How to Analyze Malware in ANY.RUN Sandbox: Eric Parker’s Guide

Not too way back, Eric Parkera cybersecurity skilled and YouTuber, launched a new video on ANY.RUN’s interactive sandbox. We advocate you take a look at his tutorial, as a result of it affords a step-by-step info on how one can use the service and save time on reverse engineering.
Proper right here’s our overview of the necessary factor highlights from the video.
About malware analysis in a sandbox
Sandboxing is a crucial course of in cybersecurity that lets professionals analyze malware in a managed environment. Sandboxes current a protected home so as to add and have a look at most likely malicious samples with out compromising your exact system.
ANY.RUN’s sandbox affords interactive analysis, providing prospects with a real-time view of how malware behaves and allowing them to interact with the system and samples an identical to on a traditional laptop.
Organising a sandbox environment
Eric began by highlighting various settings of ANY.RUN which may be adjusted for numerous eventualities, along with:
MITM Proxy: This setting is very useful for intercepting and analyzing group web site guests, resembling HTTP requests made by the malware. This allows you to observe how the malware communicates with command and administration (C2) servers and accumulate further detailed particulars about its actions.
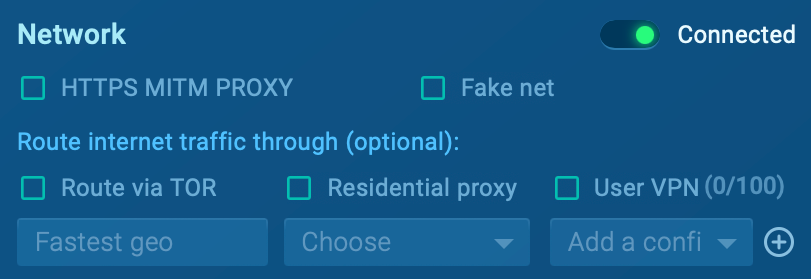
FakeNet: This function is environment friendly in case you’re fearful about malware with worm-like capabilities, allowing detection of group shares or interactions with non-functional command and administration servers.
Examine further about MITM proxy and FakeNet
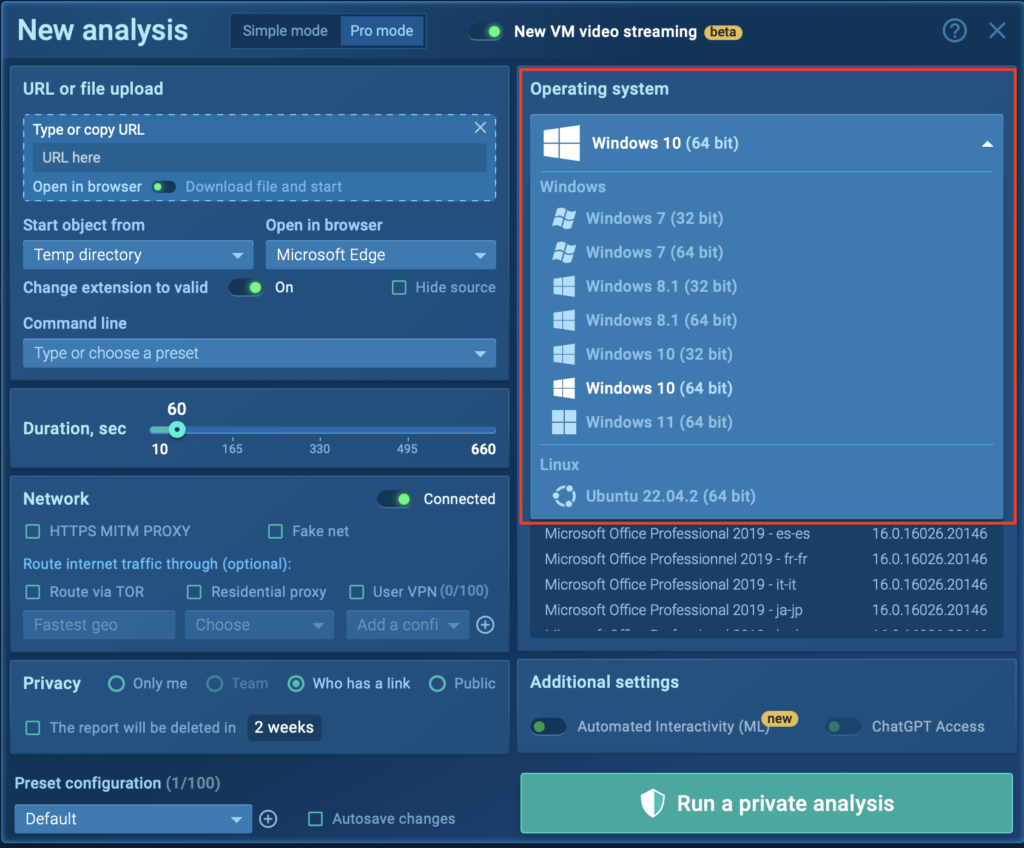
Working System Customization: ANY.RUN affords a variety of OS decisions, from older variations of Residence home windows (7/32-bit, 7/64-bit) to the latest Residence home windows 11. Linux prospects may even run samples for cross-platform analysis.
