ANY.RUN TI Lookup: a Phishing Case Study

At ANY.RUN, we’ve these days launched our new Threat Intelligence Lookup service.
This system opens up unimaginable options for leveraging our intensive menace intelligence database additional efficiently. On this text, we aim to show how our superior search capabilities will allow you to reply to security incidents additional quickly and exactly.
On this text, we’re going to walk you through a sensible occasion of a phishing assault. Nevertheless sooner than we dive into the specifics, let’s quickly recap: what’s ANY.RUN Threat Intelligence Lookup and who’s that this service for?
What’s ANY.RUN Threat Intelligence Lookup?
ANY.RUN Threat Intelligence Lookup is a contextual search service accessible on-line and through an API. It actually works by indexing and analyzing information from tens of tens of millions of public interactive analysis durations, moreover known as merely “duties,” which our group of over 300,000 researchers and 300 enterprises runs inside the ANY.RUN sandbox.
The precept intention of this system is to help your security group be a part of an isolated indicator to a specific menace.
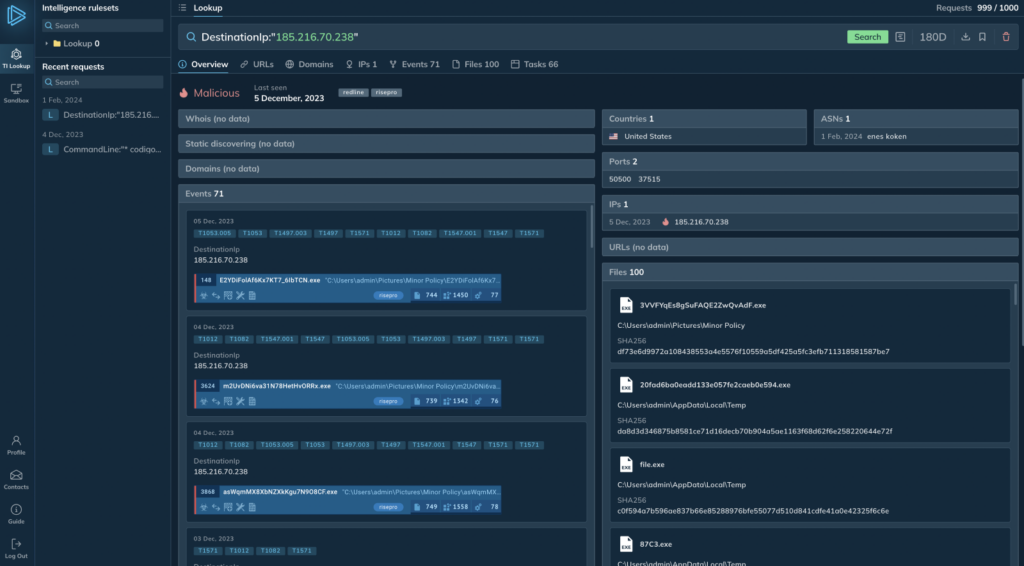
For example, do you have to spot an unfamiliar IP in your neighborhood logs, figuring out its nature might take a while. However, it’s likely that this IP has already been recorded in a sandbox exercise. By querying for this IP inside the Threat Intelligence Lookup, chances are you’ll quickly uncover linked analysis durations.
In a number of circumstances, that is adequate to ascertain the malware family by title. You’ll moreover get related particulars equal to ports, URLs, and file hashes inside the search outcomes.
In spite of everything, aside from IPs it’s best to use many alternative parameters to query our Threat Intelligence database. There are over 30 parameters in full that can allow you to assemble queries as giant or as explicit as you need. Listed beneath are a couple of of them:
- IOCs: file hashes, URLs
- Events: command line, registry path.
- Threat particulars: Suricata messages or Suricata id
- And loads of others
For a full guidelines of supported parameters, study our TI Lookup introduction publish.
Phishing assault: setting the stage for our case analysis
Let’s get once more to the case analysis and outline the scenario our security group is coping with.
(Discover: This case analysis is based on our real-world experience, however it does not replicate a specific assault on our purchasers or anyone else.)
The protection group acquired an alert from an employee a few doable phishing strive. The employee downloaded an Office attachment from an e-mail, and no matter observing odd habits, adopted instructions to permit Macros. In hindsight, it triggered an alarm, which led to the report.
Now, it’s as a lot as the security analysts to have a look at the employee’s workstation, which may have been compromised.
Step 1: Explaining a Suspicious Command Line
As commonplace in circumstances like this, let’s begin by inspecting the logs from the intrusion detection and response (IDR) system.
By going by these logs we come all through a highlighted PowerShell course of, with the time interval $code inside the command line.
The time interval $code seems unfamiliar, nonetheless what exactly may it is? An analyst lacking entry to Threat Intelligence Lookup might flip to a generic net search to answer this question, which could each be time-consuming, or unfruitful, or every.
Fortunately, now now we have a higher system at our disposal: Threat Intelligence Lookup.
By wanting with the query ImagePath:”powershell” AND CommandLine:”$codigo”as a result of the video above reveals, we uncover fairly a couple of command strains from duties containing the $code key phrase. By exploring the Events tabwe get a additional detailed view of these command strains and see that some duties are tagged with “stegocampaign.”
This implies the workstation might have been compromised by a cyberattack. However, we would like additional detailed information to ascertain the exact malware family involved.
Step 2: Determining the Malware Family
We’re making progress nonetheless must refine our search. One different hint from the IDR logs is that the suspected contaminated machine associated to port 2404, which isn’t normally utilized in our neighborhood infrastructure.
To incorporate this new information, we’ll regulate our query as follows: ImagePath:”powershell” AND CommandLine:”$codigo” AND DestinationPort:”2404″.
As a result of the video above reveals, this updated search gives us fewer duties nonetheless most of them are clearly linked to the Remcos malware family. Remcos, a well-known Distant Entry Trojan and it usually makes use of PowerShell, which matches the indicators we found earlier.
Threat Intelligence Lookup moreover reveals malicious IP addresses which have been discovered inside the duties. We’re in a position to make use of these IPs to research further and better understand the malware’s habits.
Step 3: Using IP cope with to research Remcos
To substantiate that we’re dealing with Remcos, we’ll write a query that merges a neighborhood rule title with the IP cope with linked to port 2404. Moreover, we’ll refine our search to point solely duties from the ultimate 7 days. It will appear as if this: RuleName:”remcos” AND DestinationIp:”107.172.31.178″
The query returns one exercise linked to the specified IP tagged with Remcos. At this degree, we’re capable of conclusively set up Remcos as a result of the malware on the contaminated workstation.
Nevertheless let’s not stop proper right here. By opening this sandbox exercise we’re capable of dissect all malicious TTPs associated to Remcos, utilizing ANY.RUN’s MITRE ATT&CK Matrix. We’re capable of moreover take a look at the details of malicious processes initiated by the malware.
We’re capable of then purchase IOCs supplied by the sandbox, with selections to acquire a report in HTML or JSON codecs to configure firewalls, SIEM and SOAR strategies in opposition to this Remcos variant.
This illustrates merely certainly one of many some methods ANY.RUN’s Threat Intelligence Lookup is normally a important asset for cybersecurity analysts.
In the event you want the ultimate phrase revenue, consider using ANY.RUN sandbox and Threat Intelligence Lookup collectively.
We’re moreover offering a trial with 20 search queries for current ANY.RUN purchasers, who’ve purchased Searcher plan or above. Attain out to our product sales group to attain entry to the trial, uncover out additional regarding the platform, or give attention to pricing selections.
Сontact product sales →





