further seemingly in superior threats the place plenty of components ought to work collectively seamlessly. Monitoring these events will assist set up sophisticated malware that is dependent upon inter-process communication.
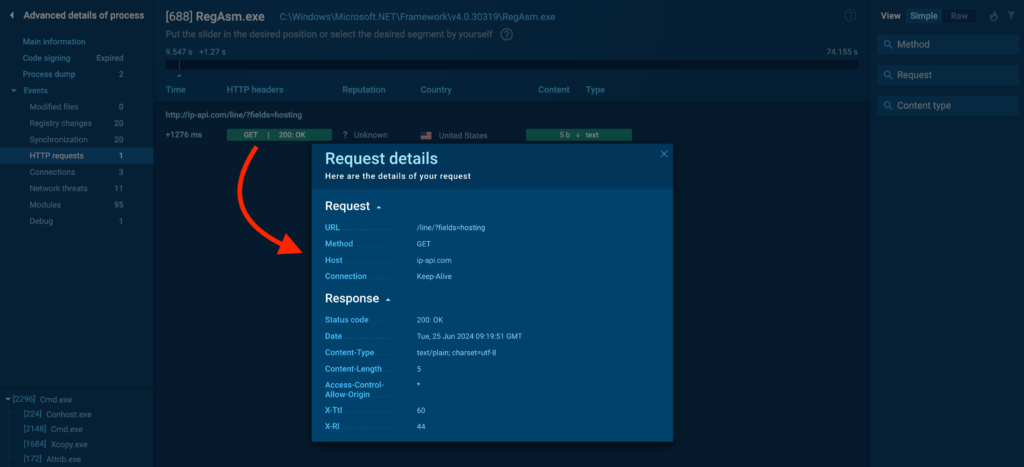
HTTP Requests
The HTTP Requests tab logs all HTTP requests made by the tactic. That’s essential for determining whether or not or not a course of is attempting to talk with a distant server, which is a typical habits in malware that exfiltrates data or receives directions from a C2 server.
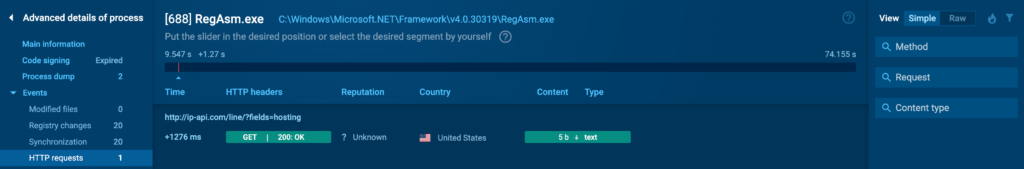
You probably can click on on on the colored buttons to entry further particulars about each request:
Connections
The Connections tab provides an in depth view of all group connections established by the tactic.
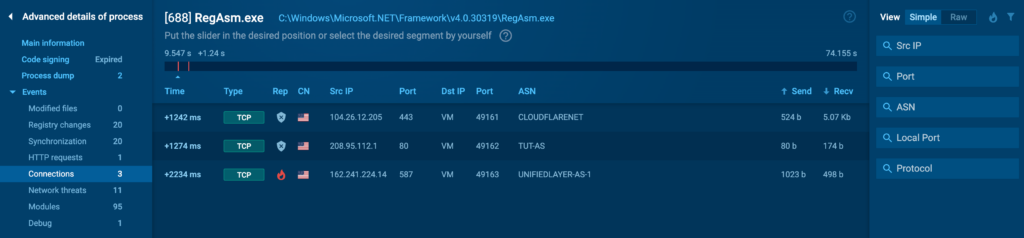
This comprises every incoming and outgoing connections, along with data similar to:
Group Threats
The Group Threats tab is dedicated to determining potential network-based threats associated to the tactic. It provides a high-level overview of any suspicious actions detected in the midst of the analysis, similar to makes an try to contact blacklisted IP addresses or domains. We use Suricata pointers to detect these threats.
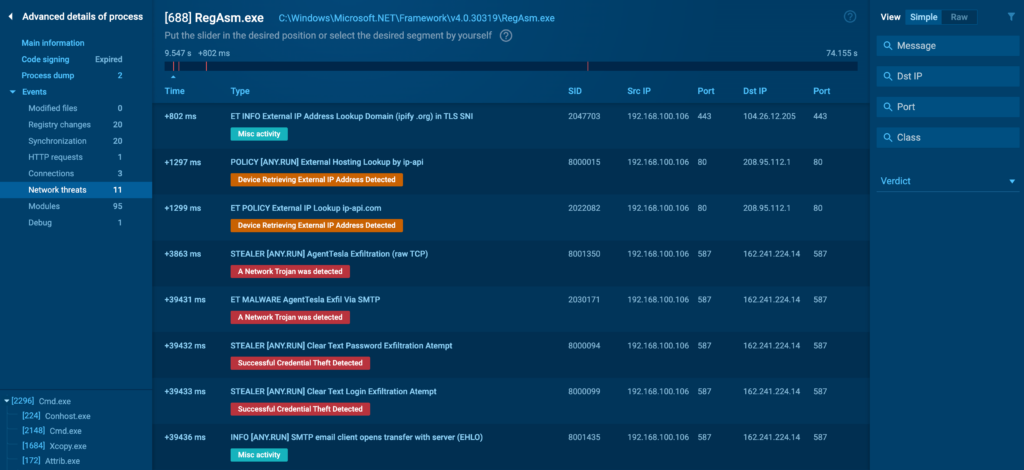
You probably can click on on on each acknowledged threat to view the whole Suricata rule that triggered the alert.