For legacy malware, using an older OS is maybe compulsory for full compatibility. Eric recommends experimenting with fully totally different OS decisions based totally on the malware sample.
Pre-installed tender set: Chances are you’ll choose pre-installed software program program models, resembling Office or Fullto simulate real-world environments, making the analysis further life like. Clients may even add their very personal devices to the digital machine for quick entry in the midst of the investigation.
Privateness Settings: Chances are you’ll choose whether or not or not your analysis outcomes are public or private. Within the occasion you’re working with delicate malware samples that may comprise proprietary information, this attribute ensures confidentiality.
Interval Administration: For malware that delays execution (e.g., with sleep capabilities), you probably can lengthen the sandbox runtime to grab the entire scope of its habits.
Sandbox analysis of Zombie malware
Inside the video demonstration, Eric used a sample he suspected of being malware. ANY.RUN’s sandbox quickly acknowledged warning indicators, detecting file replacements and irregular behaviors indicative of malware an an infection.
Key components throughout the analysis:
- File overwriting: The malware modified info with an executable payload. Inside the occasion, the malicious EXE was found to overwrite skilled system info and create fairly a couple of short-term info.
- File dumping: One among ANY.RUN’s most helpful choices was the pliability to dump info mid-execution, making it less complicated to research malware that makes use of packing or encryption to cover its malicious actions.
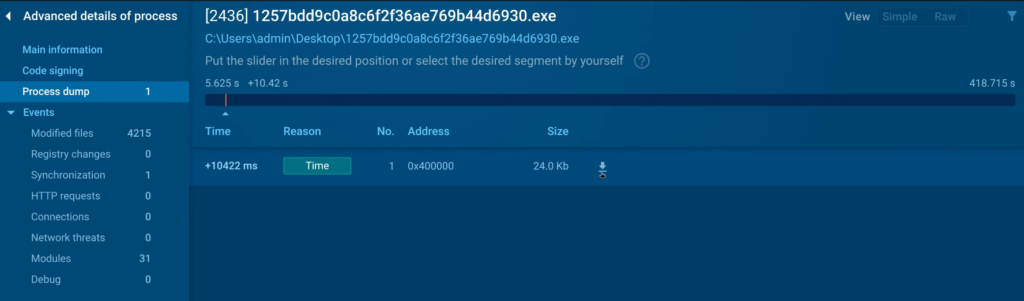
- Executable identification: Importing the file to the sandbox made it potential to instantly set up it as malicious and belonging to the Zombie malware family.
Analysis of Pysilon Discord RAT
Eric emphasised that the aim of any malware analyst is to not understand every line of code, nonetheless to get a terrific view of how this method interacts with the system. That’s the place an interactive sandbox can present terribly helpful.
By working the malware in a digital environment, analysts can quickly understand its habits with out delving into superior reverse engineering.
In numerous cases, dynamic analysis alone can current all of the obligatory information, bypassing the need for a full static analysis. Eric confirmed this by working a Pysilon Discord RAT sample throughout the sandbox.
Pysilon is a malware that is usually packed in a novel method, making static analysis harder. To avoid dealing with the packer, Eric merely enabled the MITM proxy in ANY.RUNwhich allowed him to amass the malware’s Discord bot token in a few seconds.
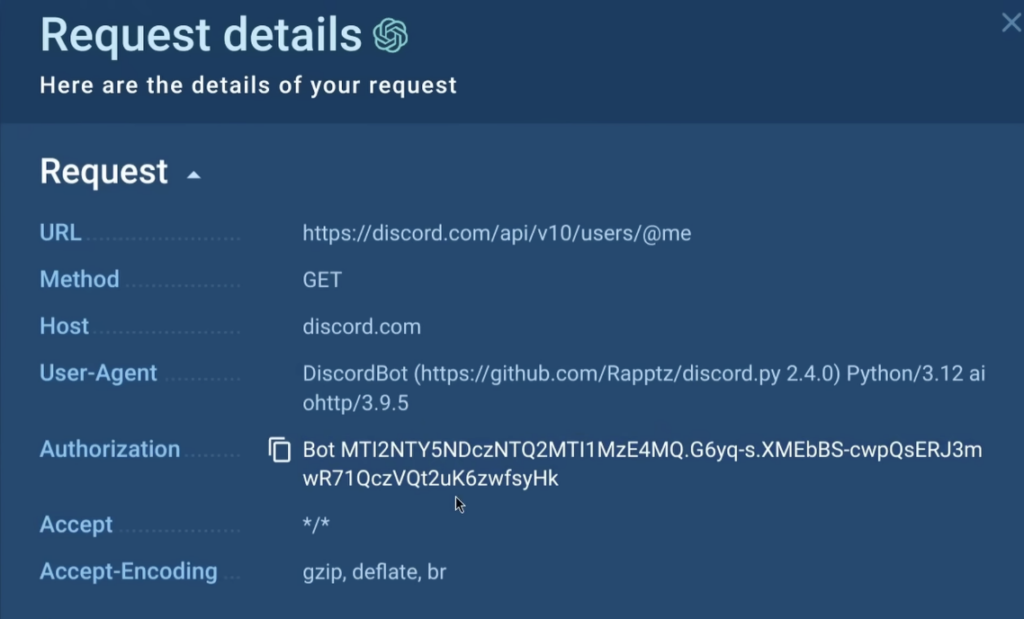
ANY.RUN moreover acknowledged a newly spawned executable named “driveinst.exe” which mimicked knowledgeable course of. This executable was flagged as unsigned, elevating a crimson flag.
ANY.RUN robotically categorized the malware as a stealerhighlighting its malicious actions and group communications.
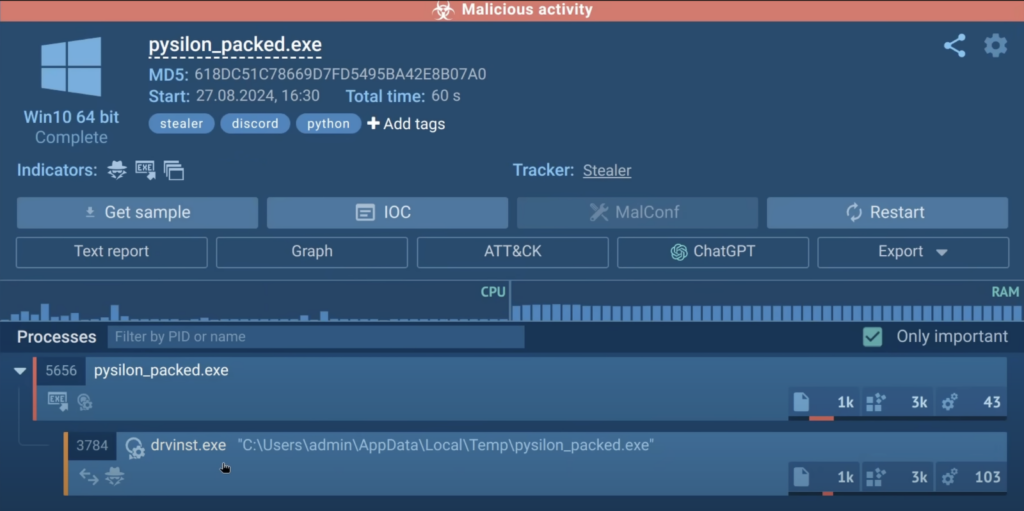
Due to this, the bot token was captured, the malware’s habits was seen, and the analysis was completed in decrease than 30 seconds.
Conclusion
Sandboxes, as demonstrated by Eric Parker, are a robust software program throughout the battle in direction of malware. Sandbox analysis allowed Eric to extract important information inside minutes, chopping down the time needed for handbook reverse engineering.
The sandbox supplied dwell info on group web site guests, file manipulation, and system changes, delivering quick recommendations on malware habits.
Eric was able to avoid the need to manually unpack or decrypt info, streamlining the analysis course of.
To see full potential of ANY.RUN’s sandbox, request a 14-day free trial →
About ANY.RUN
ANY.RUN helps higher than 400,000 cybersecurity professionals worldwide. Our interactive sandbox simplifies malware analysis of threats that concentrate on every Residence home windows and Linux strategies. Our threat intelligence merchandise, TI Lookup, YARA Search and Feeds, mean you can uncover IOCs or info to check further regarding the threats and reply to incidents faster.