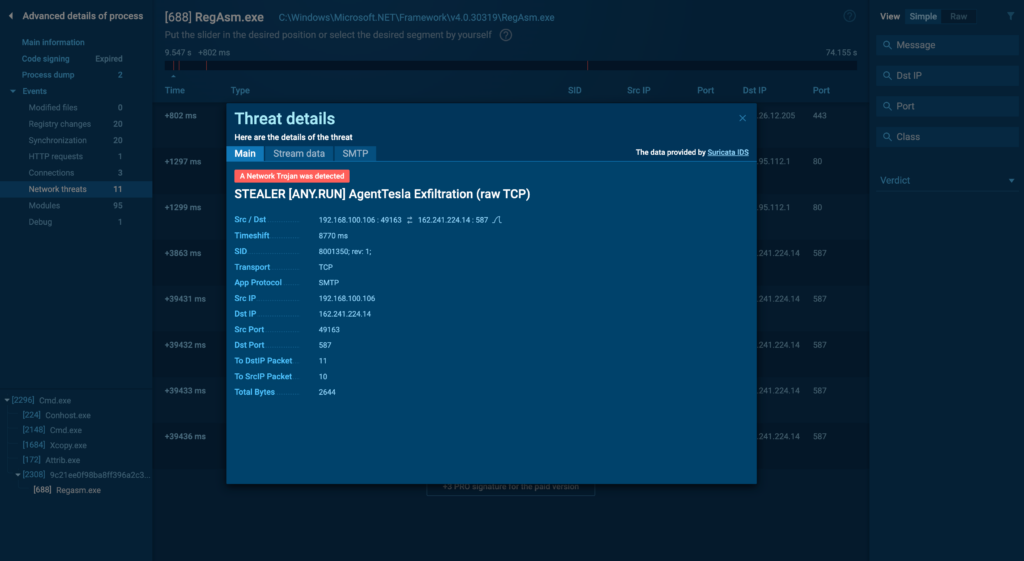
Whereas most of these pointers might be discovered with out spending a dime, some are distinctive to our paid subscribers. This allows for deeper insights into the detected threat, serving to you understand the actual group habits that was flagged.
Permit us to current you the best way ANY.RUN will assist your SOC group – information a reputation with us ⬇️
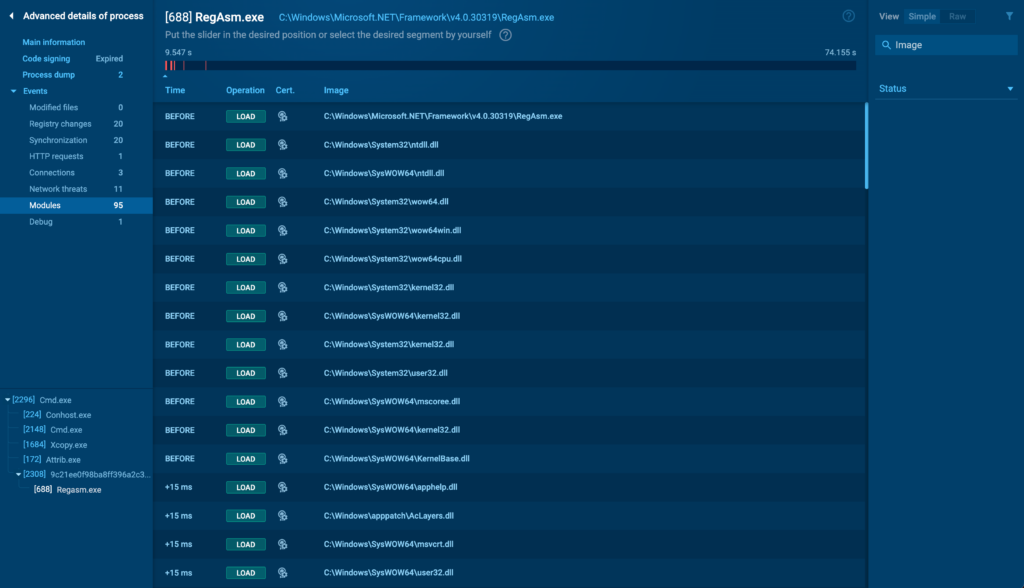
Modules
The Modules tab reveals all modules loaded by the tactic. Malware often makes use of module injection to cowl its presence or to leverage the capabilities of legit software program program components. This tab lists each module, along with its path and completely different associated particulars.
Debug
The Debug tab provides further data like exceptions, or completely different debugging data which will help in understanding sophisticated malware habits.
About ANY.RUN
ANY.RUN helps larger than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that concentrate on every Dwelling home windows and Linux strategies. Our threat intelligence merchandise, TI Lookup, Yara Search and Feeds, allow you uncover IOCs or data to review further regarding the threats and reply to incidents sooner.
With ANY.RUN you probably can:
- Detect malware in seconds.
- Work along with samples in precise time.
- Save time and cash on sandbox setup and maintenance
- Doc and analysis all sides of malware habits.
- Collaborate collectively together with your group
Request free trial →







